If you’ve been jailbreaking iPhones or iPads for any number of years, then you should be at least somewhat familiar with Filza, which is perhaps the most popular file manager app available today.
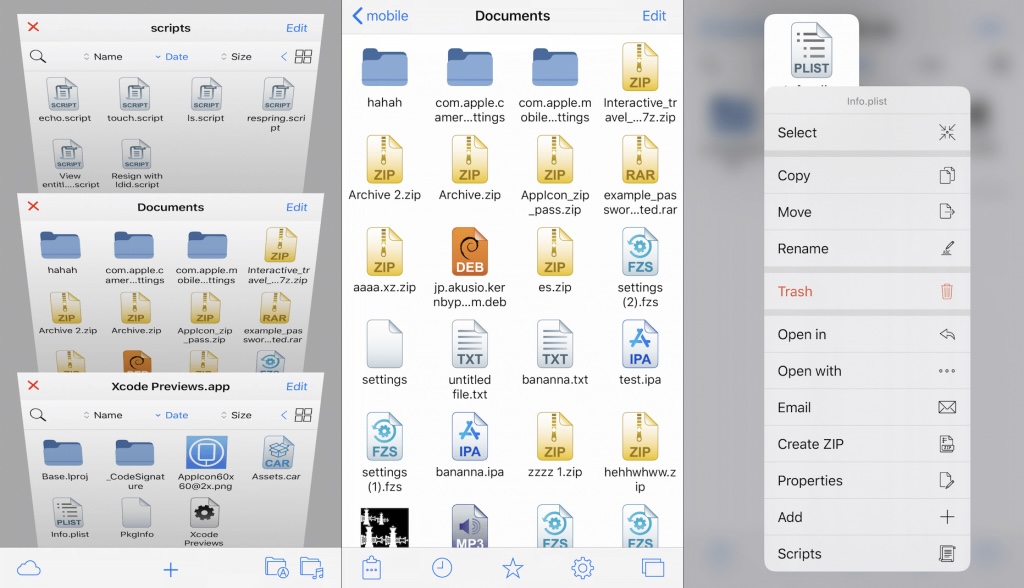
If you’ve been jailbreaking iPhones or iPads for any number of years, then you should be at least somewhat familiar with Filza, which is perhaps the most popular file manager app available today.

Shortly after the unveiling of the brand-new cicuta_verosa kernel exploit for all devices running up to and including iOS 14.3, renowned jailbreak developers and hackers began investigating its viability.
While much of the initial spotlight shined on Odyssey lead developer CoolStar to create an iOS 14-compatible jailbreak with the novel cicuta_verosa exploit, it seems that even Brandon Plank, another name that resonates positively with the jailbreak community, will be going hands-on with it.
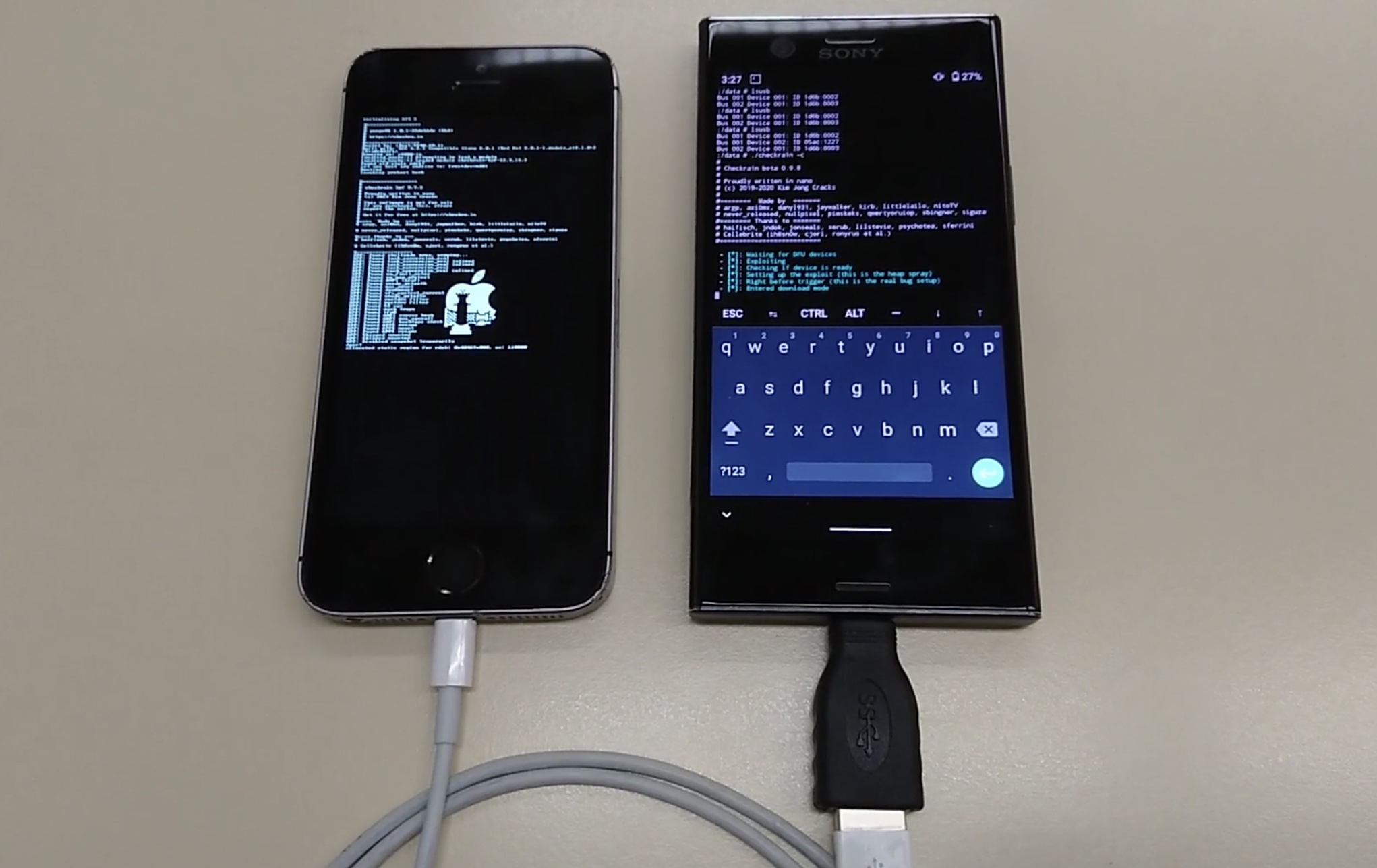
The bootrom exploit-based checkra1n jailbreak initially started out as a macOS-only utility for pwning compatible iOS devices, but it soon picked up official Linux support in a later update.
While the circumstances still aren’t ideal for Windows users, it is both possible and somewhat easy to dual-boot Linux on a Windows PC. But that may not be entirely necessary if you have certain Android devices laying around…
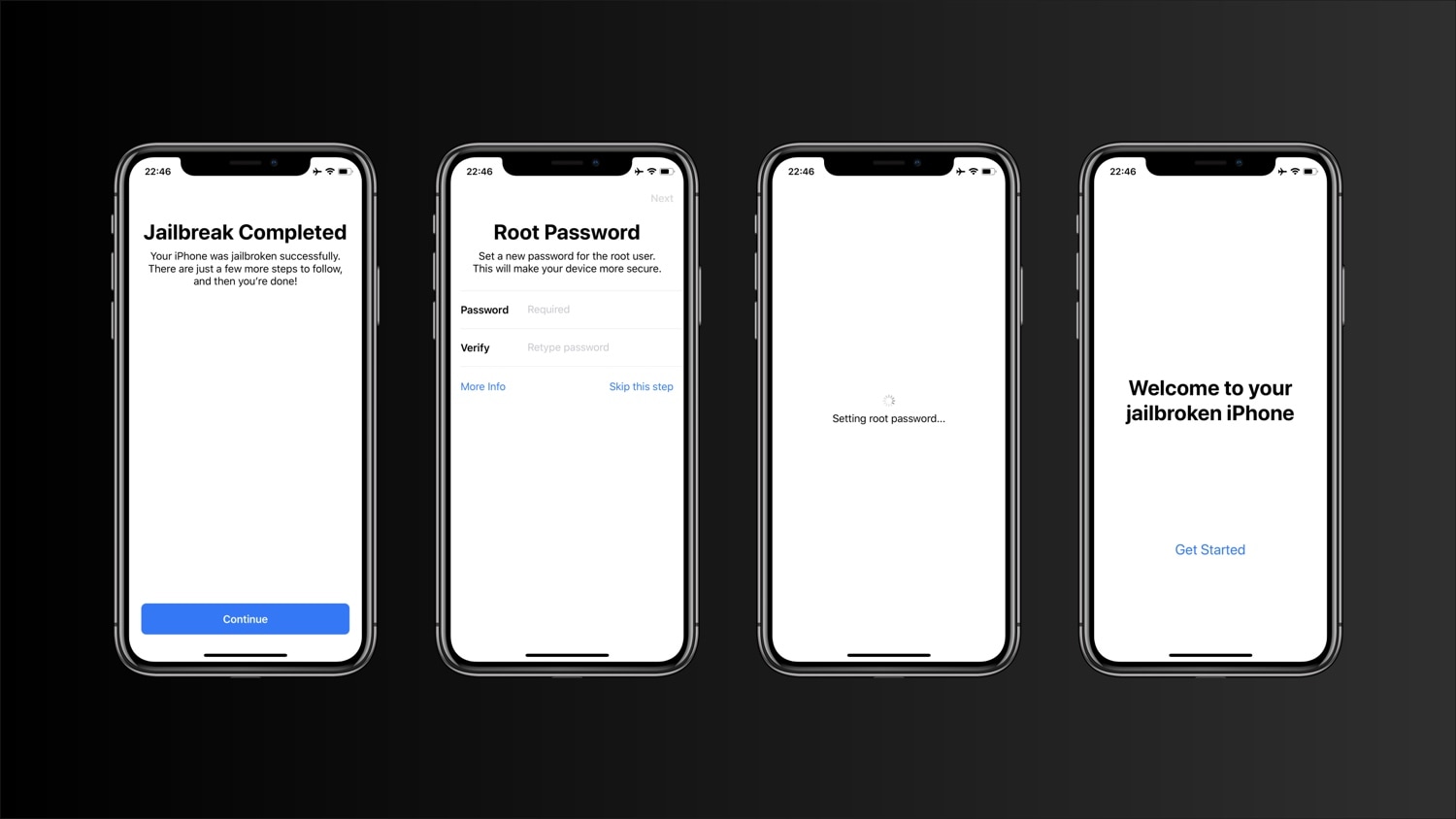
Anytime you jailbreak an iOS device, one of the first things you’re ever advised to do is change your handset’s root password, which is commonly used to access elevated privileges in mobile terminal when entering complex commands. The password is always “alpine” out of the box, but users can change this to almost anything they want to increase their handset's security from a commonly-known password.
As imperative as changing the root password may be, many jailbreakers either forget to do so or shrug off its importance. For that reason, we’re particularly fond of a sleek concept that was shared to /r/jailbreak over the weekend that rethinks the way jailbreakers will interact with their root password after jailbreaking their handset for the first time.

This tutorial shows you how to enable root user on your Mac, log in to it, use it, change its password, and finally disable it.

Hacker and unc0ver lead developer Pwn20wnd hasn’t made any significant revisions to the unc0ver v3.0.0 pre-release for a few days now, and as you might come to expect, that’s because he’s been busy attempting to pwn A12(X) devices.
If you fall under the category of ‘currently waiting for A12(X) support,’ then you’ll be excited to hear that Pwn20wnd has made some progress. A Tweet shared Monday afternoon reveals that the hacker has officially achieved a rootfs remount with read and write privileges on his A12 test device:
Hacker and unc0ver lead developer Pwn20wnd appears to have been busy this weekend, revising the unc0ver v3.0.0 pre-release jailbreak tool at least five more times since Saturday afternoon. Betas 22-26 include the brand-new rootfs remount that surfaced yesterday afternoon compliments of hacker and software tinkerer @MiscMisty.
Pwn20wnd took to Twitter this morning to announce the bulk of those revisions and elucidate what they represent:

As expected, a sixth beta of macOS High Sierra 10.13.2 that was seeded today packs in a fix for the dangerous root password vulnerability that yesterday's emergency update has already patched on Mac computers running the commercial macOS High Sierra 10.13.1 version.
Apple on Wednesday issued a critical patch for macOS High Sierra to fix a major vulnerability discovered yesterday which allowed unrestricted access with full administrative privileges on Macs with a Guest account enabled or the root account's password left blank.
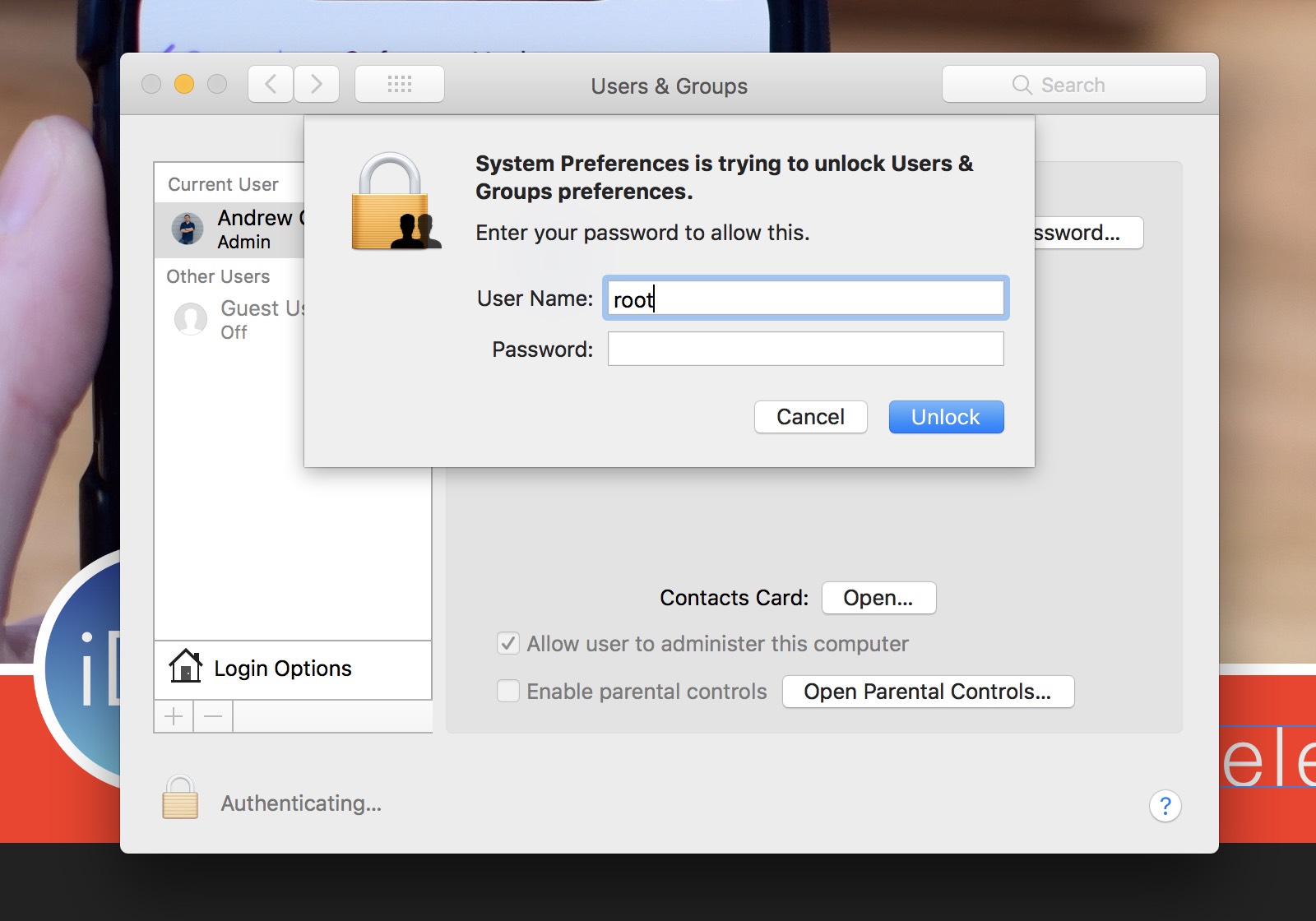
A potentially serious bug has been discovered by developer Lemi Orhan Ergin that allows anyone to gain root access to your machine by attempting to login with the username "root" and leaving the password blank. The vulnerability can easily be replicated, but fortunately, there is a simple workaround to fix the problem on your Mac until Apple releases a patch.
All Macs with OS X El Capitan installed on them have a new layer of security known as System Integrity Protection, which has been given the nickname 'Rootless' because it closes off a lot of system files to user access to prevent malicious programs and code from causing harmful changes to the core of OS X.
For some, the added security feels like a must for protection of your personal information, but for more advanced users who poke their noses into system files quite often, the feature can get in the way and prevent user modifications to the operating system. In this tutorial, we'll give you an overview of System Integrity Protection and show you a way to disable it.