It was only earlier in the day that we reported on the Misaka v8.2.0 update that added official support for arm64 devices in addition to every unsupported firmware combination for arm64e devices. But it seems that project lead developer @straight_tamago wasn’t finished yet.
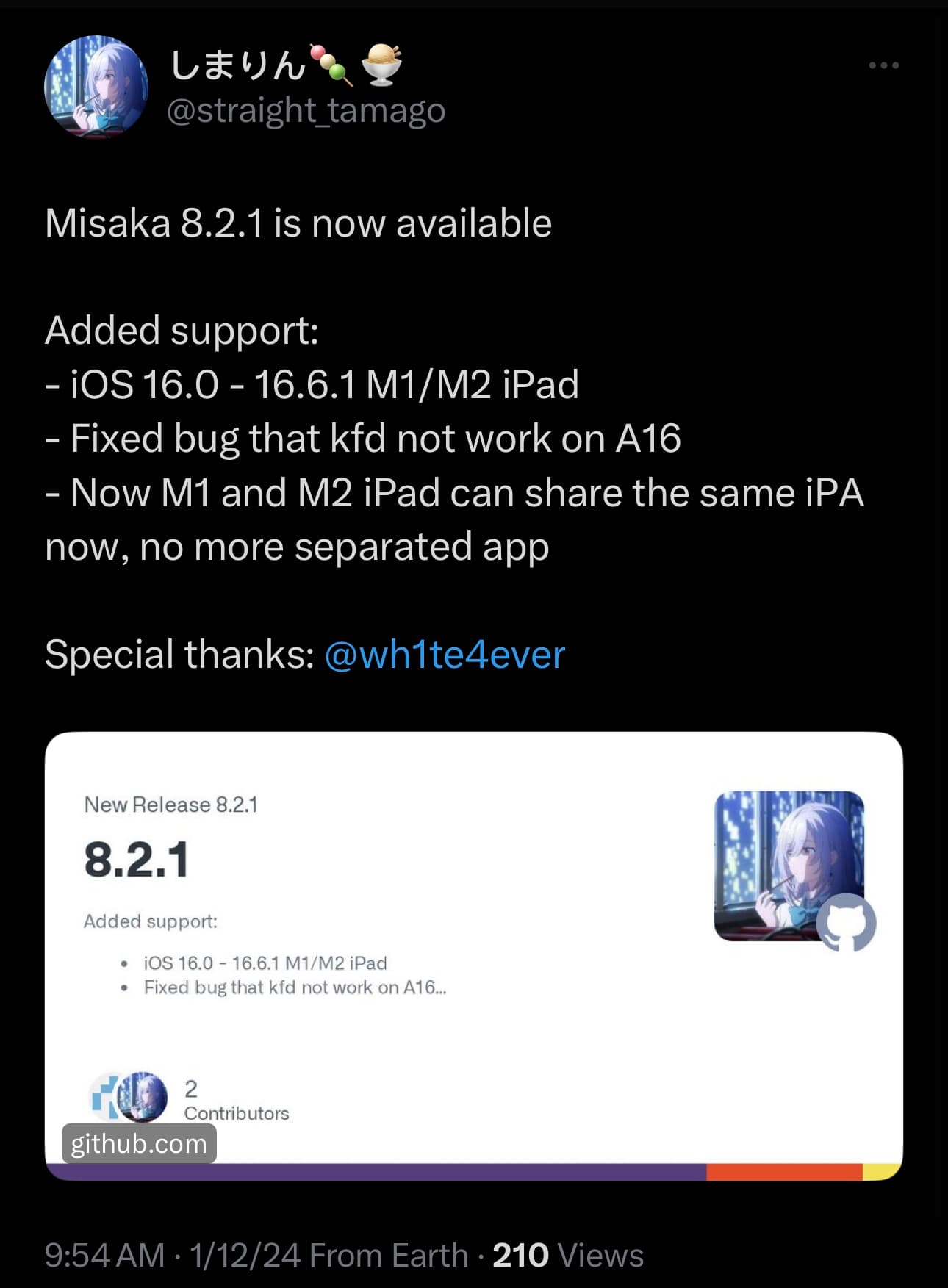
Early Friday morning, the developer took to X (formerly Twitter) to announce another important update to Misaka, this time bringing the project up to version 8.2.1, and from what we can gather, it brings the following changes:
– Add support for iPadOS 16.0-16.6.1 on M1 and M2 chip-equipped iPads
– Fix a bug that prevented the kernel file descriptor (kfd) exploit from working on A16 chip-equipped devices
– M1 and M2 chip-equipped iPads can now share the same Misaka .ipa file as ordinary iPhones and iPads instead of there being a separate app
This is a major update to Misaka because it brings the M1 and M2 chip-equipped iPads in-line with the same app as regular iPhone and iPad users. Before today, these have always been separate .ipa file builds.
The support includes the latest-supported kfd firmware with puaf_landa, from 16.0 to 16.6.1.
Moreover, iPhone and iPad users who have the A16 chip may have noticed that the kfd exploit wasn’t quite as reliable as it was supposed to be. This is now fixed.
If you’re an existing Misaka user, then you can safely install the latest build over your existing installation. You can do this with sideloading via AltStore or Sideloadly, or with perma-signing by way of TrollStore. We recommend the latter.
New or prospective Misaka users should get started by using the latest version available on the project’s GitHub page. Once downloaded, you can follow one of the tutorials we have below to get it installed on a compatible device:
- How to install the Misaka package manager with TrollStore
- How to install the Misaka package manager with Sideloadly
If you’ve never heard of or used Misaka before, it’s essentially a package manager app for non-jailbroken devices that lets you install hacks and add-ons that work with devices susceptible to both the MacDirtyCow exploit (for iOS & iPadOS 15.0-16.1.2) and the kfd exploit (for iOS & iPadOS 16.0-16.6.1). It can also be used to install TrollStore on kfd-vulnerable devices.
Are you running the latest version of Misaka yet? Let us know in the comments section down below.