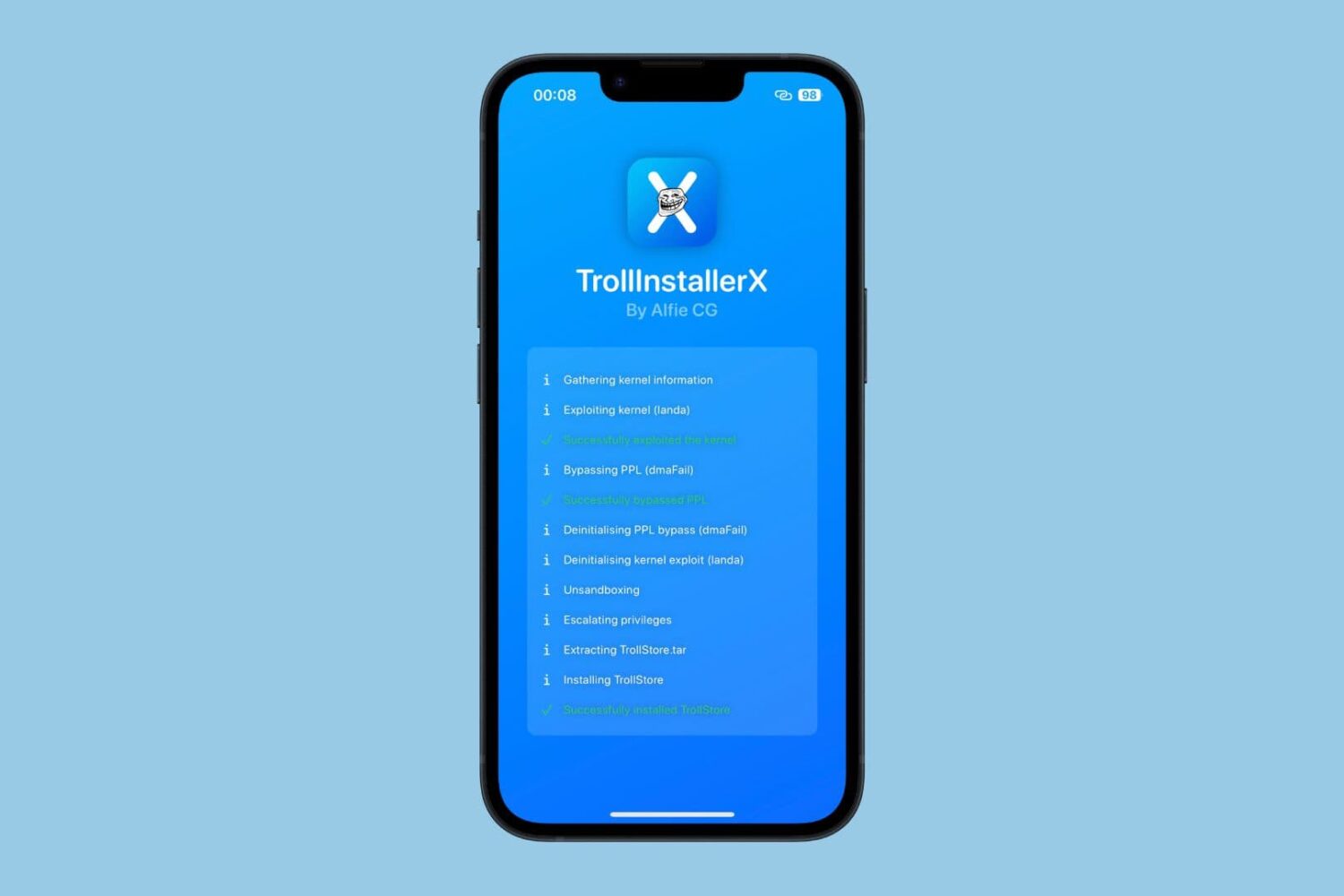
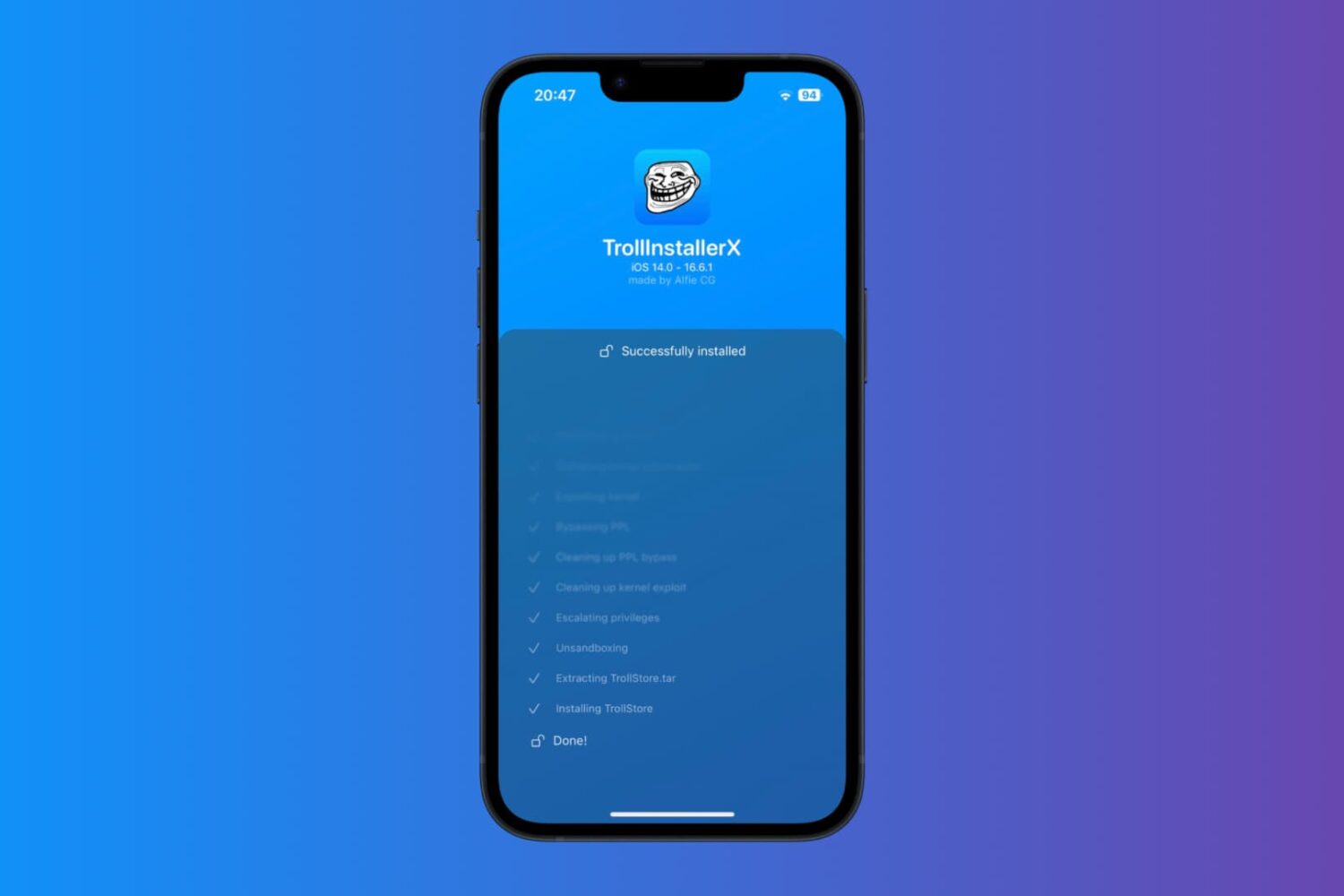
As promised back in February, Dopamine and TrollStore lead developer Lars Fröder (@opa334dev) took the stage at Zer0con 2024, a high-level and closed conference about software security, to discuss a technical deep dive about jailbreaking iOS 16.
Dopamine jailbreak developer Lars Fröder presents at Zer0con 2024