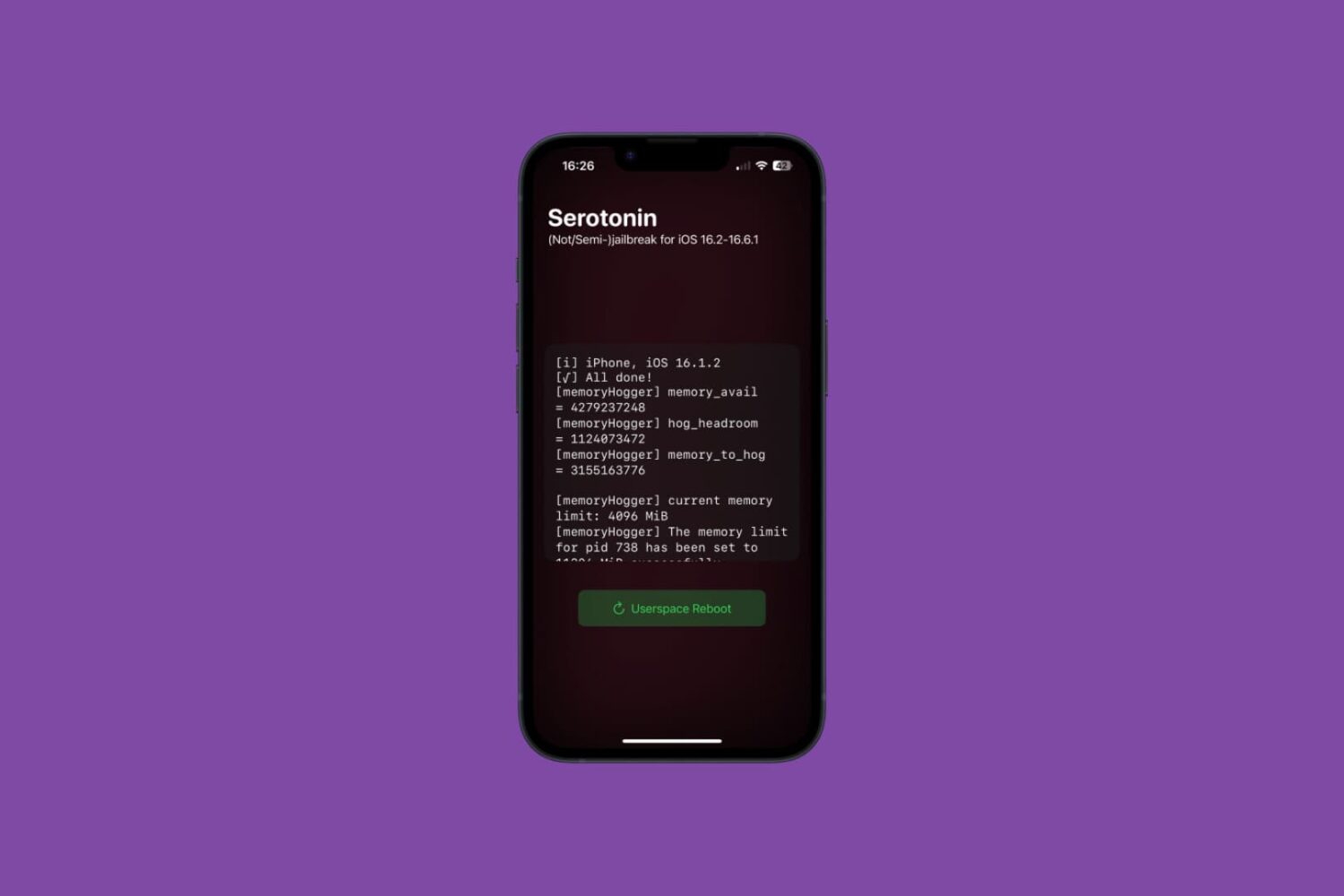
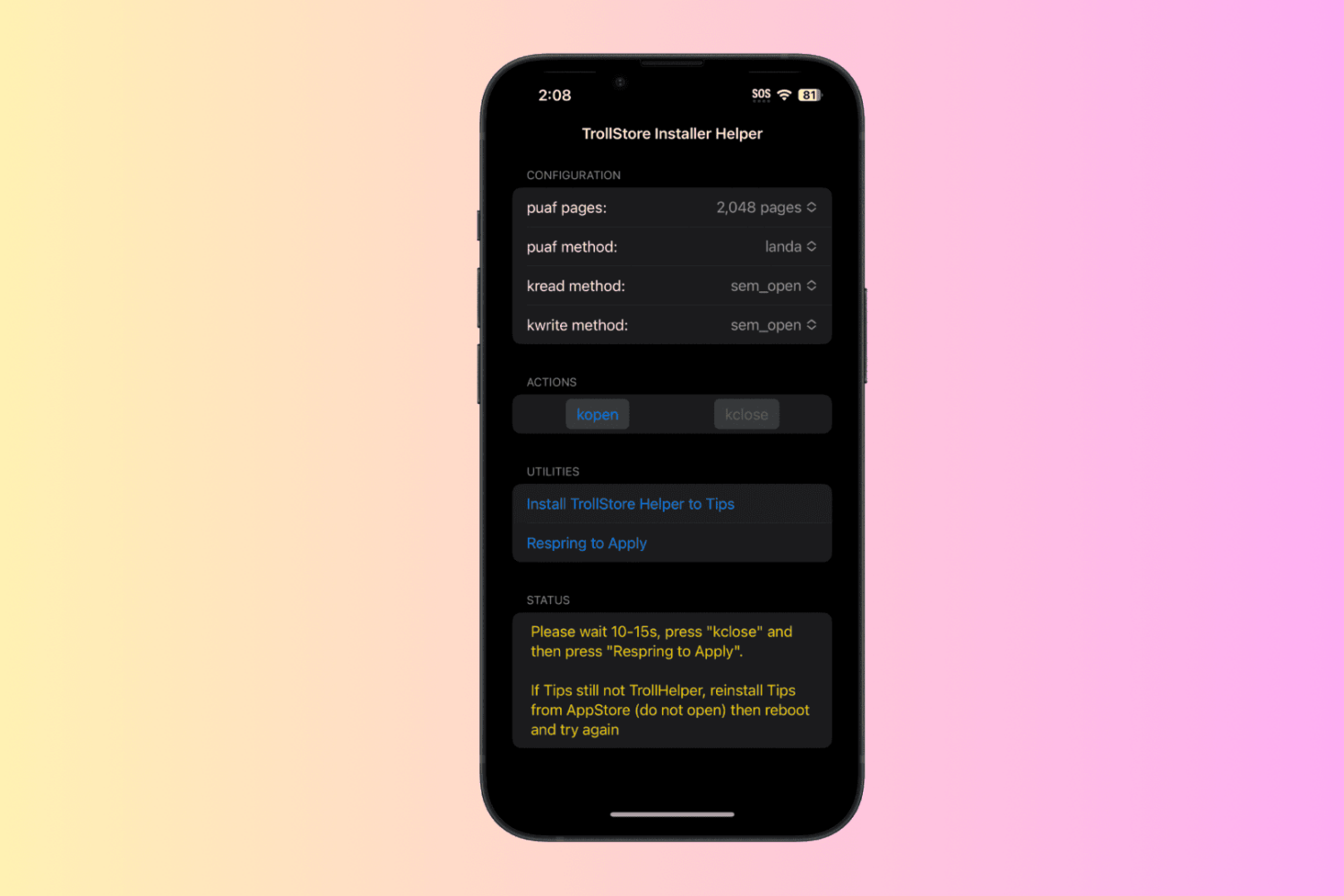
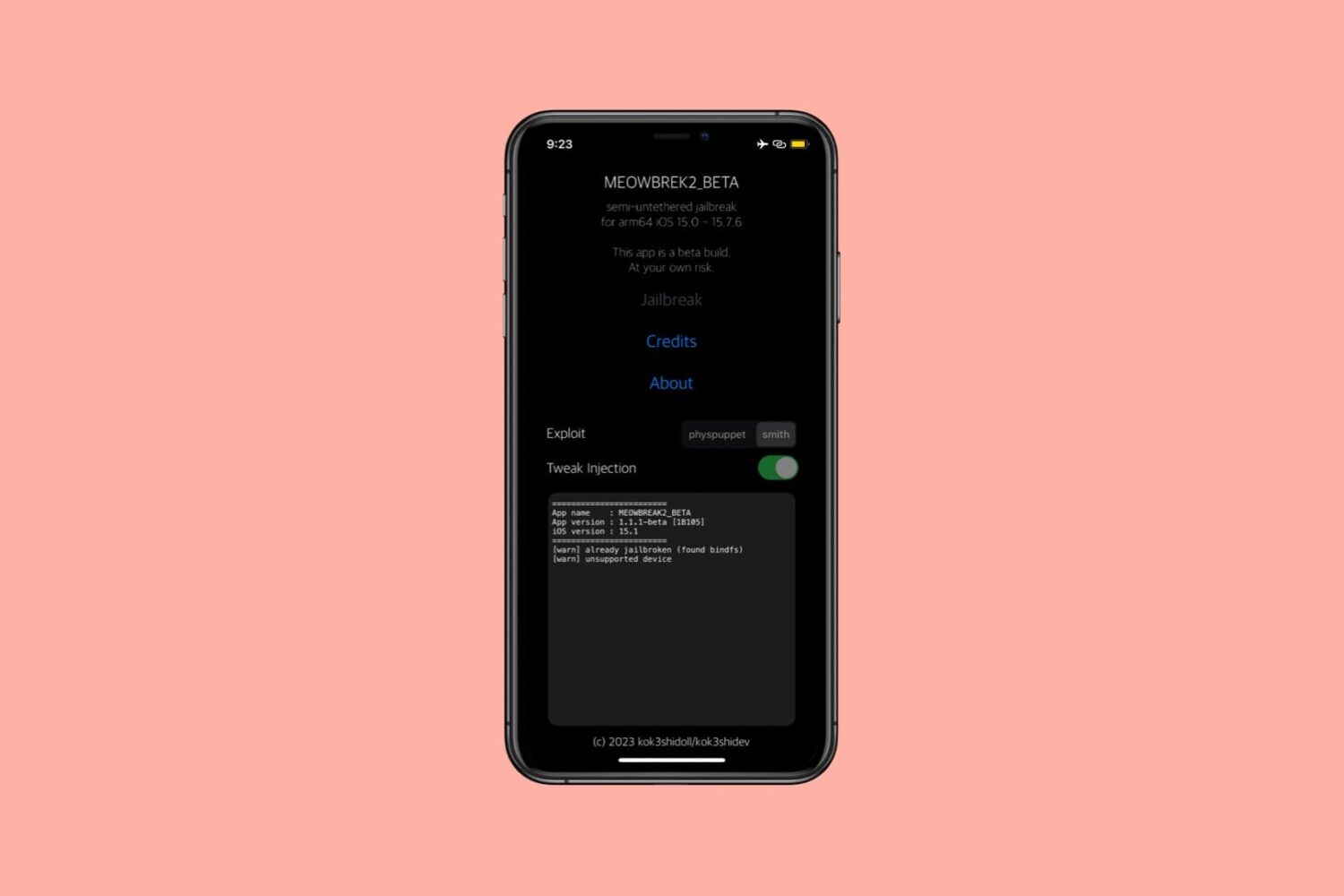
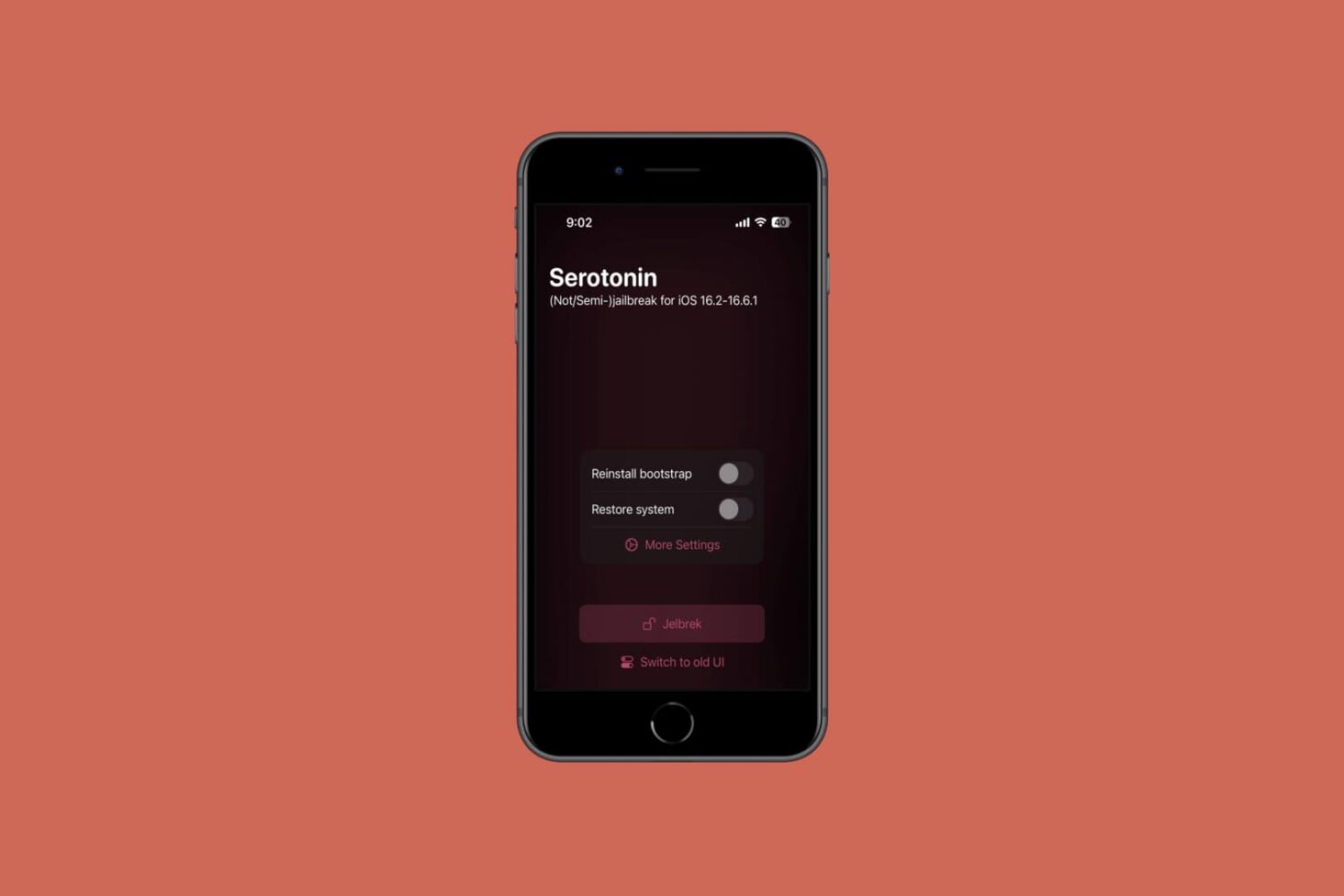
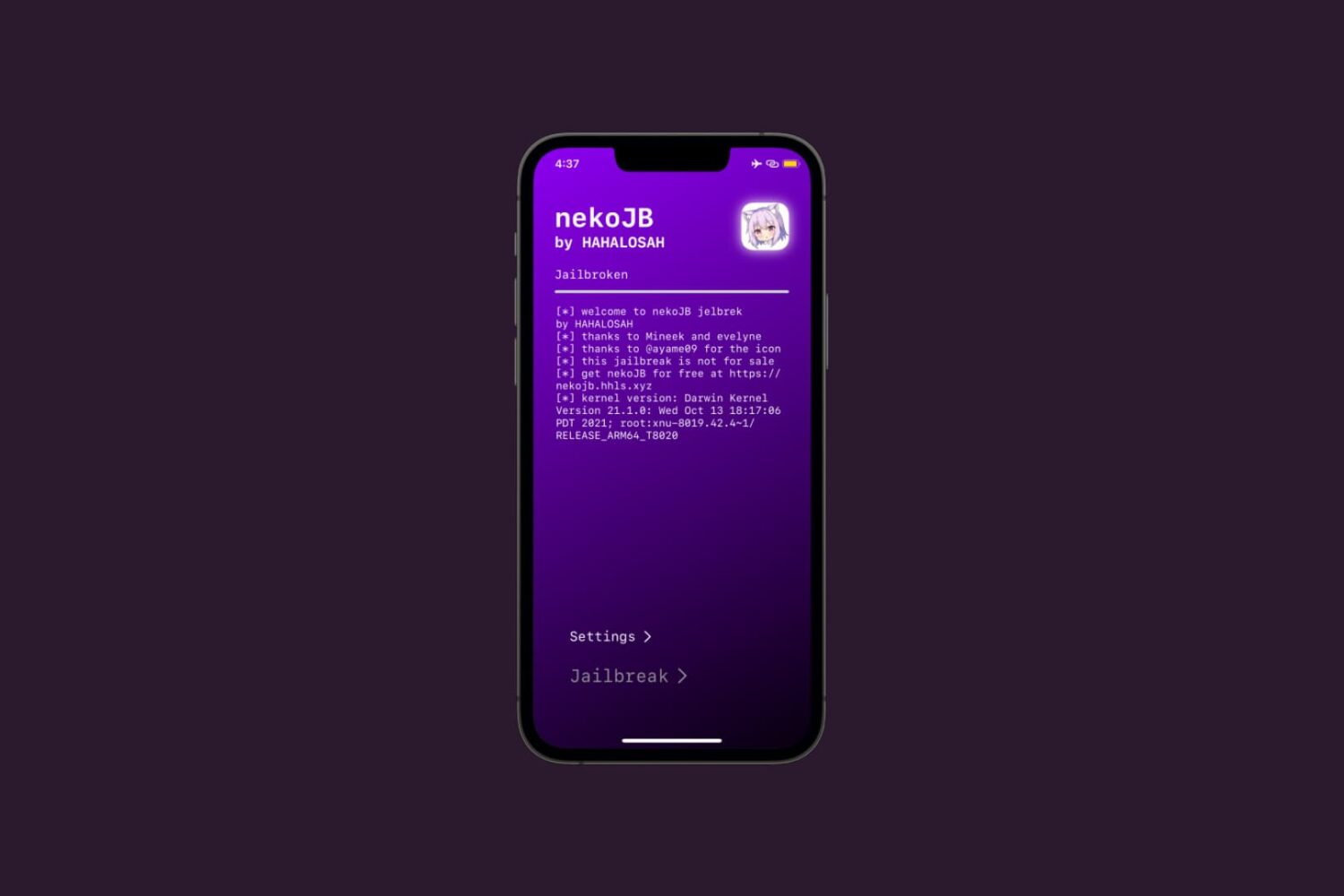
TrollStore, a perma-signing utility for iPhones and iPads that harnesses a CoreTrust exploit in iOS & iPadOS versions 14.0-16.6.1, 16.7 RC, and 17.0 to permanently install any .ipa file that you open with it without the re-signing requirements that come with sideloading, was updated this Friday evening to version 2.0.12.