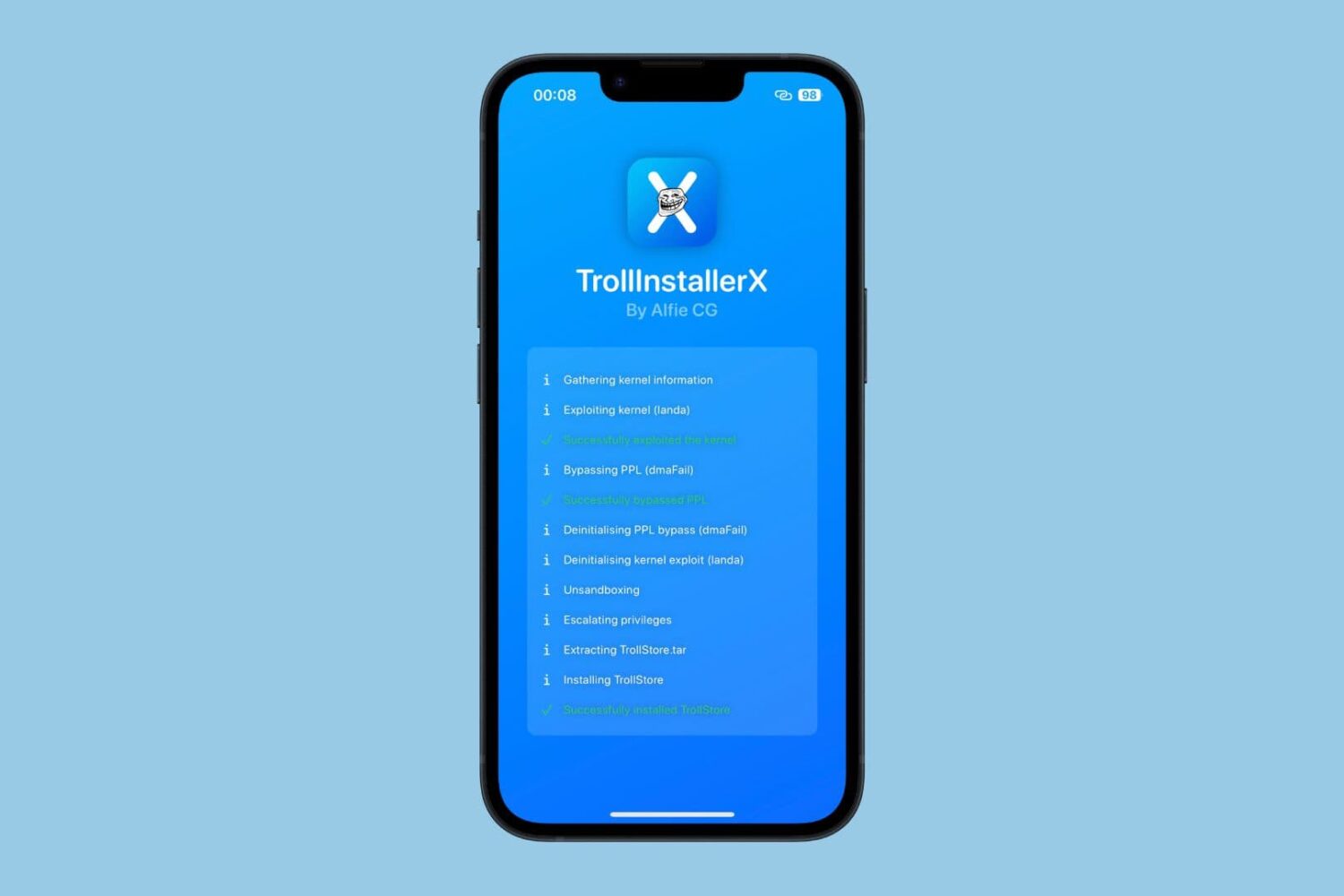
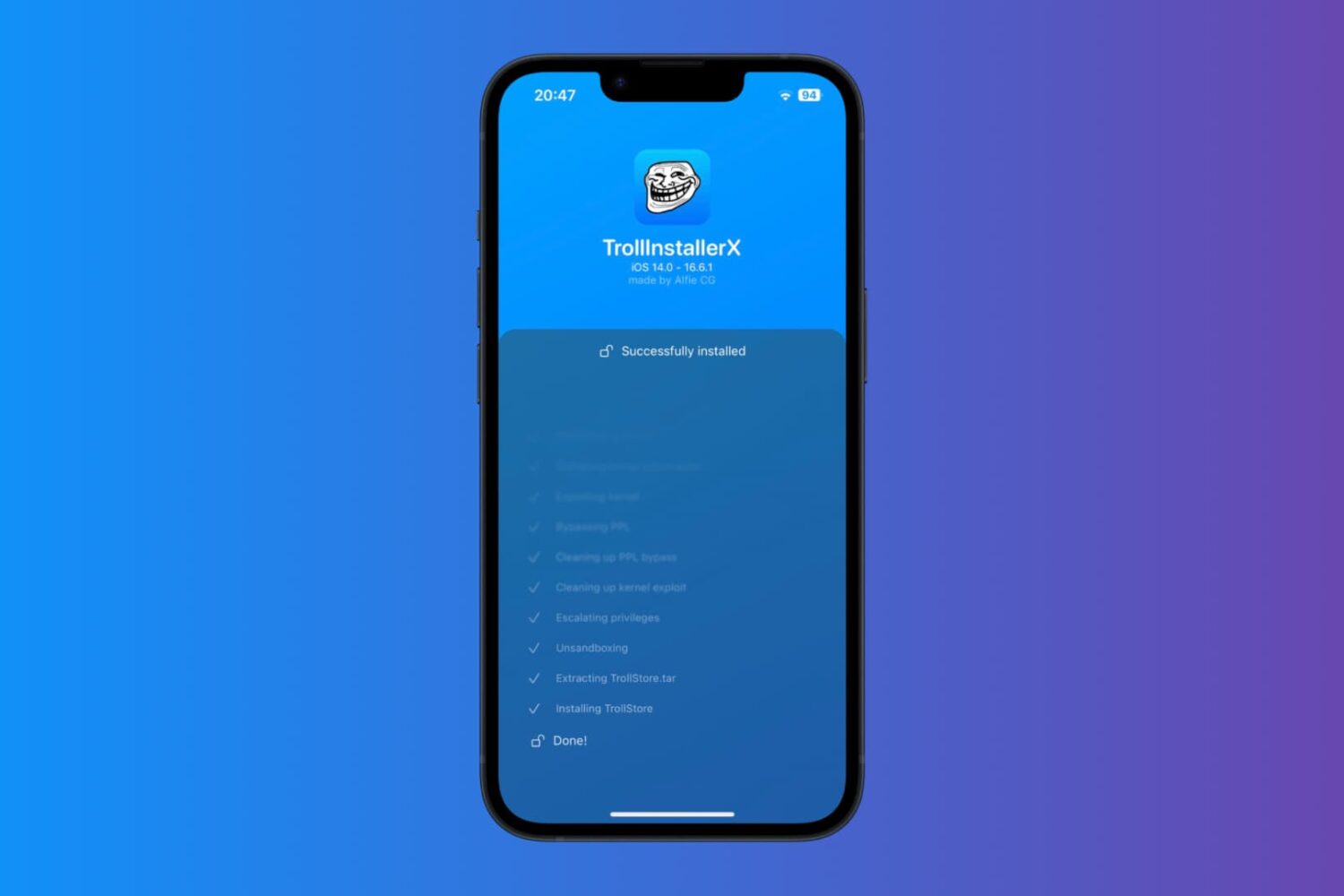
In case you’ve been living under a rock, there’s a new TrollStore installation method on the block called TrollInstallerX by iOS developer @alfiecg_dev, and it’s arguably one of the easiest ways to put TrollStore on your device aside from TrollHelperOTA.
How to install TrollStore on iOS 14.0-16.6.1 with TrollInstallerX