If you’ve followed along with us in our ongoing iPhone jailbreak news coverage, then you likely caught it wind of Luca Todesco showing off an iOS 16 jailbreak at the Hexacon security conference last Friday.
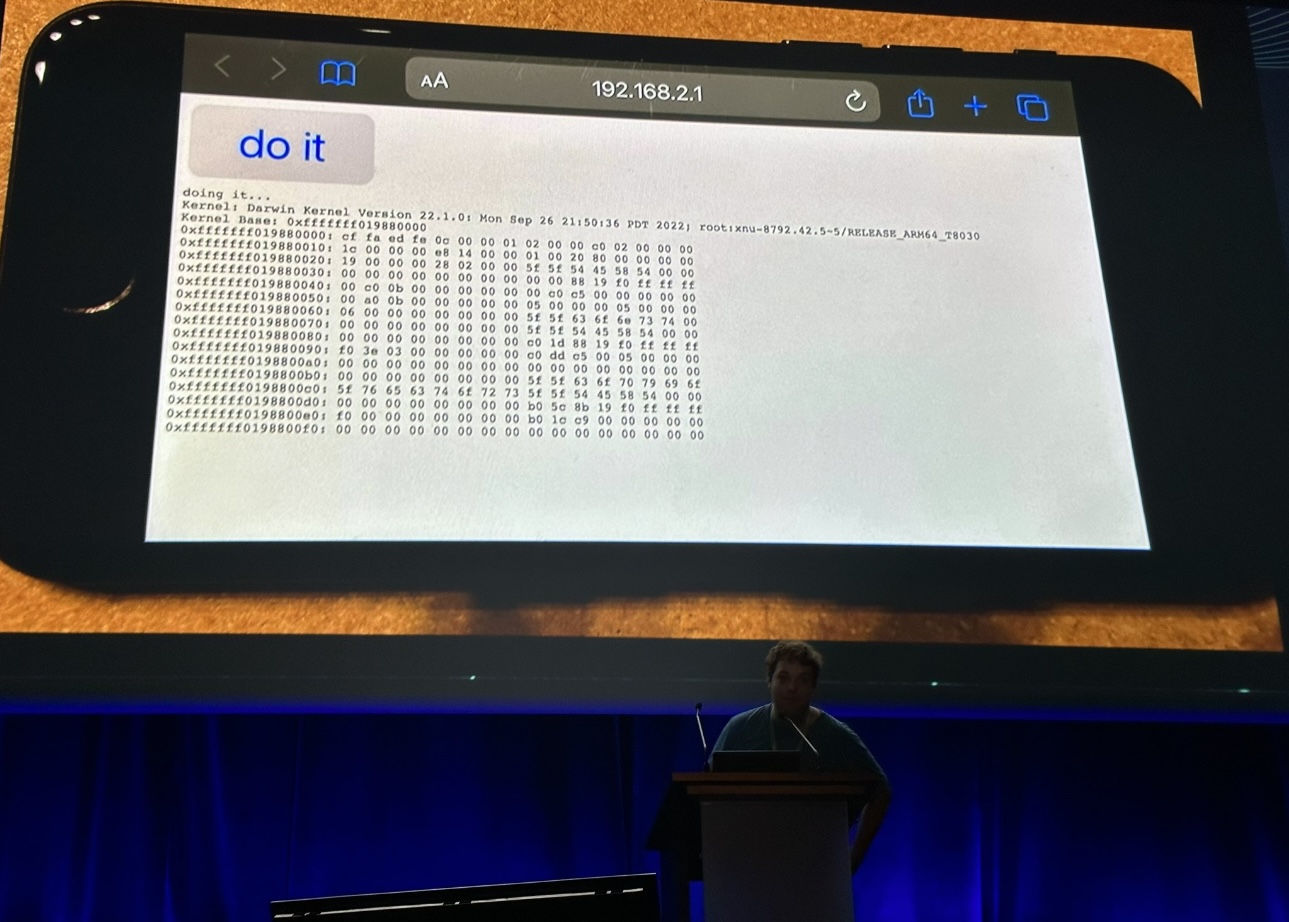
If you’ve followed along with us in our ongoing iPhone jailbreak news coverage, then you likely caught it wind of Luca Todesco showing off an iOS 16 jailbreak at the Hexacon security conference last Friday.

Security researcher and former evad3rs team jailbreak developer @pod2g made rare comments on Twitter this week following Luca Todesco’s talk at the most recent Hexacon security conference.

Speaking at the Hexacon security conference in Paris, France on Friday, hacker and security researcher Luca Todesco discussed Apple’s latest mobile software security trends and showed off a jailbreak on iOS 16.1 beta.

Just a couple of weeks ago, the checkra1n team updated the checkra1n jailbreak tool to version 0.12.3 with official support for iOS & iPadOS 14.5 along with a bevy of other miscellaneous improvements.
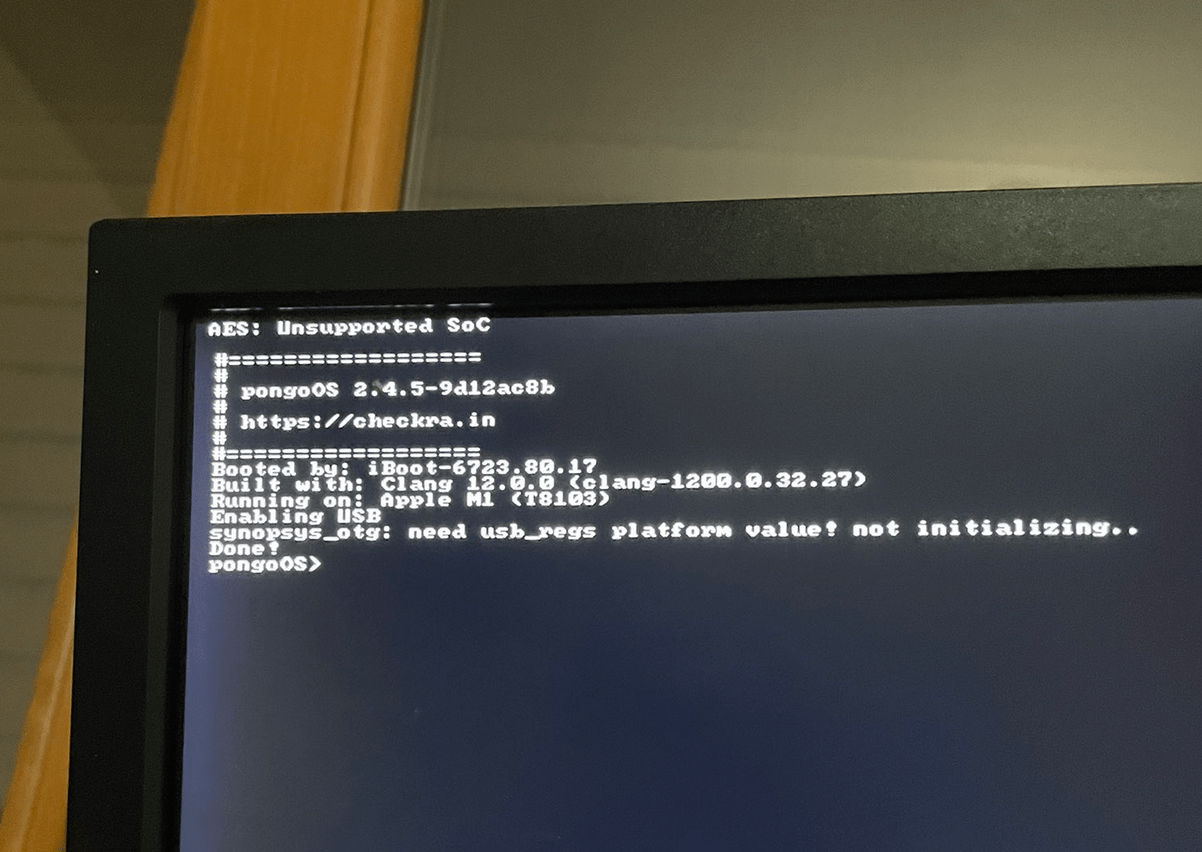
It’s not unheard of to see checkra1n team member Luca Todesco Tweeting about some sort of jaw-dropping hacking achievement. Todesco has shown time and time again that he wields magnificent hacking talents, and as of this evening, he appears to be at it again.
In a series of Tweets shared Saturday, Todesco teased multiple photographs of what appears to be pongoOS running on one of Apple’s brand-new M1 chip-equipped Macs.
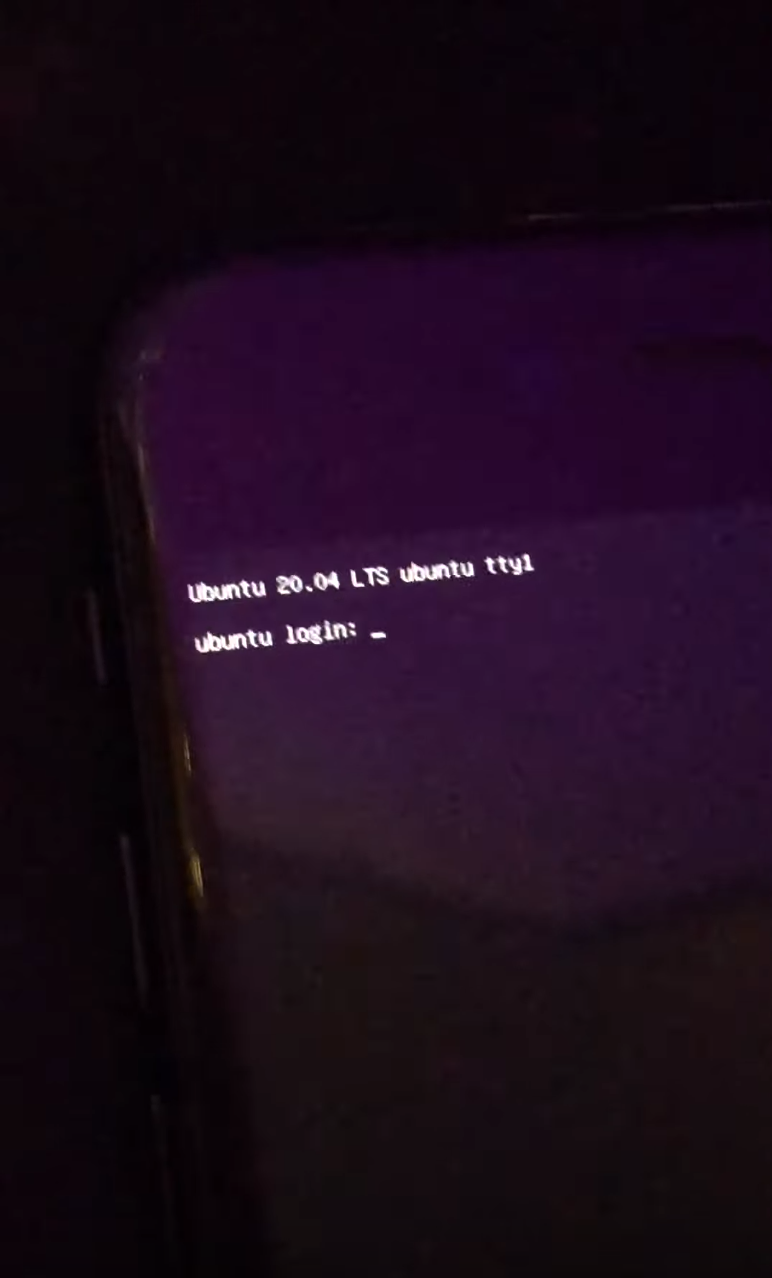
The checkra1n jailbreak utilizes such a powerful exploit that it offers a whole lot more than just a package manager and instant access to your favorite jailbreak tweaks. In fact, the hardware-based checkm8 bootrom exploit has proven more than capable of enabling a whole host of interesting hacks on compatible devices.
The latest of such hacks comes by way of Twitter user @RowRocka, who on Monday afternoon Tweeted a YouTube video of Ubuntu version 20.04 running on an iPhone 7 that had been pwned with the checkra1n jailbreak tool.

Checkra1n first picked up support for iOS & iPadOS 14 exactly one month ago starting today, but with a significant caveat in that it would initially support only A8-A9X devices. At the time, the team said it would work to add A10 support “in coming weeks,” and now that four weeks have passed since the announcement, it may come as no surprise that team member Luca Todesco addressed the community this afternoon via Twitter.
Now before your heart skips a beat on that subject, we’ll come right out and say that the latest comment contains good news. It seems that progress has been made in adding support for A10 devices running iOS & iPadOS 14, and Todesco expects a public release for this new support to happen quite soon:
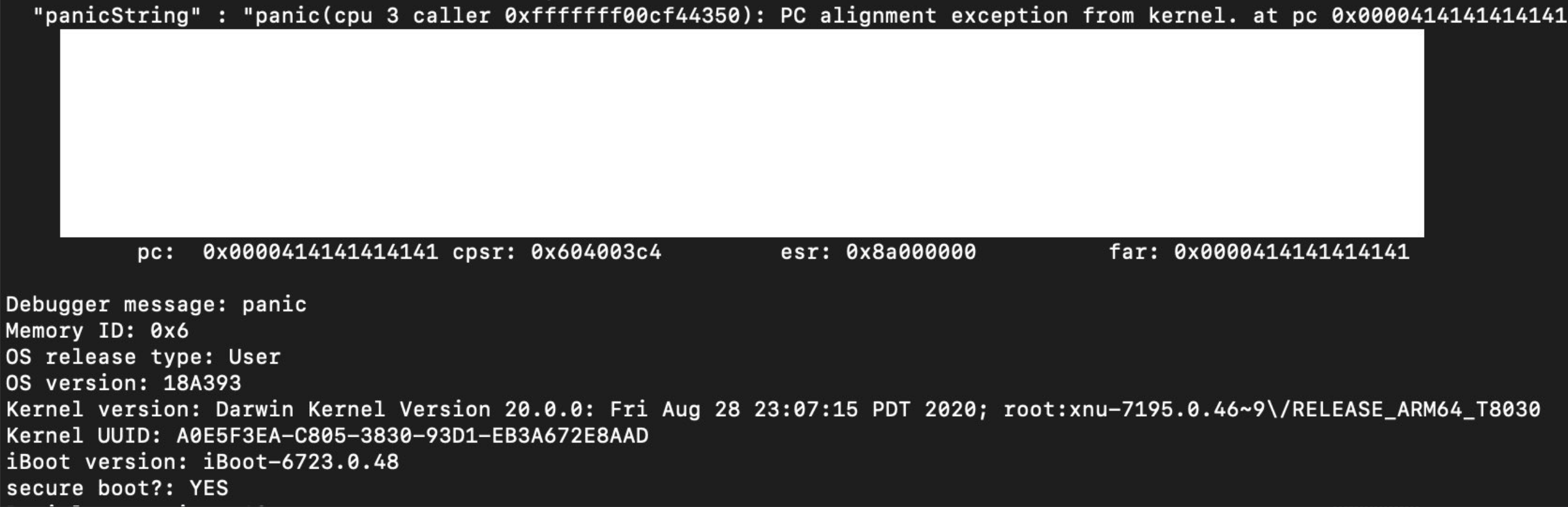
The only iOS & iPadOS 14 devices that can be publicly jailbroken at the time of this writing are those sporting A9 and A9X processors, and while that could change in the very near future as the checkra1n team works on adding A10 and A10X support, the bigger question involves the likes of much newer devices that aren’t even susceptible to the checkm8 bootrom exploit.
Fortunately, renowned hacker and checkra1n team member Luca Todesco shared a particularly interesting announcement via Twitter Monday afternoon in the form of what appears to be a working exploit and PAC bypass for iOS & iPadOS 14 devices:
The checkra1n jailbreak recently picked up support for iOS 14 on devices equipped with Apple’s A8-A9X processors, but as many noticed on the night this happened, the checkra1n team also elucidated on how it would take more time to add support for A10 and A10X devices and that they weren’t even sure if they would be able to add support for A11-equipped devices like the iPhone 8, 8 Plus, and X.
Given the rather unexpected and uncertain circumstances, we’re sure there are a lot of questions about the checkra1n jailbreak and when or if it will receive updates to support newer devices. With that in mind, we wanted to take a moment to deliver an FAQ-style post that would discuss many of the most common questions and the best answers for those questions that we have at the time of this writing.

Not even one week after Apple officially released iOS and iPadOS 14 to the general public, the checkra1n team has released checkra1n version 0.11.0 with support for Apple’s latest and greatest mobile operating system (albeit with a catch).
The checkra1n Twitter page shared the announcement late Monday night, followed closely by commentary from Todesco himself:
Hacker and checkra1n jailbreak team member Luca Todesco turned quite a few heads Sunday evening after posting a rather peculiar Tweet that appeared to tease substantial progress on an iOS 14 jailbreak.
The Tweet, embedded below, states “popped 14 so to celebrate I got a new pfp (profile picture).”
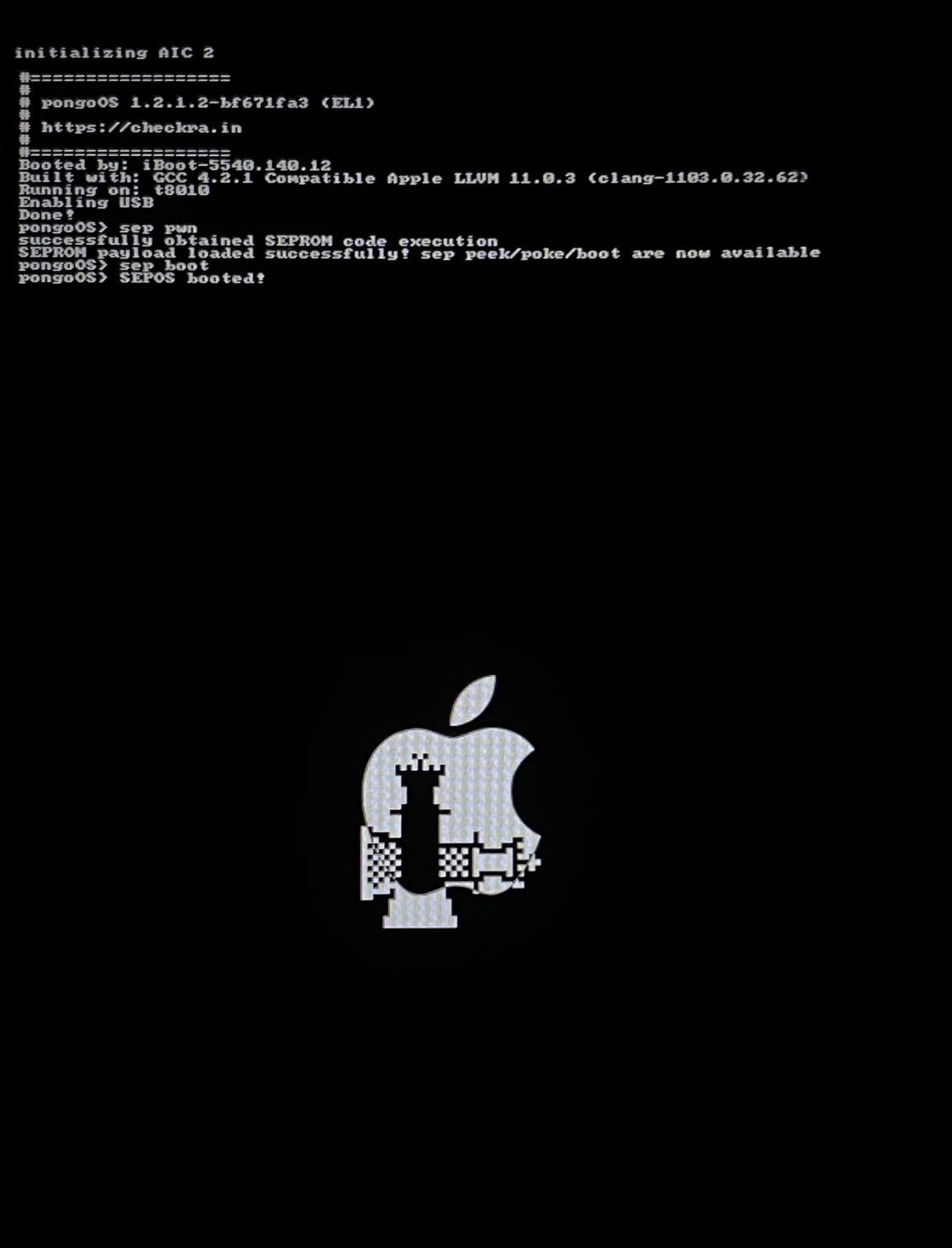
Nearing the end of last month, the Pangu Team took the stage at MOSEC 2020 to discuss a plethora of interesting topics, one of which really stood out from the rest. We’re of course talking about the unpatchable hardware based SEPROM vulnerability that targets a device’s secure enclave processor (SEP).
It wasn’t long after the SEPROM vulnerability was discovered and notes about it were published that famous hackers like Luca Todesco of the checkra1n team began tinkering with it. In fact, it was only yesterday that Todesco Tweeted some particularly eye-catching photos of checkra1n integration on an iOS device and of a T2-equipped Mac running the vulnerability as shown by the Touch Bar’s OLED display: