Security researcher Saar Amar on Monday published a proof of concept (PoC) of a kernel-level vulnerability dubbed CVE-2021-30883 that was patched by Apple’s iOS & iPadOS 15.0.2 software updates.
The write-up reignited hope that we’d see a jailbreak for recent iterations of Apple’s mobile operating systems, and perhaps unsurprisingly, some security researchers have already started going hands-on with it.
Late last night, security researcher @pattern_F_ took to Twitter to share a video of what appears to be a jailbreak demo built using the kernel vulnerability highlighted earlier in the week by Amar:
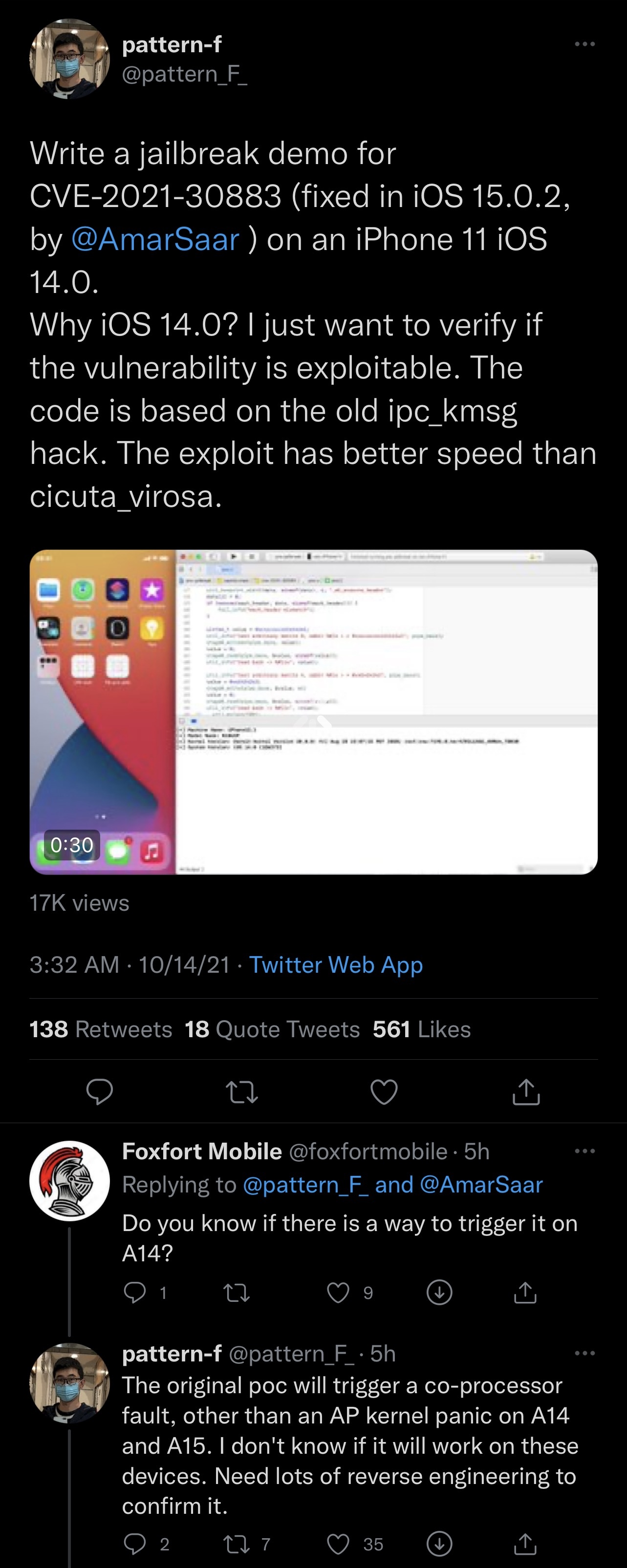
According to @pattern_F_, the device used in the video is an iPhone 11 running iOS 14.0. It’s also revealed that the vulnerability may not be readily viable on A14 and A15-equipped handsets like the iPhone 12 and 13 lineups as it is on previous devices like the iPhone 11 lineup and older; at least, not without reverse engineering to investigate a co-processor fault. This means there could be additional difficulties jailbreaking Apple’s most recent iPhone lineups, but additional testing would be required to confirm this.
The hacker also mentions that the code used in the jailbreak demo video is based on the older ipc_kmsg hack and that it offers improved speed when compared to the cicuta_verosa exploit currently used by the iOS & iPadOS 14-based Taurine jailbreak.
The ipc_kmsg hack doesn’t appear work on firmware versions beyond iOS & iPadOS 14.2 due to exploit primitive restraints, so @pattern_F_ hasn’t tested Amar’s kernel vulnerability beyond iOS or iPadOS 14.2. That doesn’t mean someone else won’t, though.
The jailbreak demo video verifies that Amar’s kernel vulnerability is indeed exploitable, which is good news for jailbreakers considering that it supports up to an including iOS & iPadOS 15.0.1 — with an important asterisk attached, of course.
The asterisk is that while it’s likely the vulnerability could result in a jailbreak for all current version(s) of iOS & iPadOS 14 up to and including iOS & iPadOS 14.8 in the future, the fact remains that iOS & iPadOS 15 have implemented novel security mitigations that will necessitate additional effort by jailbreak developers.
In any case, the biggest takeaway from @pattern_F_’s video demo is that Amar’s kernel vulnerability is exploitable. In short, this means that a talented jailbreak developer should be able to make use of it one way or another, whether it’s to replace cicuta_verosa for the speed improvements it purportedly offers or to add support for new firmware versions to an existing jailbreak tool.
In an unrelated side note, security researcher Linus Henze plans to release an untether that supports up to and including iOS & iPadOS 14.5.1 later this month.
With all the exciting news dropping lately, it will indeed be interesting to see whether anything materializes from it or not. Only time will tell, however.
Are you hyped about all the new security research that appears to be making headlines recently? Be sure to let us know why or why not in the comments section down below.