Thanks to the checkm8 bootrom exploit that powers it, the checkra1n jailbreak has earned a reputation for its resilience. No mere software update can patch this exploit, and so susceptible devices (those equipped with A7-A11 chips) should effectively be jailbreakable for life…
True as that may be, Apple can still obfuscate by introducing software barriers that make the checkra1n team work harder to develop workarounds so checkra1n can work properly. We witnessed this after the release of iOS & iPadOS 14 when A10-A11 devices picked up a new security mitigation that impacted jailbreaking them with checkra1n.
The checkra1n team successfully bypassed the challenge above on A10(X) devices with a SEPROM exploit, but no such bypass currently exists for A11 devices at this time. Still, you’ve probably seen or heard about people jailbreaking A11-equipped handsets such as the iPhone 8, iPhone 8 Plus, and iPhone X running some version of iOS 14 with checkra1n.
An iPhone X being pwned by checkra1n.
So how do they do it? We’re glad you asked because that’s what we’ll be discussing with you in this post.
Jailbreaking an A11 chip-equipped device with checkra1n
The process of jailbreaking an iPhone 8, iPhone 8 Plus, or iPhone X running iOS 14 with checkra1n is almost the same as jailbreaking any other device with this tool except that you’ll need to tick a special option off in the checkra1n app’s settings to move forward. With that in mind, our existing checkra1n tutorial is still valid even for the aforementioned devices, but there’s an additional step that users of said devices must take to complete the jailbreak process.
Initially, attaching an iPhone 8, iPhone 8 Plus, or iPhone X to your Mac with a MFi-certified USB-A to Lightning cable and launching the checkra1n app will result in a message like the one below that reads, “Sorry, [insert iPhone model here] is not supported on [insert version of iOS 14 here] at this point.”
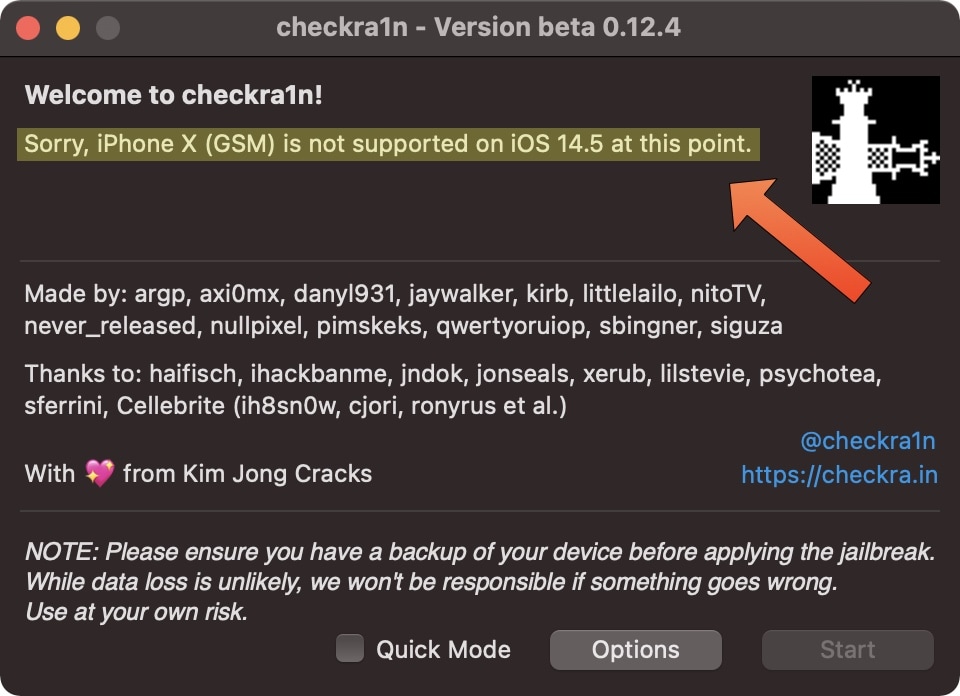
Based on this message, you might be thinking that this means your device can’t be jailbroken with checkra1n, but that’s not entirely true. Here’s how to get around the pesky message:
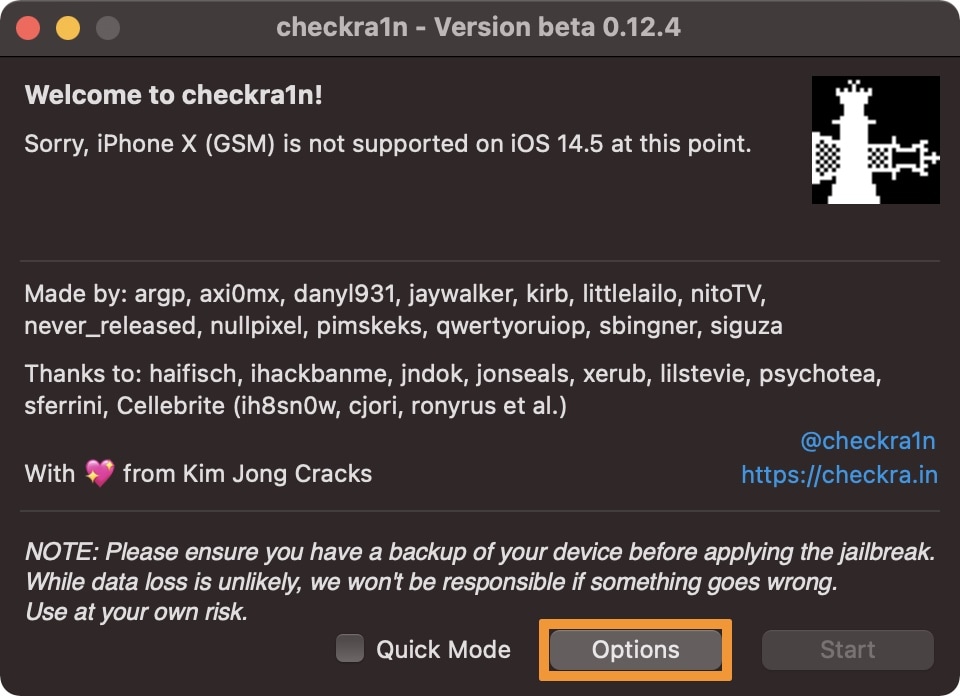
1) Click on the Options button at the bottom of the checkra1n app window:
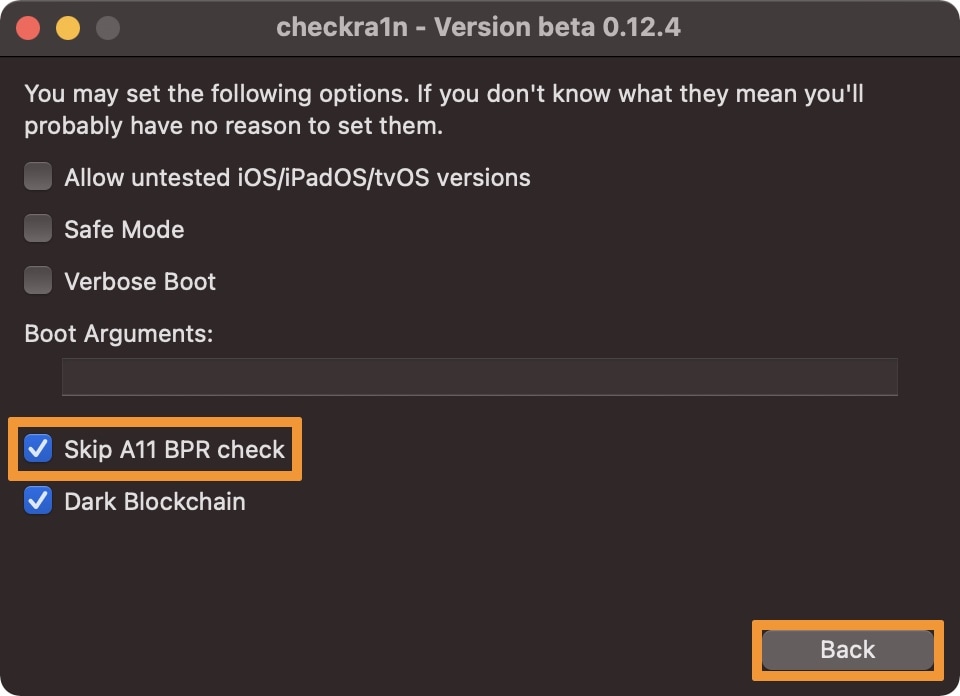
2) Enable the Skip A11 BPR check option, then click on the Back button at the bottom of the checkra1n window:
3) Now you’ll see a different message in the checkra1n window:
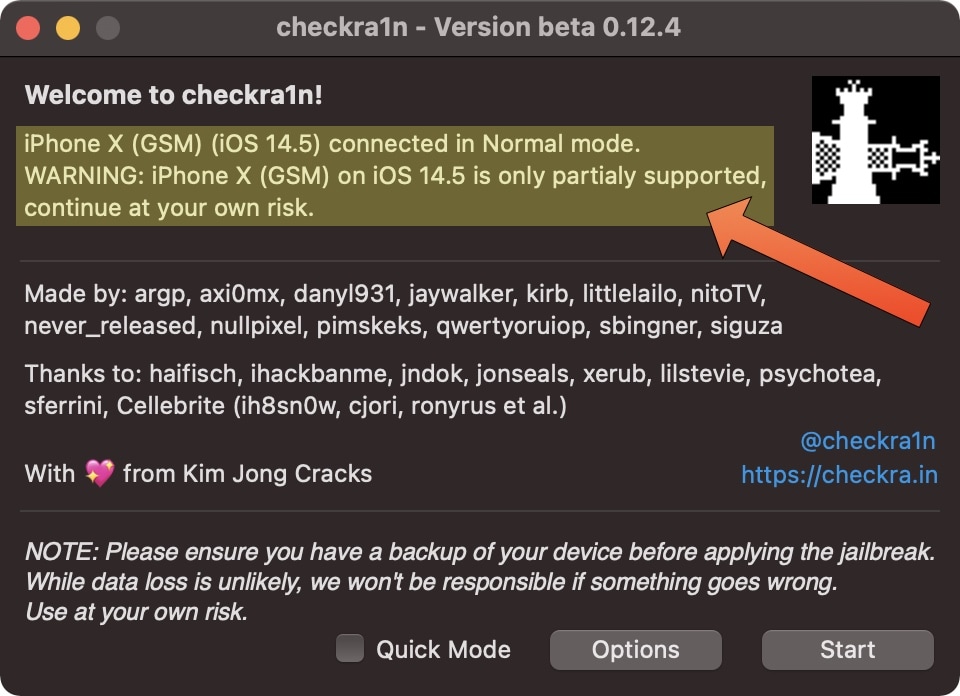
The new message reads, “[insert iPhone model here] connected in Normal mode. WARNING: [insert iPhone model here] is only partially supported, continue at your own risk.” This message simply means that checkra1n will jailbreak your connected handset, but it won’t patch the new security mitigation implemented by Apple. In other words, you won’t be able to use a passcode or biometric authentication for iOS.
After you see the message above with your iPhone 8, iPhone 8 Plus, or iPhone X, you can then go ahead and follow the steps outlined in our tutorial that discusses how to jailbreak with checkra1n. But make sure to read on first…
No passcode or biometric authentication
Perhaps the most important caveat to jailbreaking an A11-equipped handset like the iPhone 8, iPhone 8 Plus, or iPhone X running iOS 14 with checkra1n is that you can’t have a native passcode to safeguard all your personal data.
Yes, you read that right.
Lots of people depend on their passcode to keep their data secure, and that’s one of the reasons we strongly advise that you use this method at your own risk. Obviously, this won’t matter to folks who use their jailbroken iPhone solely as a secondary hobby device with no personal data on it, but if your jailbroken iPhone 8, iPhone 8 Plus, or iPhone X is your daily driver, then you may have a lot more to lose from risking the passcode-free life.
Another downside to not having native access to biometric authentication such as Face ID or Touch ID is that you can’t authenticate yourself to use Apple Pay. This is a drawback to the current situation, but if you can live without Apple Pay, then this might be a non-issue to you.
Alternative means of protection
All worries aside, the lack of a passcode doesn’t mean you have to go without any protection whatsoever. Some apps include built-in Face ID or Touch ID authentication capabilities, meaning that you can enable a feature to authenticate yourself before the app will launch. This is more common in data-sensitive apps such as banking and screen-sharing apps, but we’ve seen it in others too.
Furthermore, albeit not as effective as a full-fledged device-encompassing passcode, jailbreak tweaks exist that can prevent other individual apps or interfaces on your device from launching without first entering a pin number or authenticating yourself another way. Our favorite example is checkl0ck since it enables native-style biometric authentication and a passcode while in a jailbroken state, but another example is lockdown since it enables only a native-style passcode experience while in a jailbroken state, but for a smaller price tag.
Another option is BioProtectXS, and it can be used on your A11-equipped device, even without a passcode, as long as you’ve set Up Face ID or Touch ID at least once:
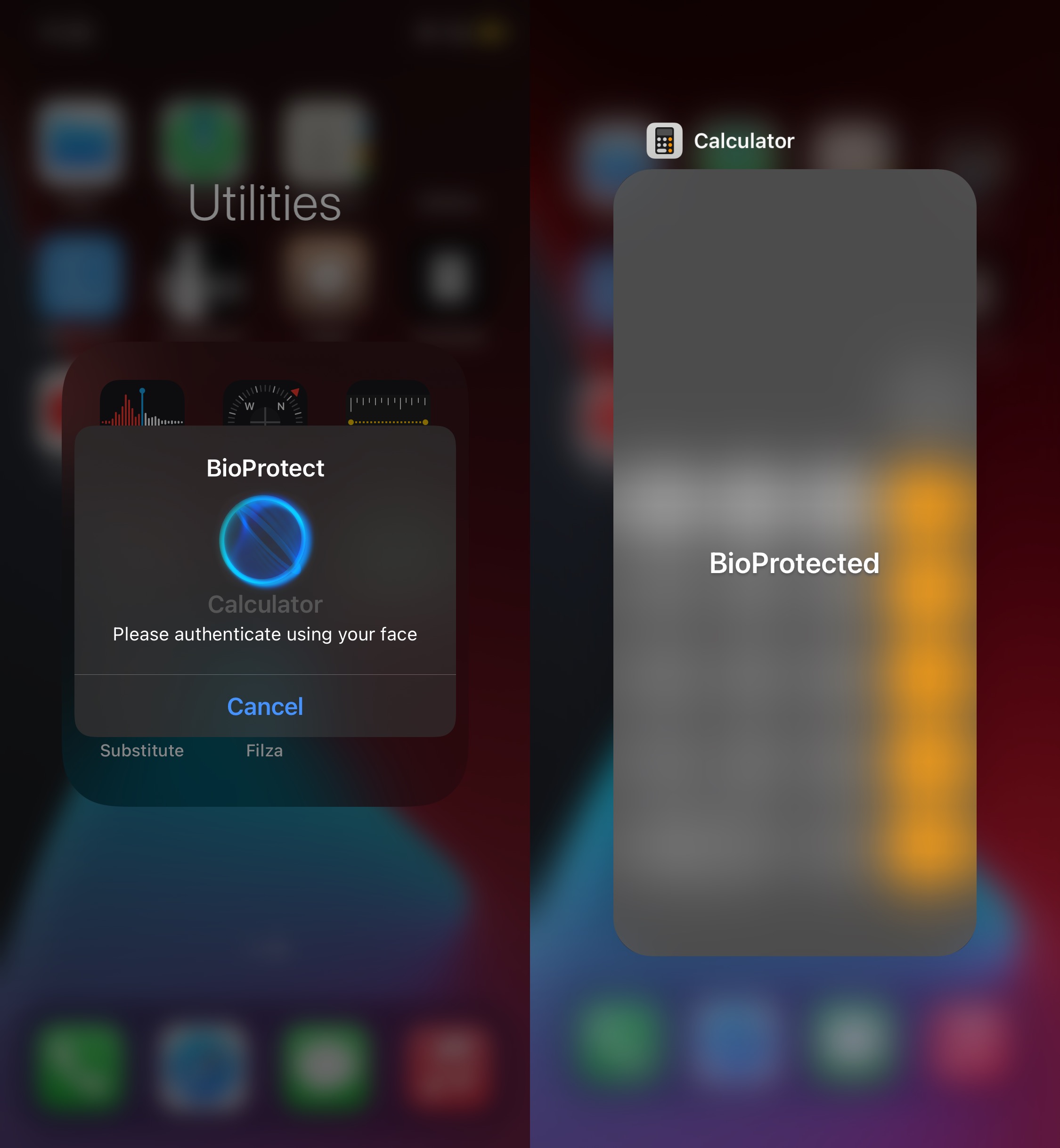
BioProtectXS is a useful utility by iOS developer Elias Limneos available for $2.99 from Limneos’ repository that makes it harder for someone who comes in contact with your passcodeless iPhone to launch apps and view your private data. While it’s possible to bypass any jailbreak tweak with a reboot, not everyone is as well-versed with jailbreaking as you might be, so they might not think twice about doing something like that. You can use ignorance like this to your advantage to help protect your device.
An additional step that you can and should take to protect your device’s security is to change the default root password from “alpine” to something that only you will remember. This can be accomplished via a mobile Terminal app like the free NewTerm 2 app from the Chariz repository.
In summary, using a jailbreak tweak to substitute an actual device passcode isn’t the most ideal or secure thing to do, but it’s something instead of nothing, and if you can’t resist the benefits of jailbreaking (like me), then it could be your best option.
Conclusion
A11 devices like the iPhone 8, iPhone 8 Plus, and iPhone X are absolute beasts when it comes to performance with or without a jailbreak, and their unpatchable susceptibility to the checkm8 bootrom exploit makes them fun jailbreakable devices to own.
Unfortunately, the inability to set a passcode when jailbreaking these handsets on iOS 14 with checkra1n and the inability to use Apple May May come as major concerns, but the method above can certainly help you mitigate security risks if you’re concerned.
Have you already or will you jailbreak your A11-equipped device on iOS 14 with checkra1n after knowing what you do now? Be sure to let us know in the comments section down below.