All the hubbub lately surrounding kernel vulnerabilities for the iPhone and iPad has been in relation to the now-turned kernel exploit for iOS & iPadOS 15.0-15.1.1. But a fresh announcement shared Wednesday afternoon to Twitter by @Synacktiv is turning quite a few heads.
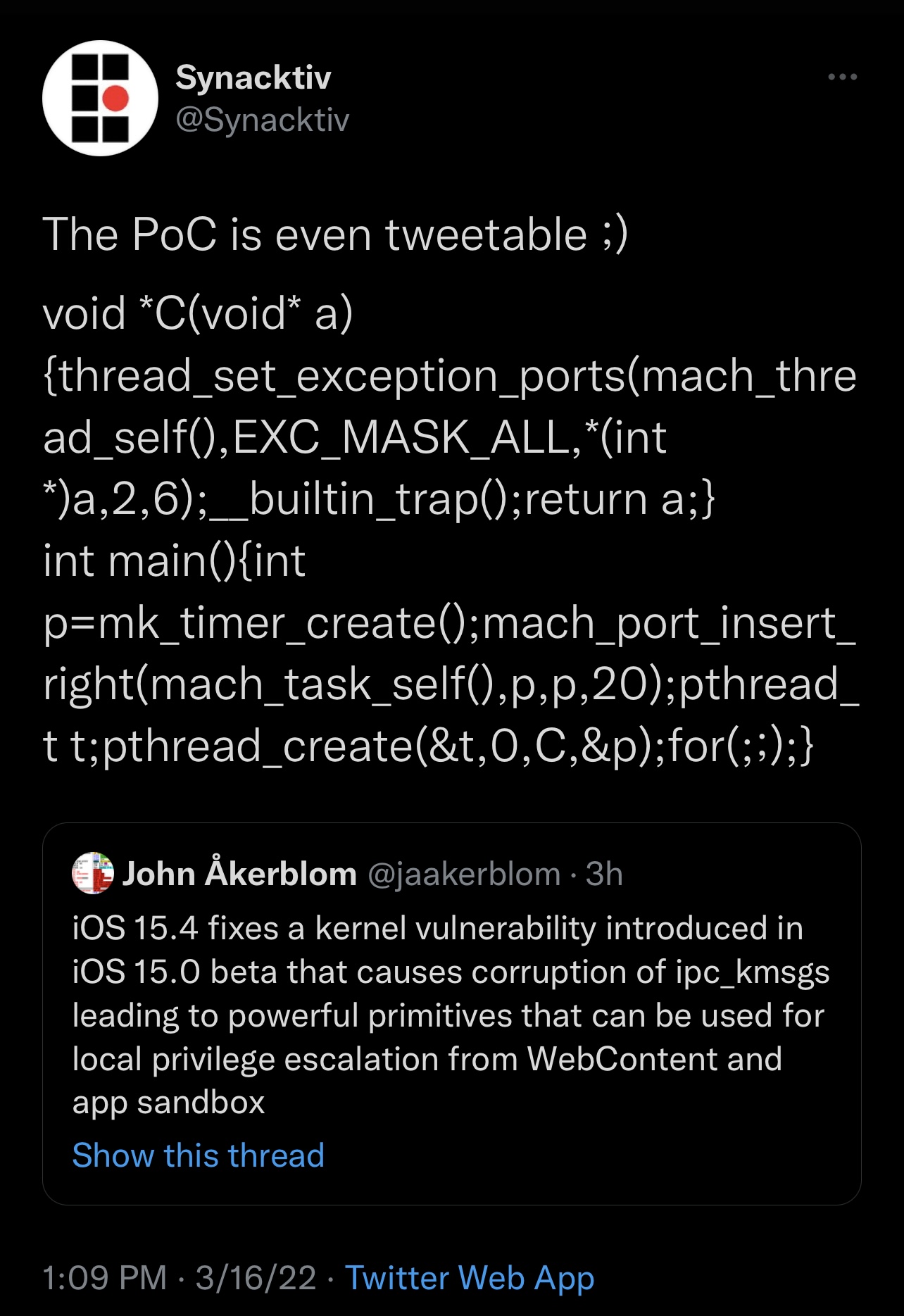
The Tweet, shown above for your viewing pleasure, depicts what appears to be a short proof of concept (PoC) demonstrating a kernel-level vulnerability that affects iOS & iPadOS 15.0-15.3.1.
Citing a linked-Tweet, this particular bug was patched in the iOS & iPadOS 15.4 software update released just this week and has been present since the iOS & iPadOS 15.0 betas.
Explaining further, @jaakerblom notes that the bug “causes corruption of ipc_kmsgs leading to powerful primitives that can be used for local privilege escalation from WebContent and all sandbox.”
So what does this all mean?
At the time of this writing, we appear to have a PoC, but not an exploit. An exploit would be just one of the components, in addition to others, that are required to develop a jailbreak.
In previous announcements, Odyssey Team lead developer CoolStar did a marvelous job of breaking down what’s required to develop a jailbreak for different types of device and firmware combinations, and it boils down to this:
A9-A11-equipped devices ranging from the iPhone 6s to the iPhone X should be fairly straightforward to develop jailbreaks for on any version of iOS & iPadOS 15 apart from needing to be rootless. These devices are also susceptible to the checkm8 hardware-based bootrom exploit that powers the yet-to-be-updated checkra1n jailbreak.
A12 and newer-equipped device including the iPhone XS all the way up to the iPhone 13 Pro, on the other hand, boast new hardware mitigations that will make jailbreaking various versions of iOS & iPadOS 15 more difficult…
The Odyssey Team is working on a sandbox escape method for A12 and newer-equipped devices running iOS & iPadOS 15.0-15.1.1, however since setuid appears to be done for in iOS & iPadOS 15.2 and later, userland exploits may be required to get jailbreaks working on A12 and newer-equipped handsets running the newer variants of iOS & iPadOS 15 such as 15.2-15.3.1.
So given what we know now, if an exploit can be made using the newly-shown PoC for iOS & iPadOS 15.3.1 and earlier, then A9-A11 devices should be good to go with it. However according to CoolStar, we would likely need a userland exploit as well to say the same for A12 and newer-equipped devices since they have additional hardware mitigations that need to be circumvented.
What we recommend
If you’re currently using iOS or iPadOS 15.1.1 or below and wish to jailbreak in the future, then stay where you are and avoid updating to any newer firmware.
If you’re currently using iOS or iPadOS 15.2-15.3.1 and you want to increase your odds of being able to jailbreak in the future, then stay where you are and avoid updating to any newer firmware.
If you updated to iOS or iPadOS 15.4 already and you want to increase your odds of being able to jailbreak in the future, then immediately downgrade to iOS or iPadOS 15.3.1 with iTunes or Finder while it’s still being signed by Apple.
Wrapping up
While this PoC release is certainly good news, there’s no telling if or when a full exploit, much less a jailbreak, will result from it. If anything, it’s a modicum of hope for those who missed their chance to DelayOTA to iOS or iPadOS 15.1.x as the deadline passed this past weekend.
Are you excited to see yet another PoC for newer versions of iOS & iPadOS 15? Be sure to let us know in the comments section down below.