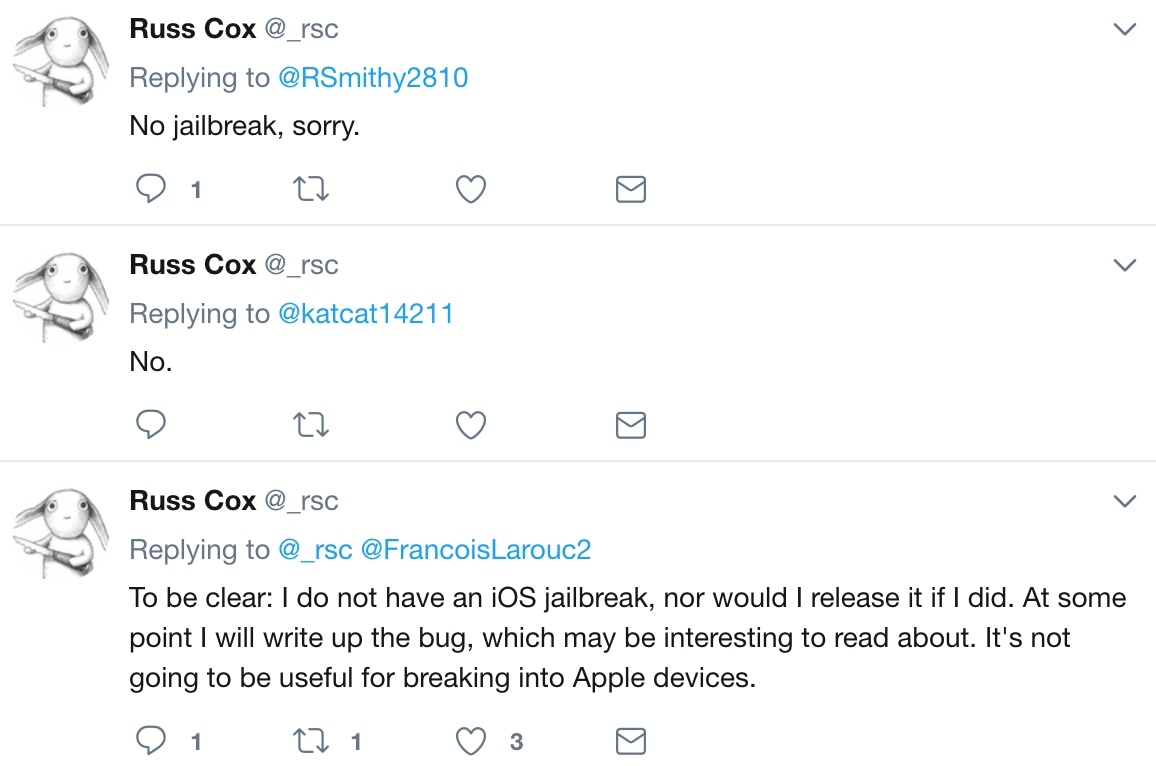
 Just a couple of days ago, security researcher Russ Cox made headlines after purportedly discovering a kernel-level exploit on iOS 11.2-11.2.1 devices. But as it seems, the ensuing excitement may have gotten a little bit out of hand.
Just a couple of days ago, security researcher Russ Cox made headlines after purportedly discovering a kernel-level exploit on iOS 11.2-11.2.1 devices. But as it seems, the ensuing excitement may have gotten a little bit out of hand.
Apple’s own security release notes for iOS 11.2.5 cited Cox’s bug as a means of executing arbitrary code on stock devices, but according to the researcher himself, it was nothing more than a memory corruption and Apple may have over-credited his finding.
Cox took to Twitter on Thursday to shed some light on the confusion, noting that perhaps Apple saw something in his bug that he had not. Furthermore, he reiterates his original statement about how jailbreakers would be disappointed with this bug:
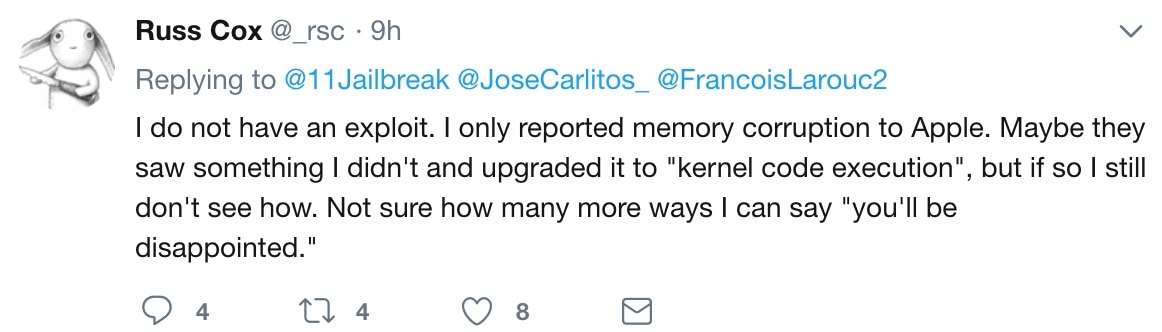
Kernel-level exploits have led to jailbreaks in the past; that said, it isn’t hard to understand why Cox’s finding received so much attention initially. Then again, no one really knows why Apple labeled Cox’s memory corruption bug as a “kernel-level code execution” exploit when it apparently wasn’t one from the start.
The news is undoubtedly disappointing for anyone that had a glimmer of hope that their iOS 11.2-11.2.1 devices might become jailbreakable. On the other hand, security researchers discover new exploits all the time, and it’s only a matter of time before something else surfaces.
Given the circumstances, Ian Beer’s tfp0 exploit for iOS 11.0-11.1.2 remains the latest viable exploit for use in jailbreaks. Tools like Electra and LiberiOS are already using it, and others could surface after Saurik updates Cydia and Mobile Substrate for iOS 11.
Are you disappointed by how things panned out? Share your thoughts with us in the comments below.