It’s the most significant cryptographic security upgrade in iMessage history, according to Apple, that will shield us from threats that don’t exist yet.
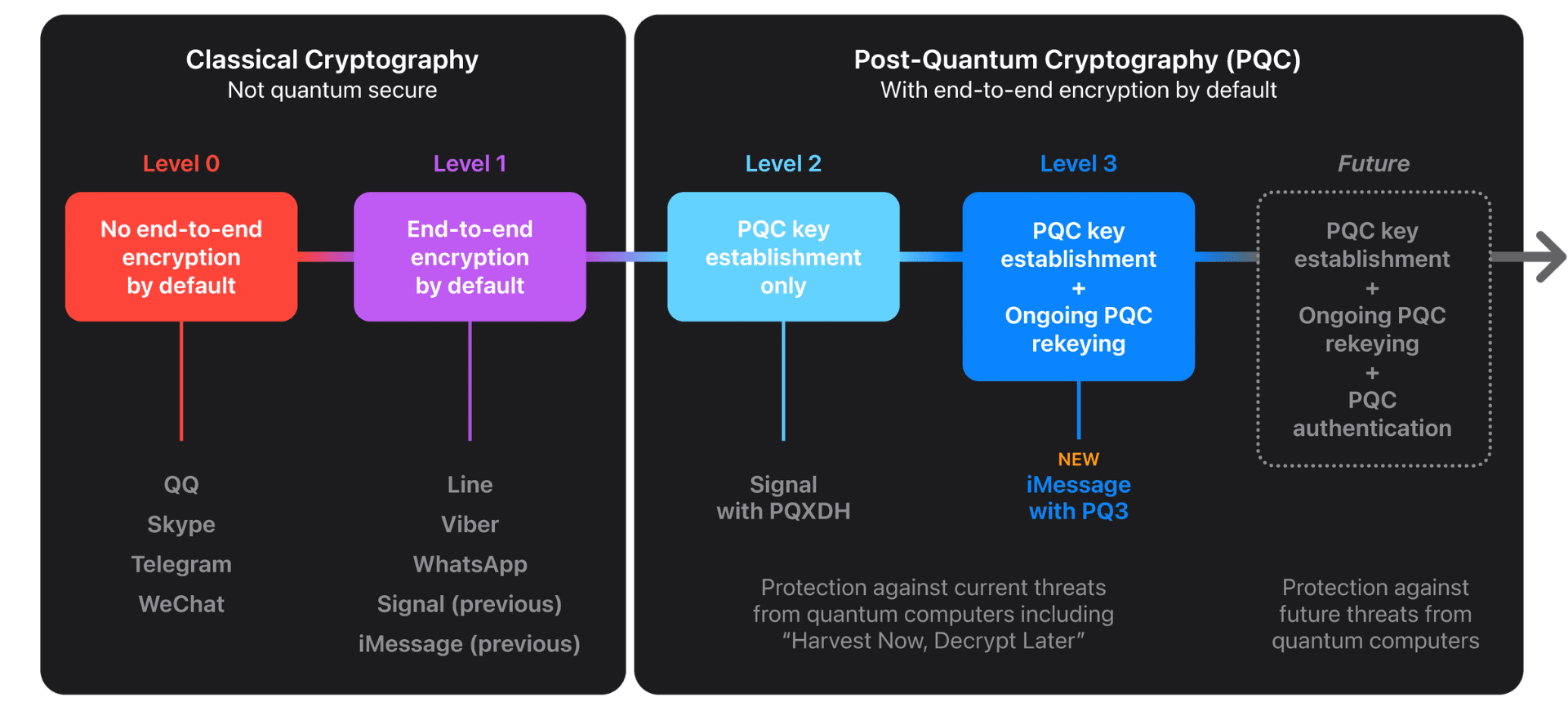
Apple announced on February 21 that the security of iMessage’s end-to-end encryption has been upgraded to the post-quantum cryptographic protocol (PQ3), making end-to-end encrypted messaging more secure than ever before.
iMessage isn’t the first messaging software to adopt this protocol—Signal is—but Apple’s approach is even more secure than two layers of security with traditional post-quantum cryptography (PQC) key establishment and ongoing PQC rekeying.
How the Q3 protocol hardens iMessage encryption
By contrast, Apple’s protocol secures the initial key and ongoing rekeying to protect against future threats. Notably, should a given key become compromised, iMessage can “rapidly and automatically restore the cryptographic security of a conversation,” the company explains on its Security Research blog.
Quantum security should protect against a scenario known as “Harvest Now, Decrypt Later,” where an attacker collects encrypted data and keeps it safe until a sufficiently powerful quantum computer has been created to break the encryption.
Although such quantum computers don’t yet exist, extremely well-resourced attackers can already prepare for their possible arrival by taking advantage of the steep decrease in modern data storage costs.
And:
The premise is simple: such attackers can collect large amounts of today’s encrypted data and file it all away for future reference. Even though they can’t decrypt any of this data today, they can retain it until they acquire a quantum computer that can decrypt it in the future, an attack scenario known as Harvest Now, Decrypt Later.
Listen, quantum computers have a long way to go before they become commercially feasible. But instead of waiting for quantum computing to happen, Apple has chosen to take proactive steps now to protect your iMessage exchanges from “Harvest Now, Decrypt Later” attacks carried out with a help from future quantum computers.
iOS 17.4 brings iMessage quantum security
To take advantage of the new security protocol in iMessage, you’ll need to update your iPhone, iPad, Mac and Apple Watch to iOS 17.4, iPadOS 17.4, macOS 14.4 and watchOS 10.4. Apple will release these software updates in March.
All devices in an iMessage exchange must have the latest software updates in order to secure conversations with the new protocol.
Apple explains that conversations between devices that support PQ3 will automatically upgrade to the post-quantum encryption protocol. The PQ3 will fully replace the existing iMessage protocol “within all supported conversations this year.”