The kernel file descriptor (kfd) exploit that grants kernel memory read and write privileges on firmware up to and including iOS & iPadOS 16.6 beta 1 is already being used to modify system files like the MacDirtyCow exploit was on iOS & iPadOS 15.0-16.1.2. But what about jailbreaking?
As we noted when first discussing kfd, it could be useful in making a jailbreak, but there was a lot of talk about newer devices requiring a PPL bypass to complete it. Fortunately for anyone with an older device, a developer has started working to use kfd to make a jailbreak that supports older arm64 devices up to and including the iPhone X.
From what we can gather, the project is being spearheaded by HAHALOSAH, the developer who brought us the NoFreeAppLimit jailbreak tweak, and they appear to be working closely with Mineek of the palera1n team, likely because of their expertise in making jailbreaks for older devices.
While palera1n already exists and can jailbreak virtually any version of iOS or iPadOS on the iPhone X and below, the fact remains that it’s a semi-tethered jailbreak and that you need to use a computer to get back into a jailbroken state after every reboot. More than that, palera1n users (especially iPhone X users) battle with SEP-related feature loss such as Touch ID/Face ID, passcode, and Apple Pay.
A kfd-based semi-untethered jailbreak would not only add jailbreaking convenience for older device users, but would also permit unfettered access to those aforementioned SEP-related features. That means that there would be no loss of Touch ID/Face ID, passcode, and Apple Pay functionality.
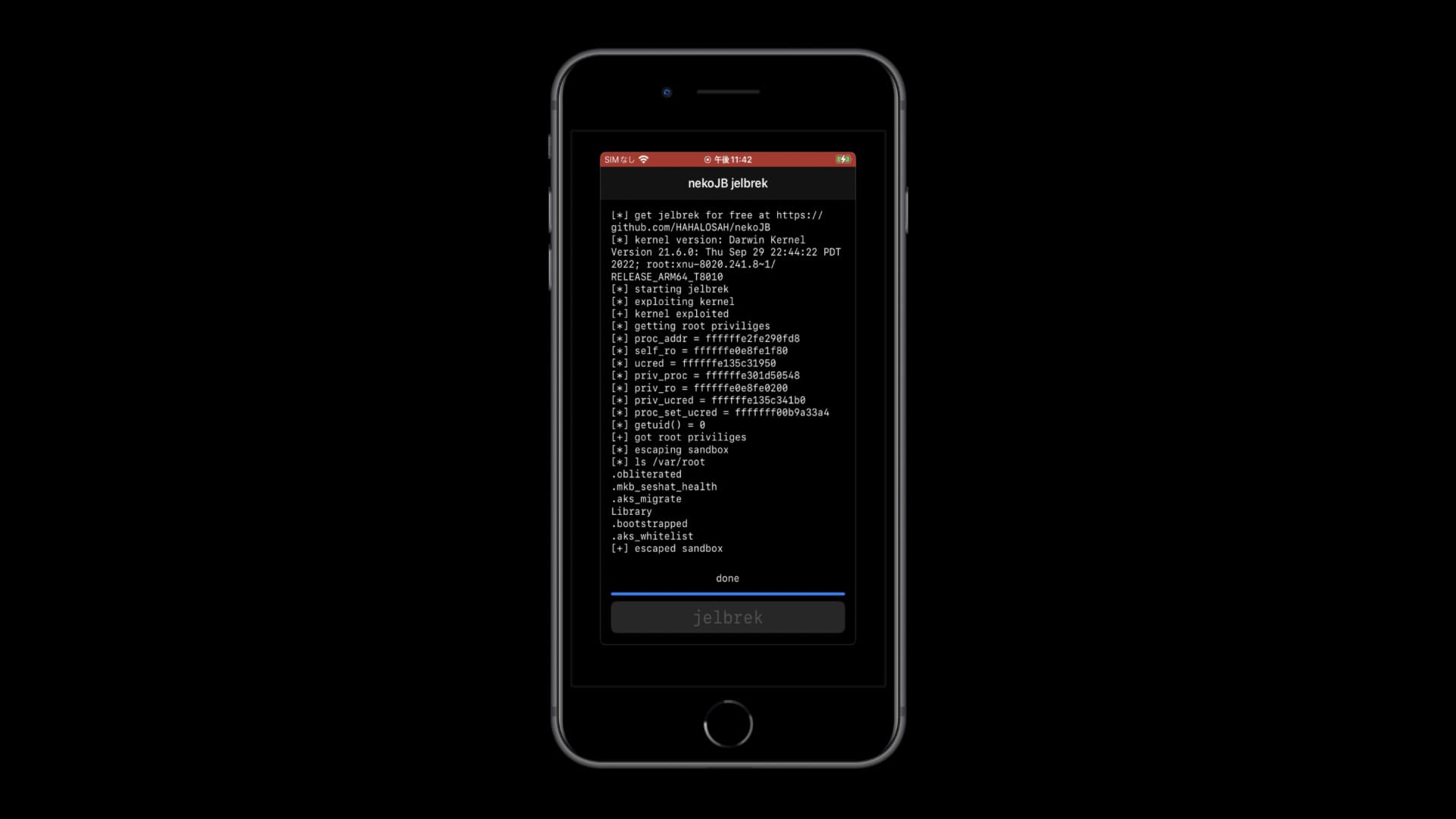
In a post shared Saturday morning to /r/jailbreak, HAHALOSAH said that the project is currently being called nekoJB. Furthermore, it won’t support arm64e devices because these devices require a PPL bypass that doesn’t exist yet.
At this time, a kfd-based jailbreak hasn’t yet been achieved, but the post does show a screenshot of sandbox escape being achieved, which is an important step in the right direction.
It will indeed be interesting to see what becomes of the nekoJB project, as it has the potential to be a convenient alternative to palera1n for anyone still hanging on to their arm64 device(s).
Are you excited to see where this goes? Let us know why or why not in the comments section down below.