Interesting news arose this weekend after @exploit3dguy shared what appears to be a successful blackbird exploit-based firmware downgrade on an iPhone 6s to iOS 10.0.1 with fully working passcode functionality.
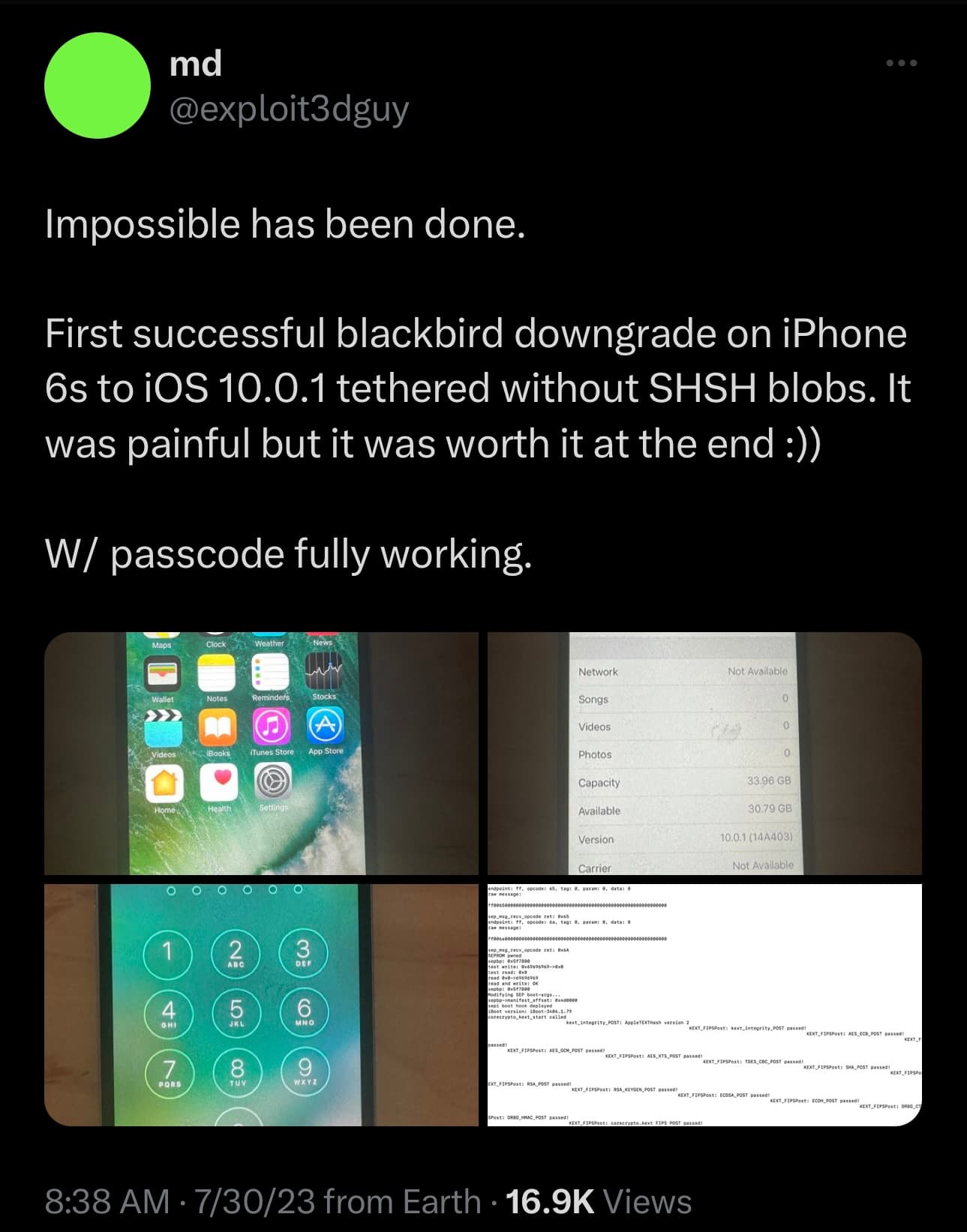
From what we can gather, the feat demonstrated above is possible on an untethered basis if the user has saved SHSH blobs and on a tethered basis if the user hasn’t saved SHSH blobs.
Furthermore, it should work on other versions of iOS, as long as the susceptible device has blackbird-supported SEP hardware.
In the Tweet, @exploit3dguy said it was the first time that this has been accomplished and that it required a lot of effort. The Tweet received lots of positive response from the jailbreak community, including from members such as Jake James and Tihmstar.
If you weren’t already aware, blackbird is a Secure Enclave Processor (SEP) exploit that exists in devices equipped with A8, A9, A10, and T2 chips (and their variants). It works in tandem with a hardware-based bootrom exploit, such as checkm8, which is why it only supports older devices up to and including those with A10 chips inside.
With this feat having been achieved, it will be interesting to see if it transforms from a mere proof of concept into a usable utility that iPhone and iPad users with compatible devices will be able to take advantage of. Of course, only time will tell.
Are you excited to see what becomes of blackbird? Let us know in the comments section down below.