Developmental news pertaining to iOS software security surfaced this week after the @ElcomSoft Twitter account shared screenshots of what appears to be a working forensic toolkit for A11-A13 handsets running iOS or iPadOS 14.4-14.8.
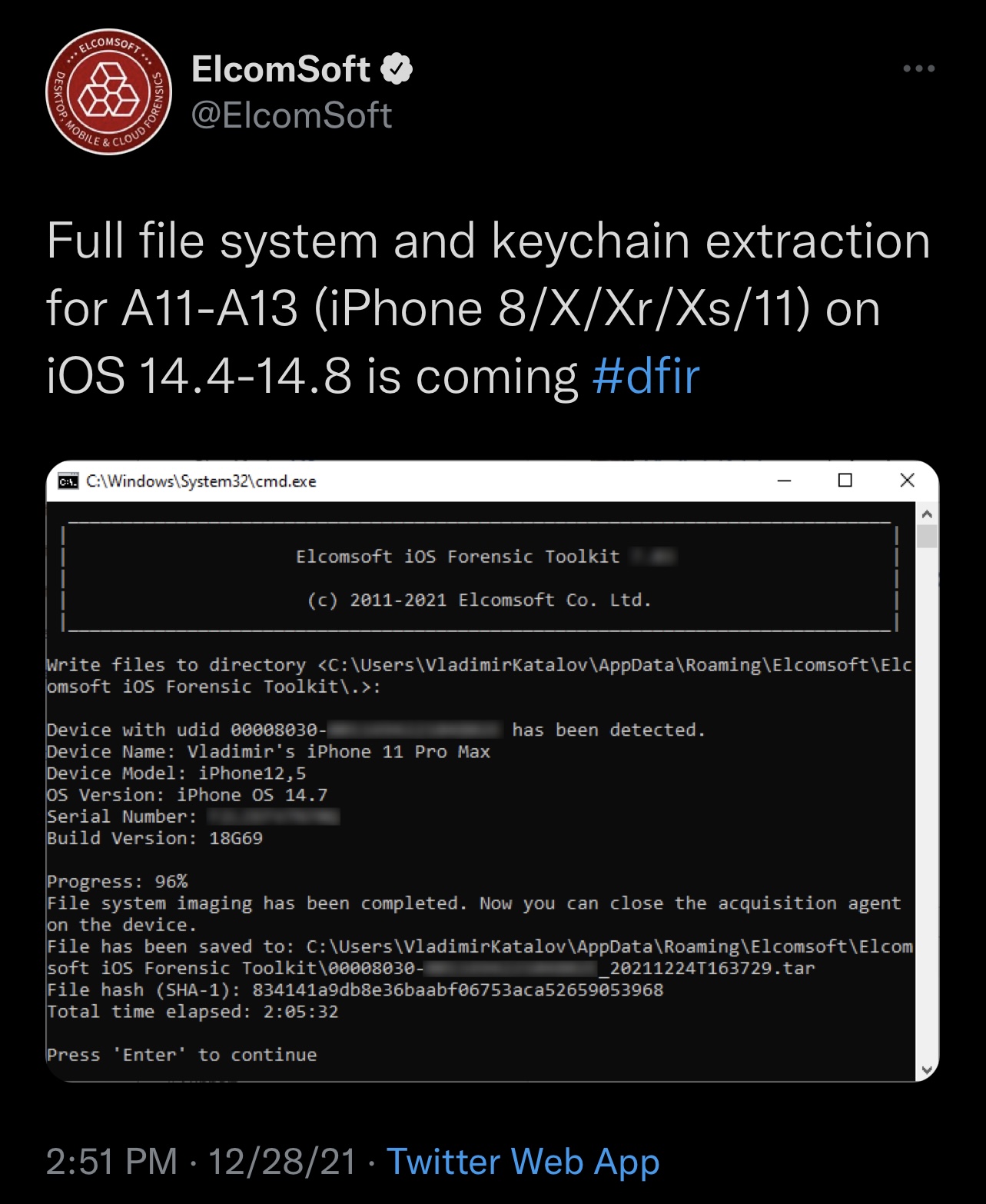
Digital forensic toolkits such as this one permit an attacker to conduct forced file system and keychain data extraction on any supported handset. They are frequently used by law enforcement during investigations when they involve passcode-protected devices.
Because the tool grants the user full file system access, this would mean that it utilizes an exploit to bypass encryption securities and provide access to the root file system. Similar methods are used by jailbreak tools to provide root access to the end user, however this is an instance where exploits are used for Digital Forensics & Incident Response (DFIR), a different concept and exploit utilization entirely.
A Twitter user appeared to respond to the announcement and @ElcomSoft confirmed they have no plans to release a jailbreak based on the exploit used by their forensic toolkit. This seems to imply that the exploit is powerful enough to be used for jailbreaking, but that the firm will keep their exploit to themselves as it’s a part of their business model to do so.
Forensic toolkits like this one are usually sold to third parties, which can include law enforcement agencies. A greater concern is when they fall into malicious hands to exploit users, much like the NSO Group incident involving a type of spyware used to surveil high-profile iPhone users like activists and journalists.
Because of the privacy implications involved, they often receive negative attention. Since the forensic toolkit grants full file system and keychain access, this means that a victim’s personal data and login credentials that have been saved to the keychain feature on the device would be compromised by the attacker.
One way to keep yourself protected from such data extractions is to keep your firmware up to date, as this tool only appears to support a subset of devices running iOS or iPadOS 14.4-14.8. Unfortunately for jailbreakers, that’s easier said than done right now unless you have a checkra1n-compatible device running iOS or iPadOS 14.8.1.
A11-A13 handsets encompass devices ranging from the iPhone 8 to the iPhone 11 Pro. Newer handsets can’t be targeted by this particular forensic toolkit.