Hacker and security researcher @pattern_F_ issued a stern reminder to avid jailbreakers Tuesday afternoon about the potential dangers of a jaw-dropping security flaw discovered in iOS & iPadOS 14.0-14.3.
The reminder, issued in the form of a remote jailbreak demonstration video shared via Twitter, demonstrates what appears to be an iPhone 12-era handset being jailbroken after visiting a website that was designed to deploy a local privilege escalation exploit remotely.
In the Tweet, @pattern_F_ shares that being on a susceptible firmware version is potentially bad, as tapping on a malicious link that utilizes an exploit like this could compromise private information stored locally on your handset:
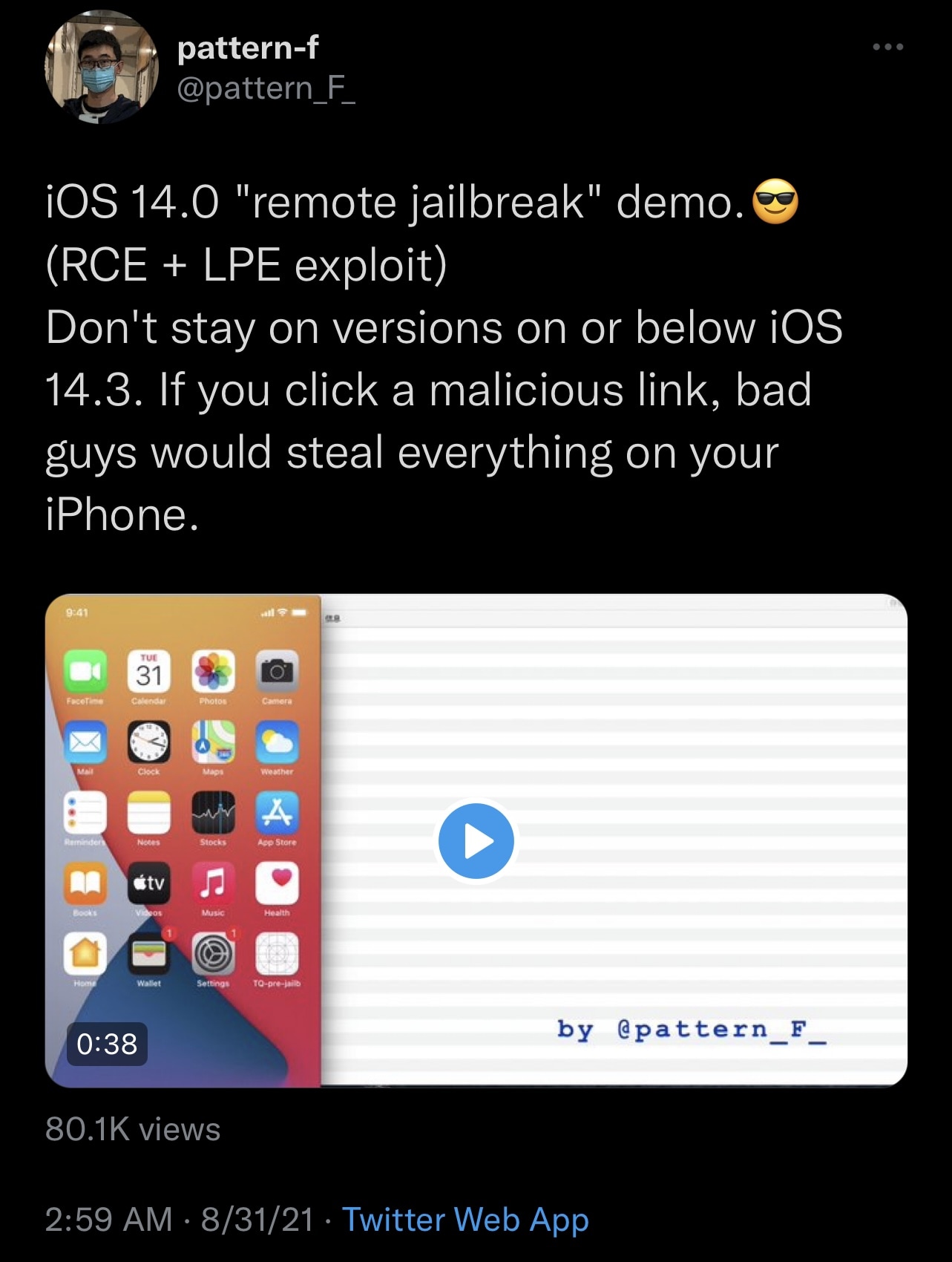
We can see from the video just how easy it could be to get tricked into tapping on a potentially malicious link or button that would then remotely execute the code needed to exploit your device. The hacker then demonstrates successful root access following the hack near the end of the video.
It’s unlikely that the remote code execution and local privilege escalation exploit demonstrated by @pattern_F_ will be released to the general public in leu of the security implications that it would have for users, but that doesn’t mean that malicious hackers aren’t already aware of similar ways to exploit the affected versions of iOS and iPadOS. Still, it’s fairly impressive to see that @pattern_F_ managed a fully remote jailbreak after harnessing the method.
It’s worth noting that some jailbreakers can’t upgrade from iOS or iPadOS 14.0-14.3 without losing their jailbreak. That’s because tools such as Taurine and unc0ver don’t yet support newer versions of Apple’s mobile operating systems. Checkra1n users, on the other hand, have a lot more flexibility to move between firmware versions as this jailbreak is based on a hardware-based bootrom exploit called checkm8.
A potential fix?
Jailbreakers currently on iOS or iPadOS 14.0-14.3 who don’t have any way of upgrading their firmware without losing their jailbreak fortunately have the option to install a third-party patch dubbed itmsBlock by @tihmstar. This patch is available on GitHub and can offer additional protection against attacks like the one demonstrated in the video if you’re not too keen on updating from a jailbroken installation of iOS or iPadOS.
If you’re not jailbroken and don’t intend to jailbreak, but you’re using iOS or iPadOS 14.0-14.3 for whatever reason, then it might be a good idea to consider updating your firmware to ensure the security of your device.
Are you impressed by the remote code execution capabilities demonstrated by @pattern_F_, or are you horrified by the idea that a malicious hacker could potentially use this or a similar remote hacking method to steal data from iPhones and iPads running obsolete firmware? Be sure to let us know in the comments section down below.