The quest to pwn the Apple Watch is one that has received oodles of attention over the years, and while the concept is most certainly possible, it hasn’t quite reached the level of fruition that most jailbreakers would expect – especially when compared with the jailbreak offerings for iPhones and iPads.
Much of this has to do with the uncertainty of an Apple Watch jailbreak’s usefulness in addition to concerns related to restoring the Apple Watch’s firmware in the event of catastrophic errors (respring loops, etc.), but that hasn’t stopped some jailbreak developers from dabbling with the idea.
The most recent example of Apple Watch pwnery comes from Odyssey Team lead developer CoolStar, who just over the weekend shared some rather exciting screenshots in the Sileo / Taurine / Odyssey Discord channel of the cicuta_verosa exploit being used to pwn the Apple Watch:
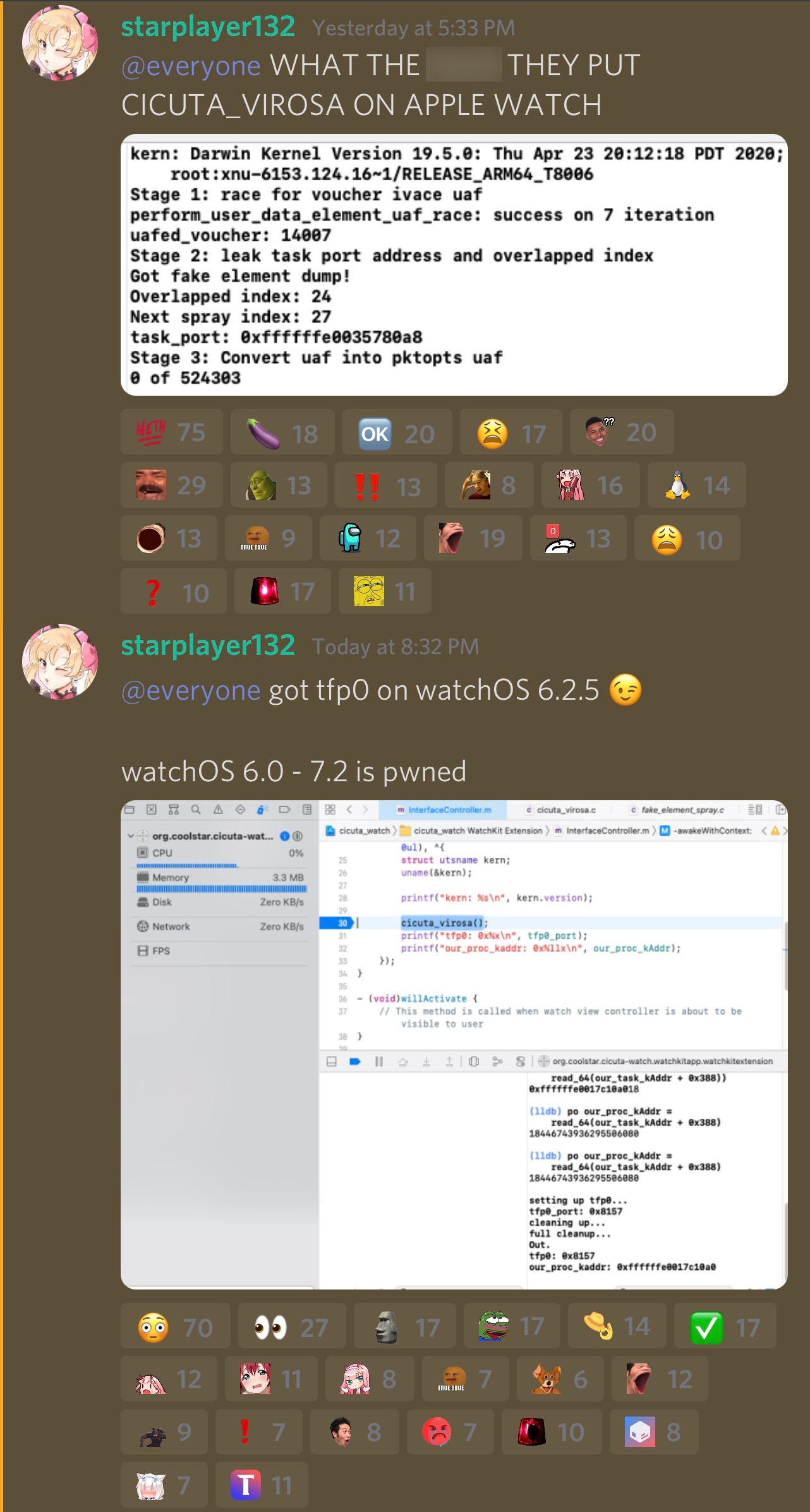
Based on CoolStar’s comments in concert with the screenshots that were shared, we can discern that cicuta_verosa supports watchOS 6.0 through 7.2, and that in this particular instance, tfp0 was successfully achieved on CoolStar’s Apple Watch running watchOS 6.2.5.
Notably, cicuta_verosa is the very same exploit actively utilized by the Taurine jailbreak for iOS & iPadOS 14.0-14.3.
As for achieving tfp0, this effectively translates to a kernel task port, which means that the exploit user can achieve arbitrary reads and writes to the device’s kernel memory. Jailbreaks depend heavily on these capabilities for a multitude of reasons.
It will indeed be interesting to see what materializes from this past weekend’s achievements, especially given the obscurity of the concept behind Apple Watch pwning and what it might be used for. We will continue monitoring the situation for updates and keep our readers apprised should anything substantial happen.
Would you ever jailbreak your Apple Watch if given the opportunity? Share why or why not in the comments section down below.