Yesterday, we highlighted a proof-of-concept iPhone charger by researchers at the Georgia Institute of Technology which can be used to install malware on your non-jailbroken iPhone, iPod touch or iPad in under a minute. It’s another example of the cat and mouse game played between hackers and Apple.
Today, we received word of an iOS security flaw which can be exploited to break the password required to restrict access to apps, content and features on your iPhone, iPod touch or iPad…
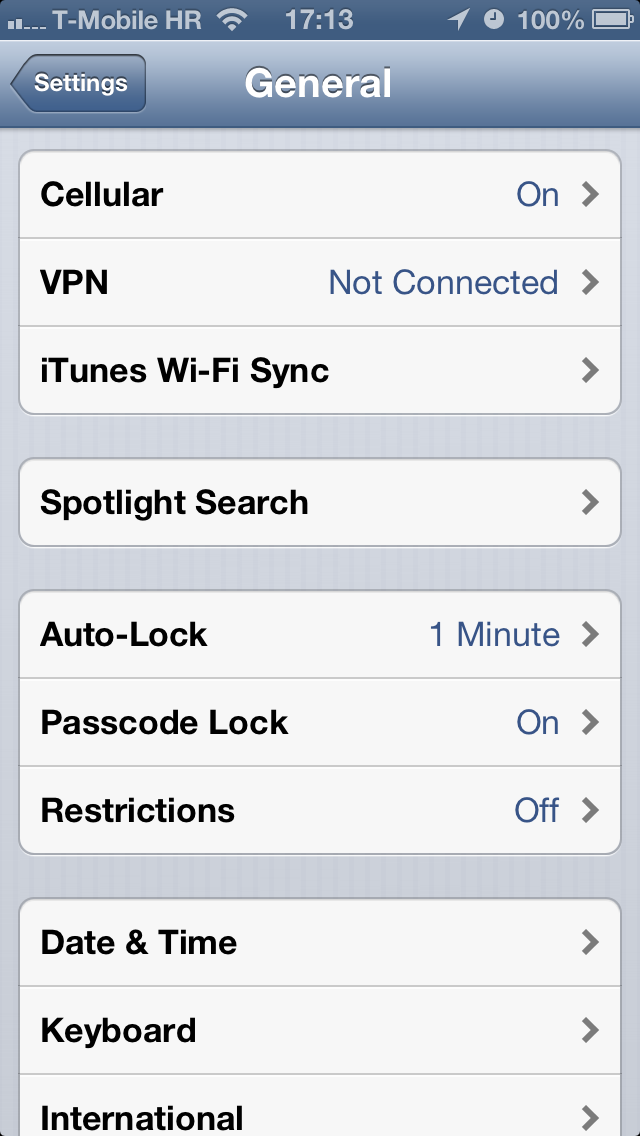
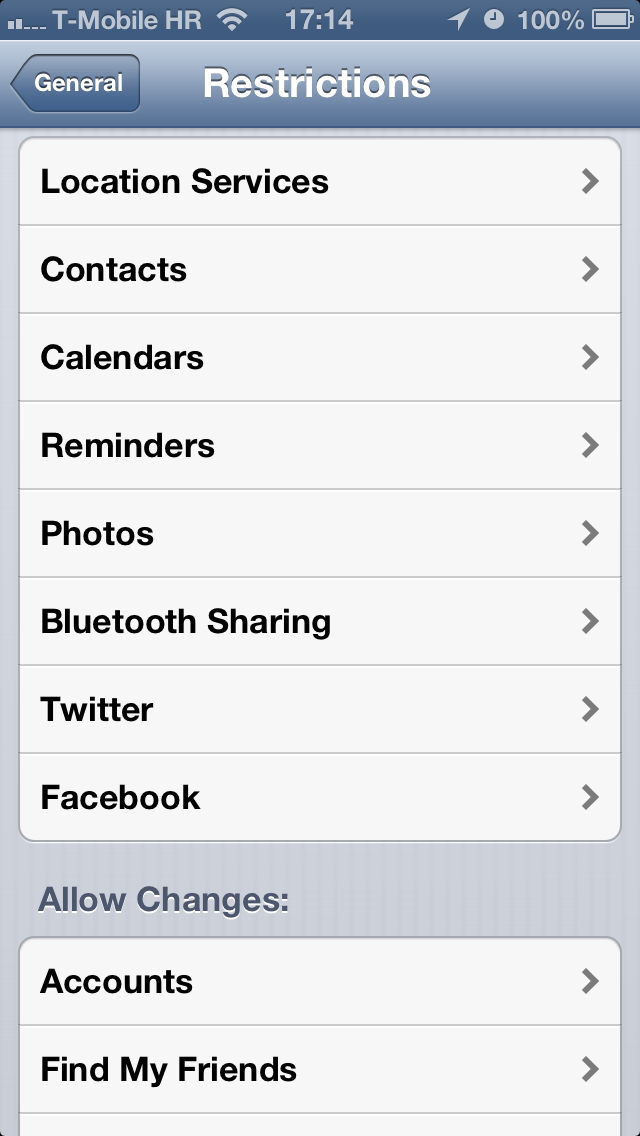
Simply put, the exploit can be used to turn off the restriction passcode in Settings > General > Restrictions, assuming it was enabled in the first place.
The French blog iGen.fr passes along a report by Peter Dandumont outlining gaining access to restricted apps. Restricted iOS apps are managed through the General > Restrictions section of the Settings app.
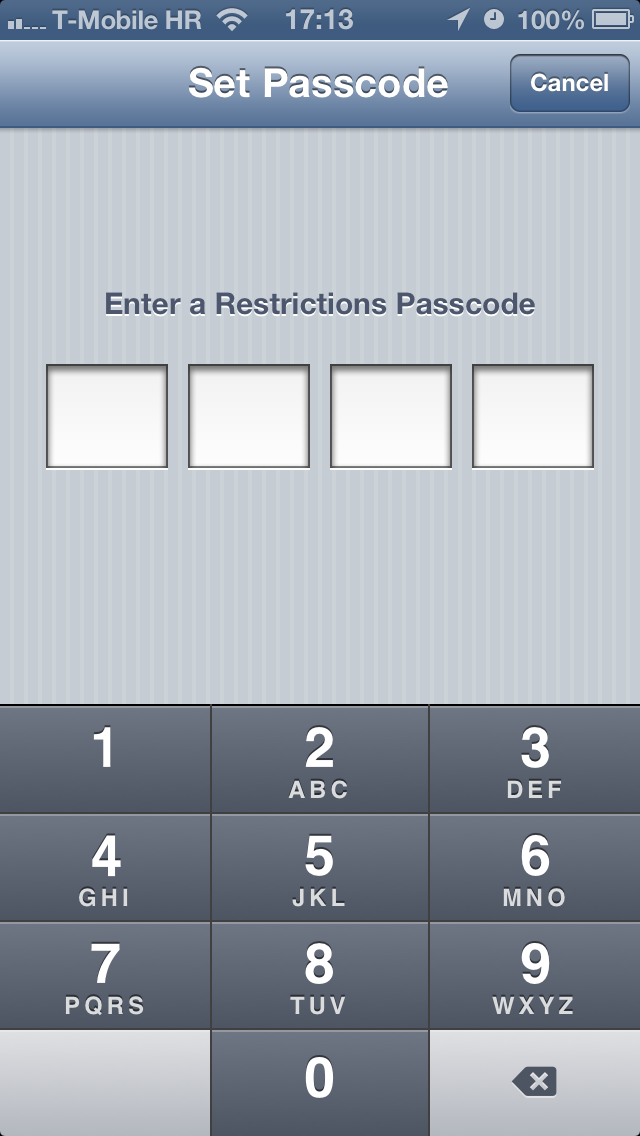
Enabling or disabling the feature is only possible with a custom four-digit passcode, which is different than the one you enter at the Lock screen.
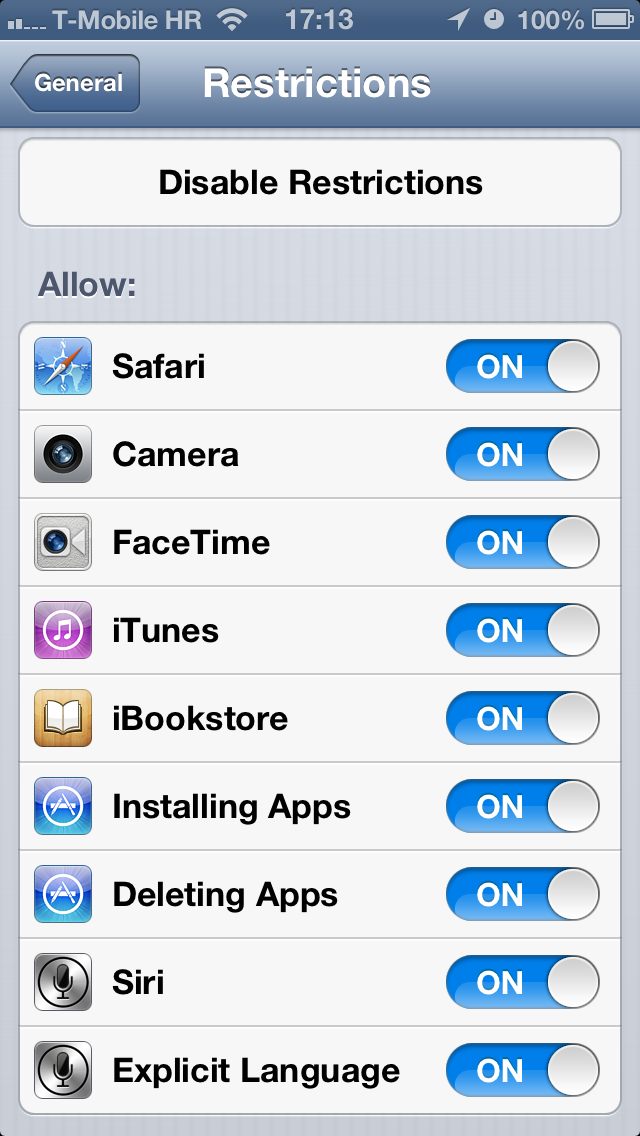
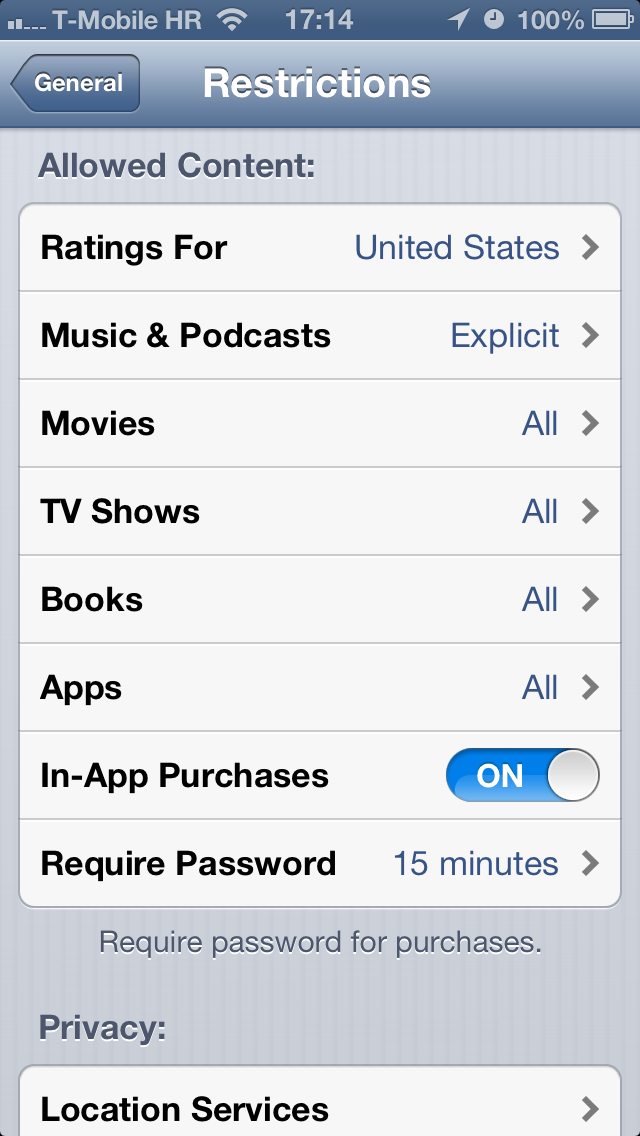
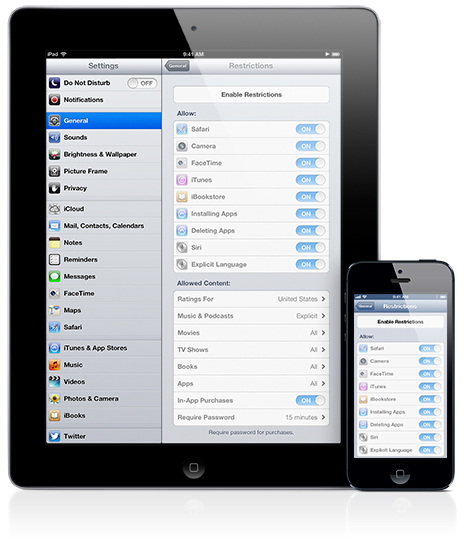
As a quick backgrounder, Apple developed these restrictions so parents could limit the use of certain applications (Safari, Camera, FaceTime, iTunes, iBookstore), features (installing apps, deleting apps, Siri and explicit language for Siri) and content (including ratings, music and podcasts, movies, TV shows, books, apps and in-app purchases) on iPhone, iPod touch or iPad devices.
Dandumont discovered that hooking up a Teensy 3.0 card which emulates a USB keyboard to an iPad through Apple’s iPad Camera Connection Kit opens doors to brute-forcing your way into restricted iOS apps.
He details the security oversight which makes this hack possible:
When you hit several times a wrong code, the virtual keyboard is locked for 1 minute, 5 minutes, 15 minutes and 60 minutes after each bad try. But if ever a physical keyboard is used, it is always possible to try a code.
Here’s a video of the exploit.
The method apparently works with any conventional keyboard, including a Bluetooth one. Of course, you’d have to write an app to generate the right set of codes for brute-force attacks.
Because iOS Restrictions are protected with a four-digit numerical passcode, brute-forcing one’s way into someone else’s Settings > General > Restrictions may take anywhere from a few minutes to a few hours.
In the worst case, Dandumont says breaking the passcode takes a little more than eight hours. Again, the method does not compromise your master password – it’s for turning off the restriction passcode to gain access to iOS Restrictions.
Dandumont filed a bug report with Apple and won’t post the code until the firm squashes the bug. Now that he publicized the exploit, Apple should be able to fix this flaw with a simple firmware update.