A string of bad news for Apple continues with a revelation published Thursday on The Daily Dot that London-based computer security expert Ibrahim Balic gave Apple a heads-up about a vulnerability he had discovered in iCloud, but the company discounted the severity of the issue and ignore the problem for six months.
As you know, the issue blew up in a major way, becoming the topic of late-night shows, after several celebrities with weak Apple ID passwords saw their nude photographs hijacked and posted on the web.
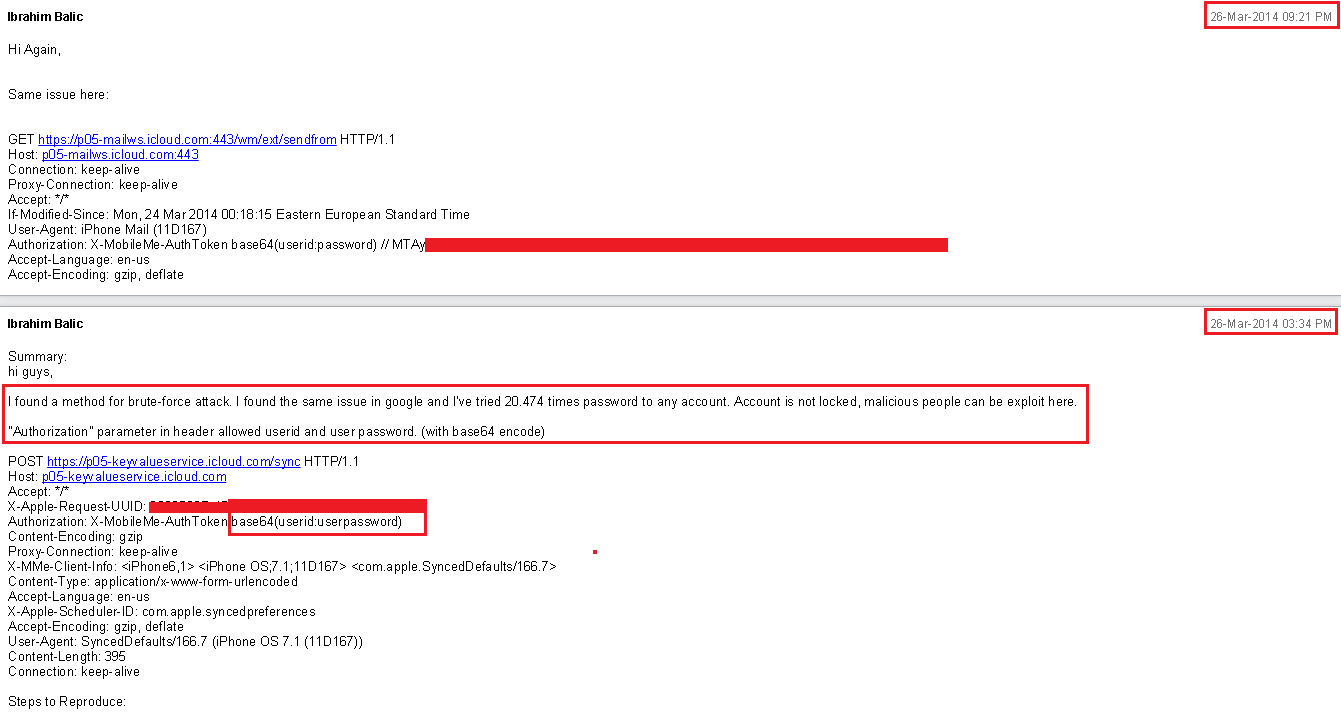
Balic reportedly cautioned Apple back in March that he had been able to use some 20,000 passwords against specific iCloud accounts. It would seem that his warnings either fell on def ear with Apple’s engineers who manage security or at least his emails were never escalated up the corporate ladder to become a priority.
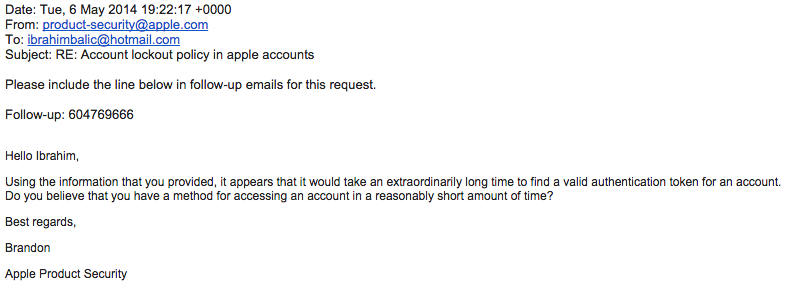
“Using the information that you provided, it appears that it would take an extraordinarily long time to find a valid authentication token for an account,” an Apple engineer wrote back to Balic. “Do you believe that you have a method for accessing an account in a reasonably short amount of time?”
Balic, who provided copies of his correspondence with Apple, is not so sure that the iPhone maker has addressed the iCloud vulnerability to this date. We actually don’t know whether or not the iCloud vulnerability Balic discovered is related to the brute-force attack that had been used on celebrities’ Apple IDs.
Hackers who leaked nude pics are thought to have used the iBrute tool to launch a brute-force attack on the Find My iPhone services, which at the time did not lock out users after multiple failed attempts to guess the password (Apple has since rectified this obvious oversight).
Apple itself said in a statement that the breach was the result of a “targeted attack” which benefited from the victim’s weak Apple ID password and the fact that they did not protect their account with two-step verification.
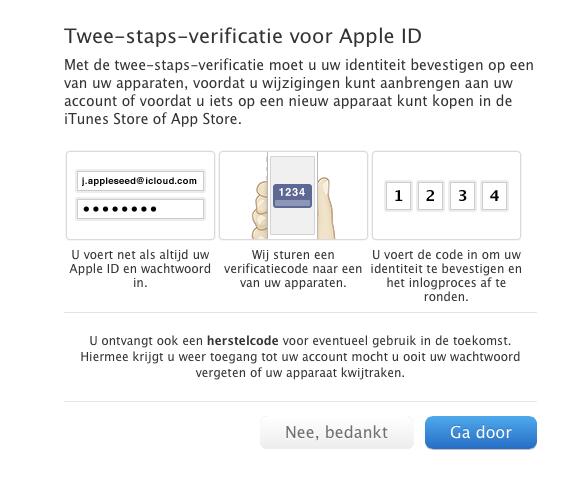
The Cupertino firm recently expanded the use of two-step verification to further protect iCloud accounts in the aftermath of the scandal.
The opt-in feature boosts you security by requiring you to enter a four-digit code sent by text message or pushed to your device each time you log in to your Apple ID account on the web, to iCloud.com or try to use a new device authorized with the same Apple ID/iCloud account.
You are wholeheartedly encouraged to enable two-step verification for your Apple ID by following our handy tutorial.