While the dust is far from settled on the nasty SSL bug found in iOS last week, a new security flaw in the mobile OS has been brought to light. The new flaw makes it possible for attackers to covertly log every touch a user makes, including keyboard and Touch ID presses.
Researchers at security firm FireEye made the discovery, saying in a blog post that the gap exists within iOS’ multitasking feature that allows for the background monitoring, and it can be exploited via a malicious app install or remotely via a separate app vulnerability…
Here’s the blog post via ArsTechnica:
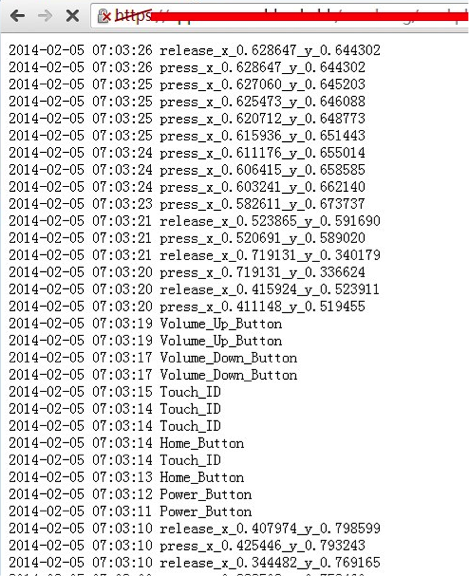
“We have created a proof-of-concept “monitoring” app on non-jailbroken iOS 7.0.x devices. This “monitoring” app can record all the user touch/press events in the background, including, touches on the screen, home button press, volume button press and TouchID press, and then this app can send all user events to any remote server, as shown in Fig.1. Potential attackers can use such information to reconstruct every character the victim inputs.
Note that the demo exploits the latest 7.0.4 version of iOS system on a non-jailbroken iPhone 5s device successfully. We have verified that the same vulnerability also exists in iOS versions 7.0.5, 7.0.6 and 6.1.x. Based on the findings, potential attackers can either use phishing to mislead the victim to install a malicious/vulnerable app or exploit another remote vulnerability of some app, and then conduct background monitoring.”
Shortly after publishing the post, FireEye posted a separate brief that was quickly removed. But according to an RSS reader cache the firm claimed that it “delivered a proof-of-concept app through the App Store that records user activity and sends it to a remote server.”
The bad news is, the vulnerability has been confirmed to exist on non-jailbroken iPhones and iPads running iOS versions 7.0.4, 7.0.5, and 7.0.6, as well as those running on 6.1.x. The good news is, FireEye says that Apple is aware of the problem and is working on a fix.