Just a couple of weeks ago, we showed you an add-on for MacDirtyCow devices called Plampy UI by YangJii that enabled a spiffy new look and feel for the Control Center user interface by way of new icon glyphs.
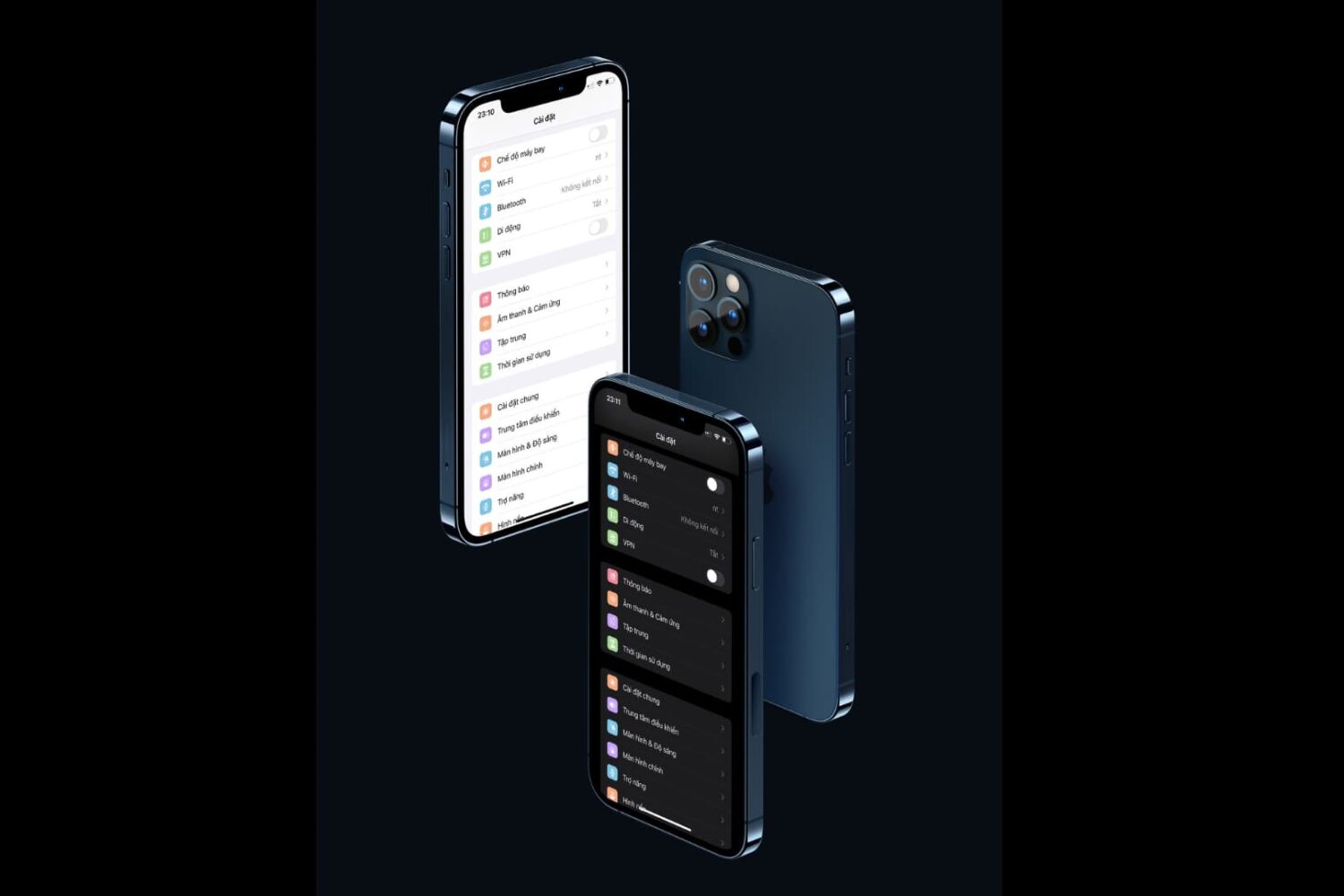
Just a couple of weeks ago, we showed you an add-on for MacDirtyCow devices called Plampy UI by YangJii that enabled a spiffy new look and feel for the Control Center user interface by way of new icon glyphs.
Misaka, the premier package manager app for devices utilizing the MacDirtyCow exploit on iOS 15.x-16.1.2, received another update this week, officially bringing it up to version 1.9.0.
The Misaka package manager app for MacDirtyCow exploit-susceptible devices running iOS or iPadOS 15.0-16.1.2 received yet another update this week, this time bringing it up to version 1.8.9 beta.
Looking for MacDirtyCow add-ons for your iOS or iPadOS 15.0-16.1.2 device that will let you customize your handset outside of the stock parameters? If so, then you might take an interest in one called NoVulnTools2 by iOS developer tyler1029.

System sounds aren’t readily configurable on non-jailbroken iPhones and iPads, except maybe the ringtone and text tone, but with a MacDirtyCow exploit-based add-on called SoundManager by iOS developer EPOS, you can do this even without a jailbreak.
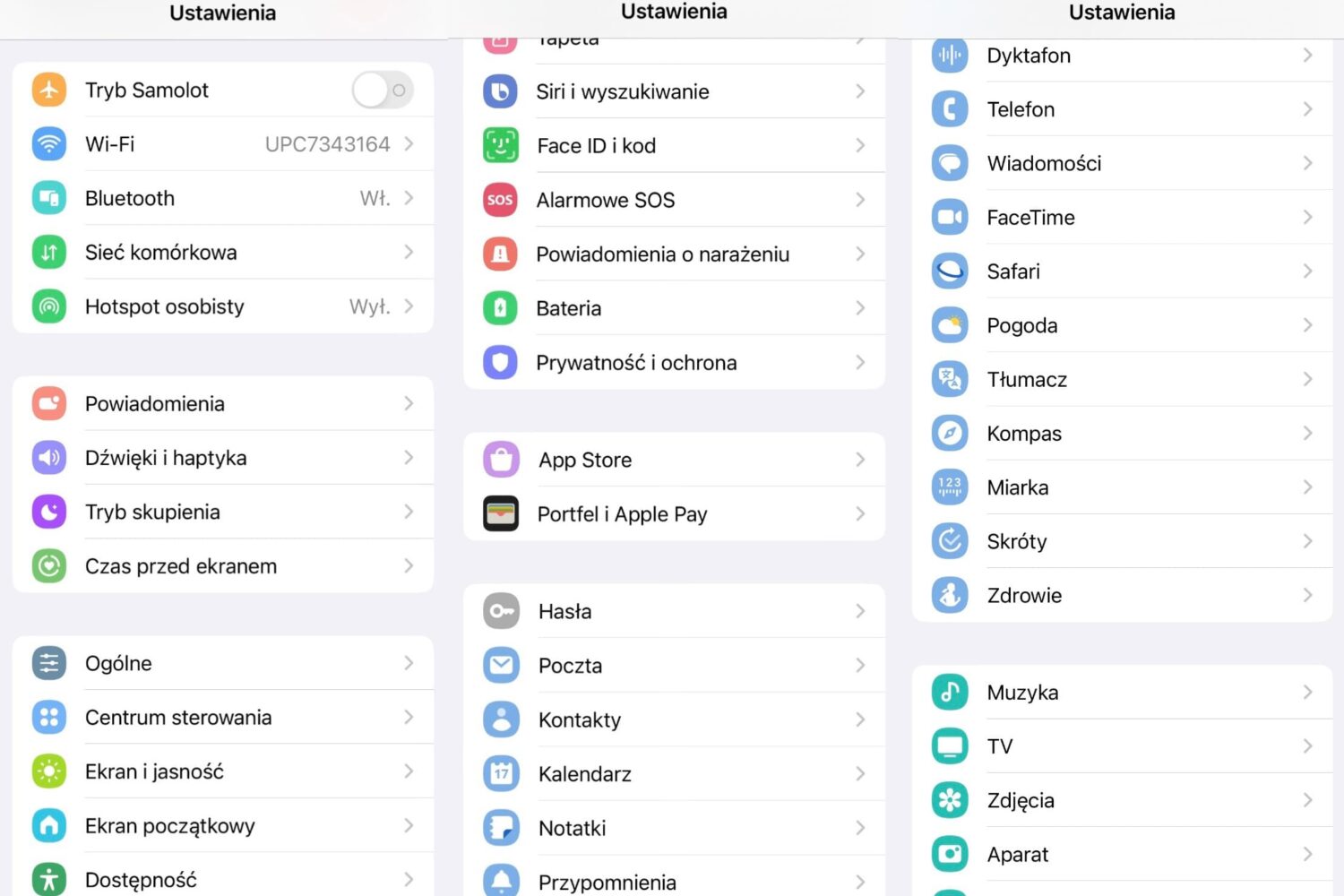
How would you like it if your iPhone’s Settings app icons took the appearance of a Samsung Android device? Even better… what if you could do that without jailbreaking? Interested yet?
The Settings app is the primary place where iPhone users can change device behavior and options, but depending on your tastes, you might find the organization to be less than optimal.
Just last week, we showed you a package manager app for MacDirtyCow exploit-susceptible devices called Misakathat could be used to install add-ons for customizing the iOS user interface, and we walked you through the process to install and use it.

Anyone that has a Face ID-equipped iPhone and runs a MacDirtyCow-susceptible firmware between iOS 15.0-16.1.2 can take advantage of a checkra1n-inspired Face ID glyph animation that replaces the traditional animated Face ID padlock when authenticating themselves.
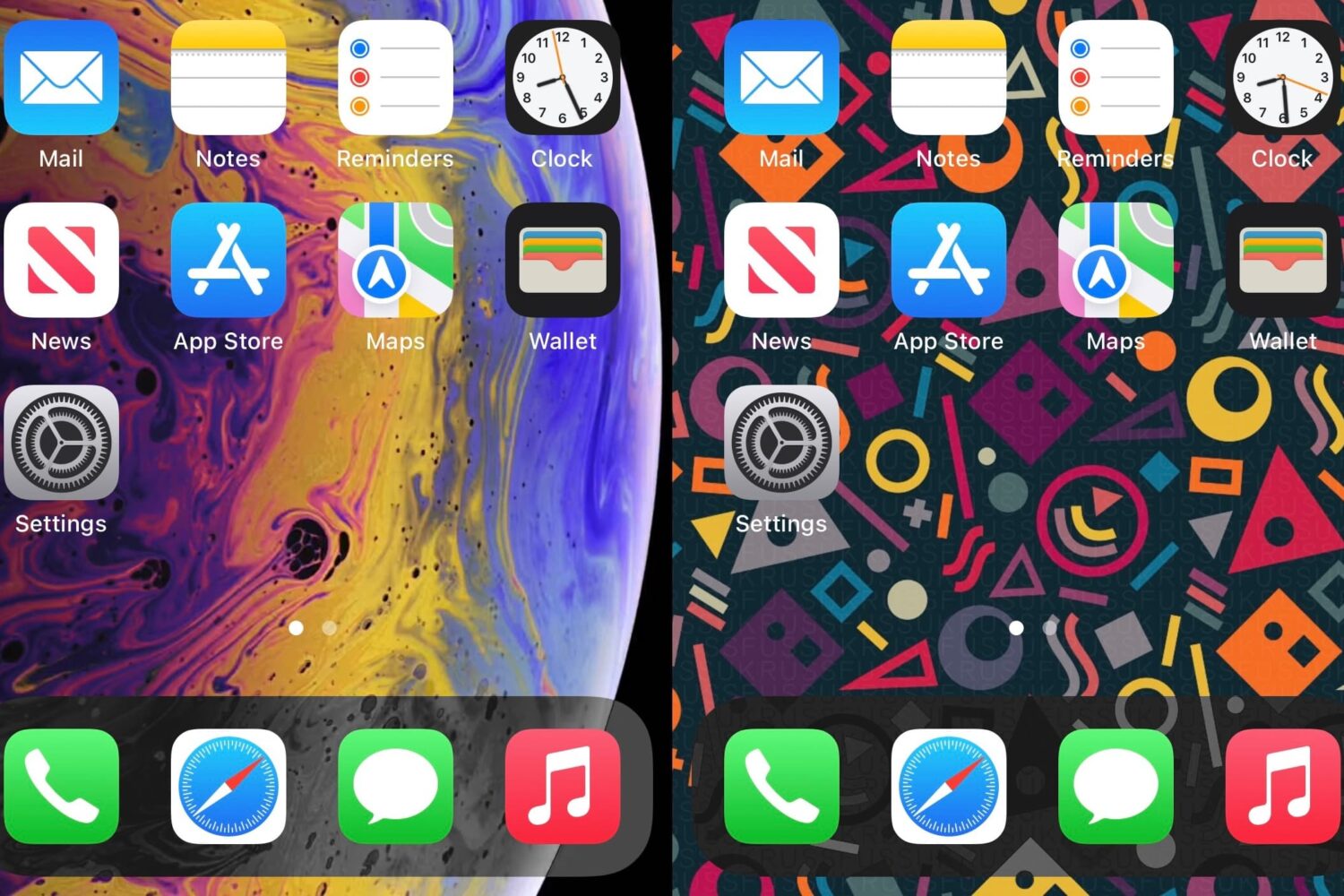
Whether you’re jailbroken or not, if you have a firmware supporting the MacDirtyCow exploit, namely iOS or iPadOS 15.0-16.1.2, then you can take advantage of add-ons that modify the appearance and behavior of your iPhone or iPad.
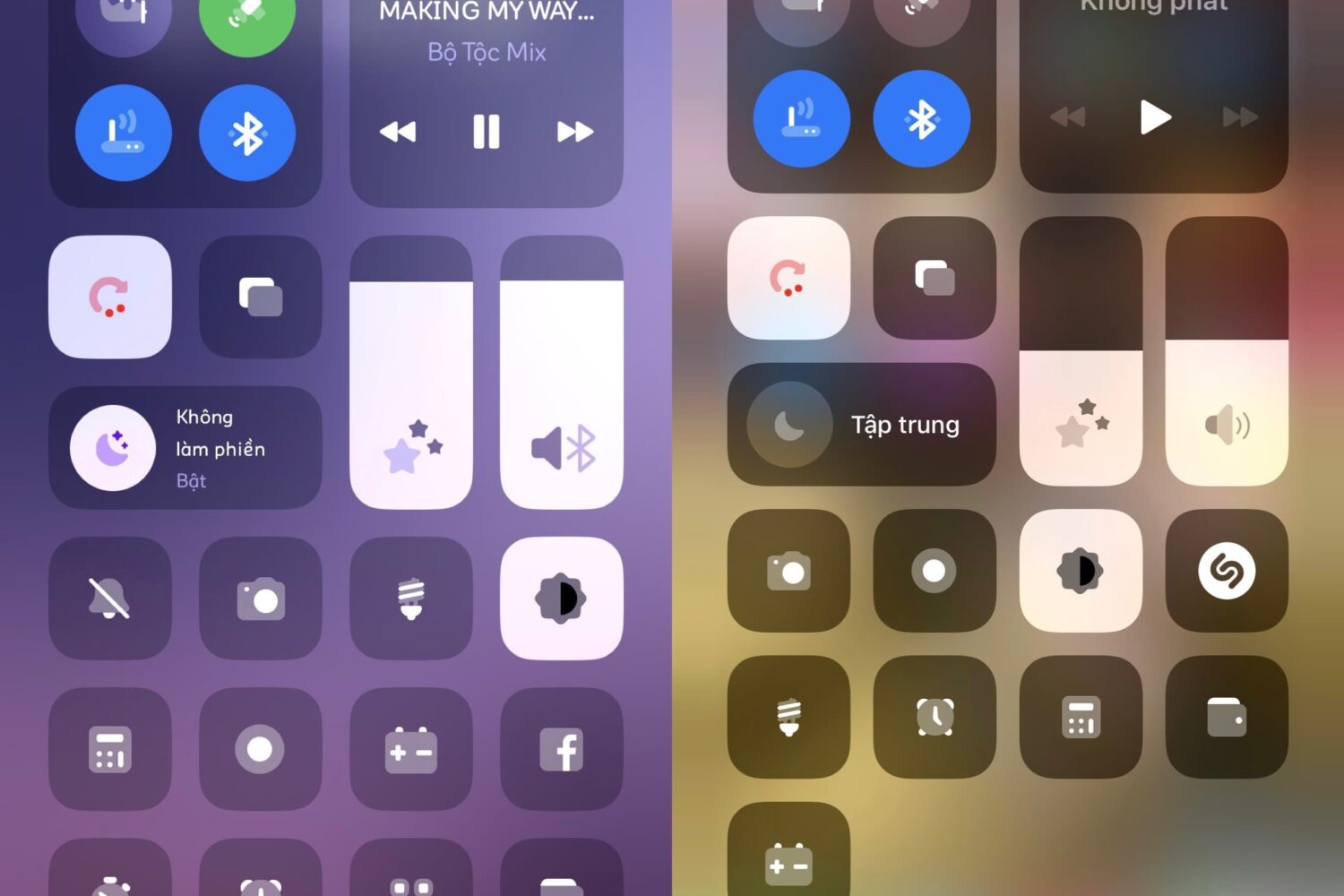
If you’ve got a device running MacDirtyCow-vulnerable firmware, such as iOS or iPadOS 15.0-16.1.2, then you might be excited to learn of a Control Center add-on called Plampy UI Control Center by iOS developer YangJiii.
Cowabunga, a popular all-in-one UI customization app for use with TrollStore on iOS 14.0-15.4.1 devices or the MacDirtyCow exploit on iOS 15.0-16.1.2 devices by iOS developers sourcelocation and leminlimez, was updated to version 8.0.0 this weekend with a slew of improvements that users will appreciate.