Lulz Security, commonly referred to as LulzSec, has been causing all sorts of chaos around the web for the past few months. The team of hackers is responsible for a number of recent attacks, including posting a fake news story on PBS.com and knocking the CIA's website offline.
Though their recent attacks have been fairly harmless, their most recent break-in has made a lot of folks nervous. Last Thursday, LulzSec published more than 700 confidential documents stolen from the Arizona Department of Public Safety (DPS).
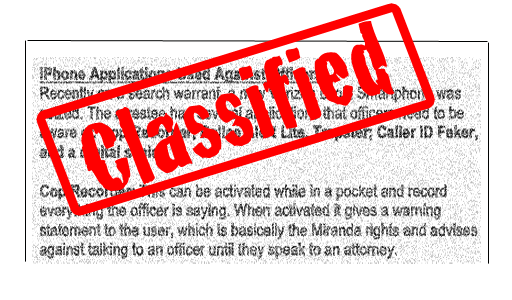
The 440MB of data included emails, handbooks, images and other sensitive files, some of which revealed the identities of Arizona Law Enforcement. In sifting through the data, Techland uncovered a form particularly interesting to iDB entitled "iPhone apps- used against officers.doc"