According to a post published yesterday on the official YouTube Engineering and Developers Blog, 97 percent of YouTube's traffic is now encrypted since the Internet giant began rolling out encryption using HTTPS two years ago. Encrypted traffic increases your security by garbling the data as it travels from servers to your computer, and vice versa, in order to make these transmissions unreadable to rogue parties without an encryption key.
Encryption
Facebook Messenger starts testing end-to-end encryption with Secret Conversations
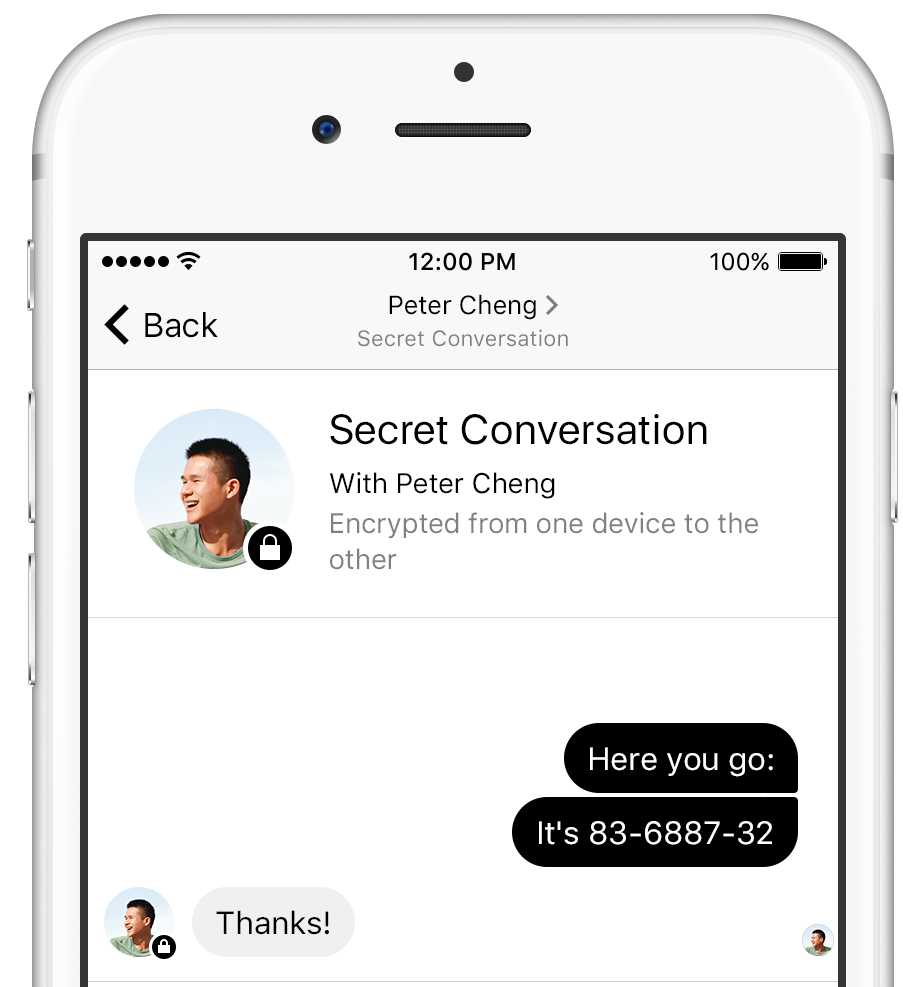
The Guardian reported more than a month ago that Facebook would be rolling out end-to-end encryption for chats in Messenger. Friday, the social networking firm announced that it's begun testing the new feature, dubbed Secret Conversations.
An opt-in feature, the new option within the mobile Messenger app for iOS and Android was designed to better support conversations about sensitive topics with end-to-end encryption.
Has Apple gone mad? More iOS 10 parts left unencrypted in beta 2
As you know, security experts were baffled realizing that the iOS 10 kernel in beta 1 was not encrypted. Apple argued it was no big deal because the kernel contained no user data so the company had left it unencrypted intentionally in order to increase general system performance, in their own words.
But Apple didn't stop there.
As first discovered by prominent jailbreak developer and iPhone hacker, MuscleNerd, iOS 10 beta 2 actually leaves more parts of the operating system unencrypted.
What's going on here?
Apple explains why iOS 10 kernel is unencrypted
Following the discovery by MIT Technology Review that the kernel in iOS 10 beta is unencrypted, Apple has gone on the record to explain why that's the case. Speaking with Dave Mark of The Loop, an Apple spokesperson has officially confirmed that the decision was intentional.
Now, some security experts speculated that leaving the iOS 10 kernel unencrypted would aid anyone, nefarious users included, looking for security weaknesses in the iOS software.
Apple explains why such fears are unfounded.
iOS 10 beta kernel is unencrypted, but why?
MIT Technology Review has discovered that the kernel in iOS 10 beta is unencrypted, making it a lot easier for technology-minded users, jailbreak developers and the like to take a peek under iOS's hood and pinpoint any potential vulnerabilities.
For those wondering, kernels in all prior iOS betas used to be encrypted. Is this a bold move meant to help strengthen security in iOS 10 or will this decision actually introduce further security risks and open new attack vectors for hackers to exploit?
Facebook Messenger said to be rolling out opt-in encryption in the coming months

After WhatsApp and Viber both introduced end-to-end encryption last month, Facebook Messenger will become the next major messaging app to roll out this essential security feature, reports The Guardian.
Although end-to-end encryption on Messenger will be framed as an optional feature that users will need to manually enable, it will ensure that the contents of communications are hidden from eavesdroppers and that the identities of the participants are concealed.
Apple brings back security expert Jon Callas following FBI dispute

Apple this month brought back software engineer and top expert in practical cryptography Jon Callas, reports Reuters. The move follows Apple's high-profile battle with the FBI, and amidst a growing war between governments and tech firms over encryption.
Callas worked at Apple in the '90s, and again between 2009 and 2011, when he designed encryption to protect data stored on Mac computers. He rejoined the company in May, to help add more powerful security features to its wide range of consumer products.
FBI paid more than $1.3 million for San Bernardino iPhone hack

FBI Director James Comey said on Thursday that the agency paid more to break into the San Bernardino shooter's iPhone than he'll make in the remaining 7+ years of his tenure. Reuters crunched the numbers, and that suggests that the FBI paid more than $1.3 million for the hack.
That seems like a lot of money for a tool that doesn't work on the iPhone 5s or newer, but speaking at the Aspen Security Forum in London today, the Director said that he believes it was worth it. And of course the FBI will be able to use the tool in other case involving older iPhones.
Apple says it refused Chinese demand for iOS source code

Apple declined to provide Chinese officials with access to iOS source code, General counsel Bruce Sewell said on Tuesday at a subcommittee hearing on encryption. "We have been asked by the Chinese government. We refused."
Sewell said the request had come in the last two years, and noted several times that Apple has not cooperated with China on that level. Some lawmakers have questioned whether or not Apple has given the country special treatment.
Privacy-enhanced Viber for iPhone lands with end-to-end encryption, hidden chats and more
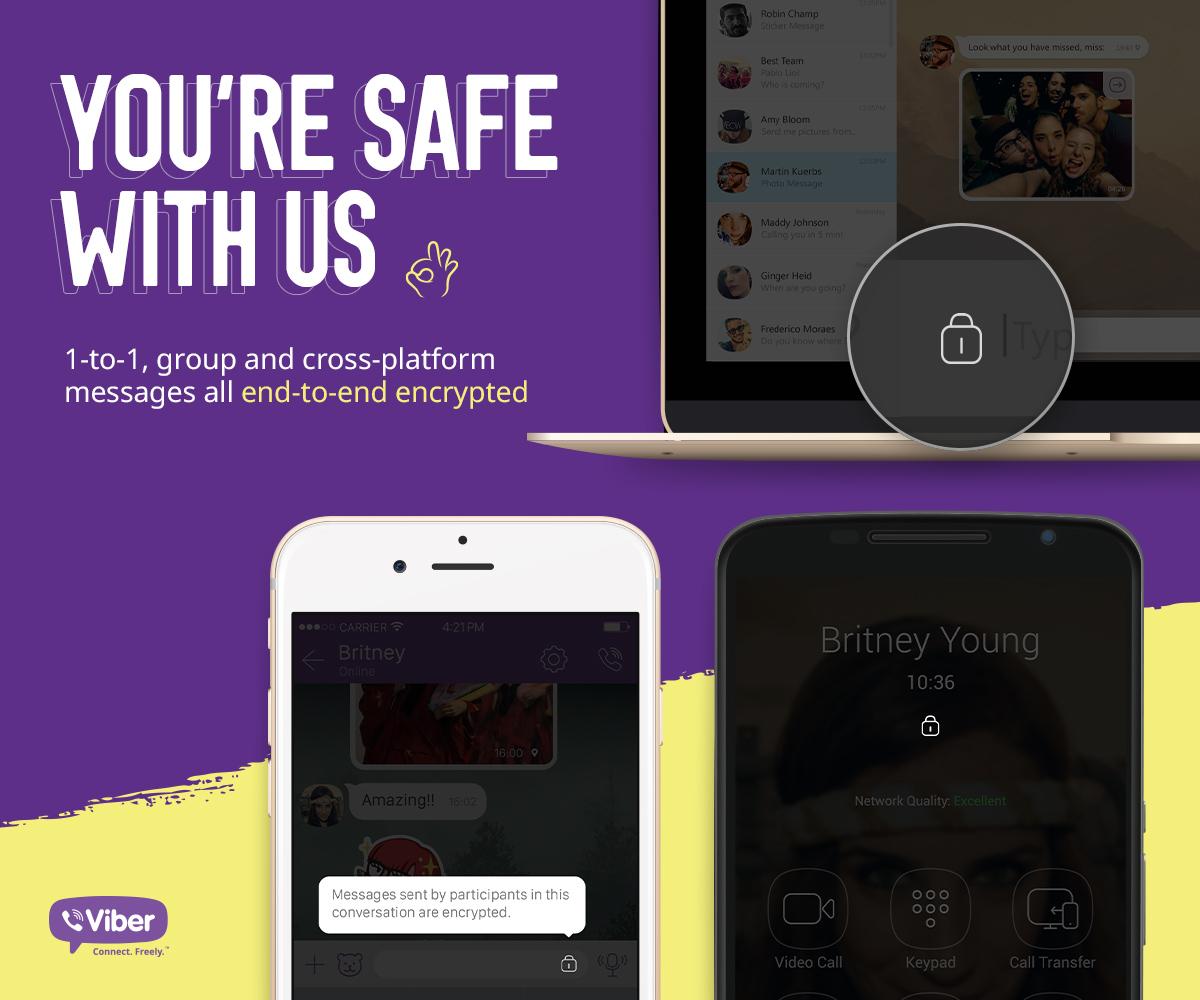
Two weeks after rival WhatsApp announced that chats on its platform are protected from eavesdropping with end-to-end encryption, the popular messaging app Viber on Tuesday released a privacy-enhanced edition of its iPhone and iPad app.
Bumped to version 6.0, messages you send and receive through Viber are now protected with end-to-end encryption, as indicated by the new padlock icon, and you can also hide away specific chats.
Canadian police have had BlackBerry’s global decryption key since 2010

Canadian police have been in possession of a BlackBerry's global decryption key since 2010, reports Vice. The site says recently released court documents reveal that the key was used in a criminal investigation to intercept over 1 million BBM messages.
The documents were made public after members of a Montreal crime syndicate pleaded guilty to their role in a 2011 murder, and they shine some light on the extent that BlackBerry, as well as telco giant Rogers, is willing to cooperate with investigators.
Mobile forensics firm that unlocked terrorist’s iPhone 5c thinks it can hack iPhone 6

Mobile forensics firm Cellebrite that helped the United States Federal Bureau of Investigation bypass the passcode protection on the San Bernardino shooter's iPhone 5c is adamant that it can also work around Apple's security protections and hack into an iPhone 6, CNN reports.
Italian father Leonardo Fabbretti, who wanted to see the photos stored on his dead son Dama's iPhone but was told by Apple that it was impossible to get into the device without a passcode, has now met with Cellebrite executives who have been working on accessing the files.