Unless you’ve been living under a rock for the past couple of years, you would have caught wind about two powerful kernel-level exploits that have been used by iOS developers to release hacks and add-ons for non-jailbroken devices.

Those kernel-level exploits have been referred to as MacDirtyCow (MDC) for iOS & iPadOS 15.0-16.1.2 and kernel file descriptor (KFD) for iOS & iPadOS 16.0-16.6 beta. But what if we told you that another exploit just like these had been discovered for newer version(s) of Apple’s mobile device firmware?
That indeed appears to be the case, at least citing posts shared via X (formerly Twitter) over the weekend by both sourcelocation and LeminLimez — two prominent developers of MacDirtyCow and kfd exploit-based add-ons.
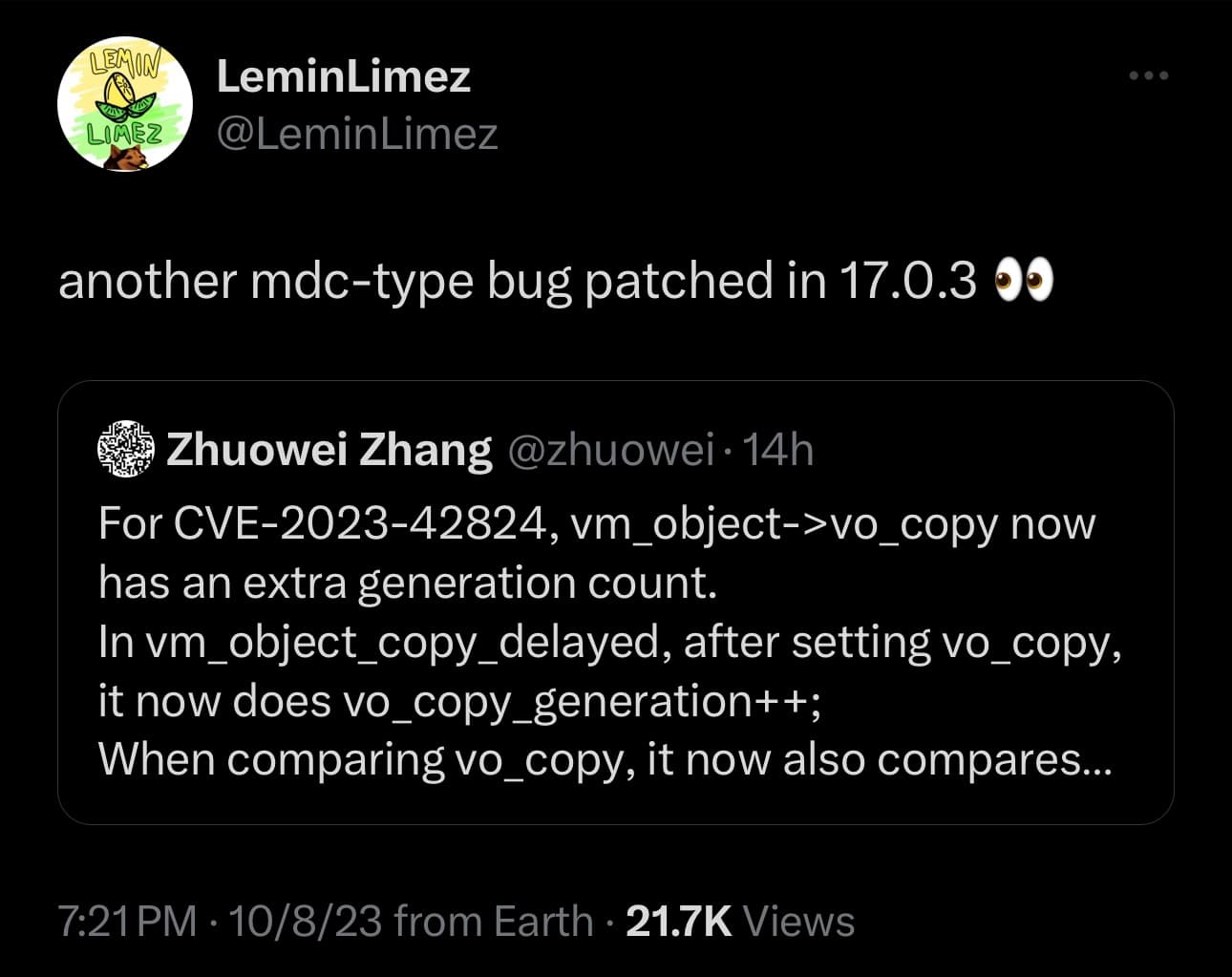
The both of them shared a post originally put up by security researcher Zhuowei Zhang, who cited a bug called CVE-2023-42824, and included context indicating that yet another MacDirtyCow and kfd-like bug has been patched in iOS & iPadOS 17.0.3. This would mean that it works in iOS & iPadOS 17.0.2 and earlier.
Taking a closer look at Apple’s “About the security content of iOS 17.0.3 and iPadOS 17.0.3” page, we learn more about the nature of this bug:
Impact: A local attacker may be able to elevate their privileges. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.6.
So what does all of this mean? In essence, it means that even if we don’t see another jailbreak anytime soon, it’s certainly possible that there could be another season of non-jailbroken package managers such as Misaka, Picasso, and PureKFD that serve as vehicles for system customization.
As for the recommended firmware to be on, any firmware from iOS or iPadOS 16.5-16.6.1 or earlier is probably ideal, but the bug also impacts some for the first versions of iOS & iPadOS 17 — these may require additional techniques to get working, however.
These types of kernel exploits allow for system customization without a jailbreak because they can both read and write to kernel memory. They allow things such as passcode button and phone dialer customization, app icon theming, Apple Pay card customization, system color changing, and more…
It will indeed be interesting to see what becomes of CVE-2023-42824, especially as it could unlock system customization on more recent version(s) of iOS & iPadOS that are outside of the scope of stock iPhone and iPad options.
Are you excited? Let us know in the comments section down below.