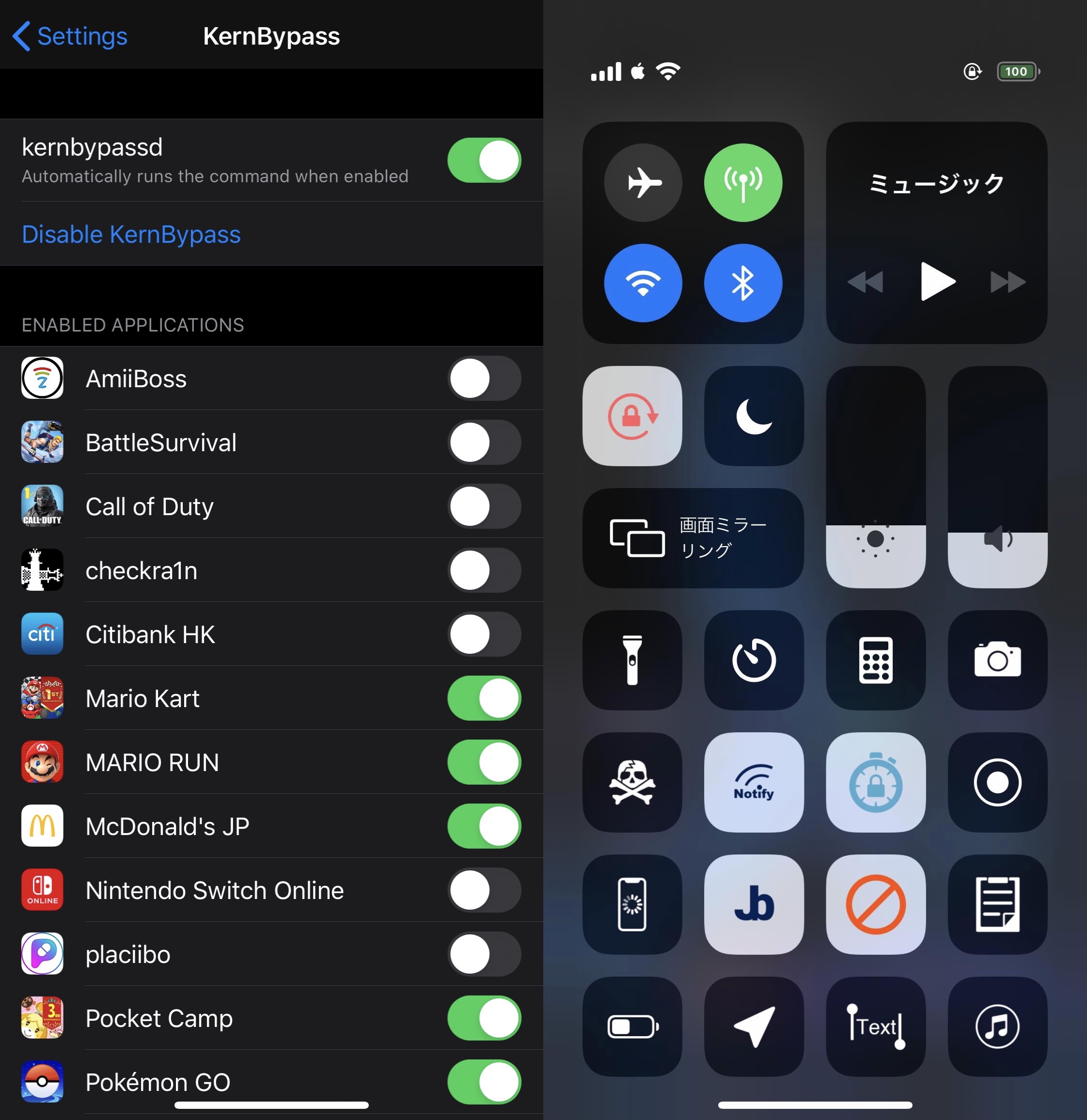
Earlier this year, iOS developer XsF1re garnered a substantial amount of attention from the jailbreak community after releasing the FlyJB kernel-level jailbreak detection bypassafter releasing the FlyJB kernel-level jailbreak detection bypass — a tool that was basically meant to amount to a way for jailbreakers to go undetected by App Store apps that would traditionally bar access to those with pwned handsets.
Soon after, XsF1re pulled the project, citing a loss of confidence, but later reinstated it as FlyJB X upon developing improvements to make the bypass more reliable. Still, it wasn’t without its shortcomings. Over the weekend, however, iOS developer Ichitaso updated his own kernel-level jailbreak detection bypass dubbed KernBypass (unofficial) to version 0.0.5, and from what we can gather, it just might be slightly superior.
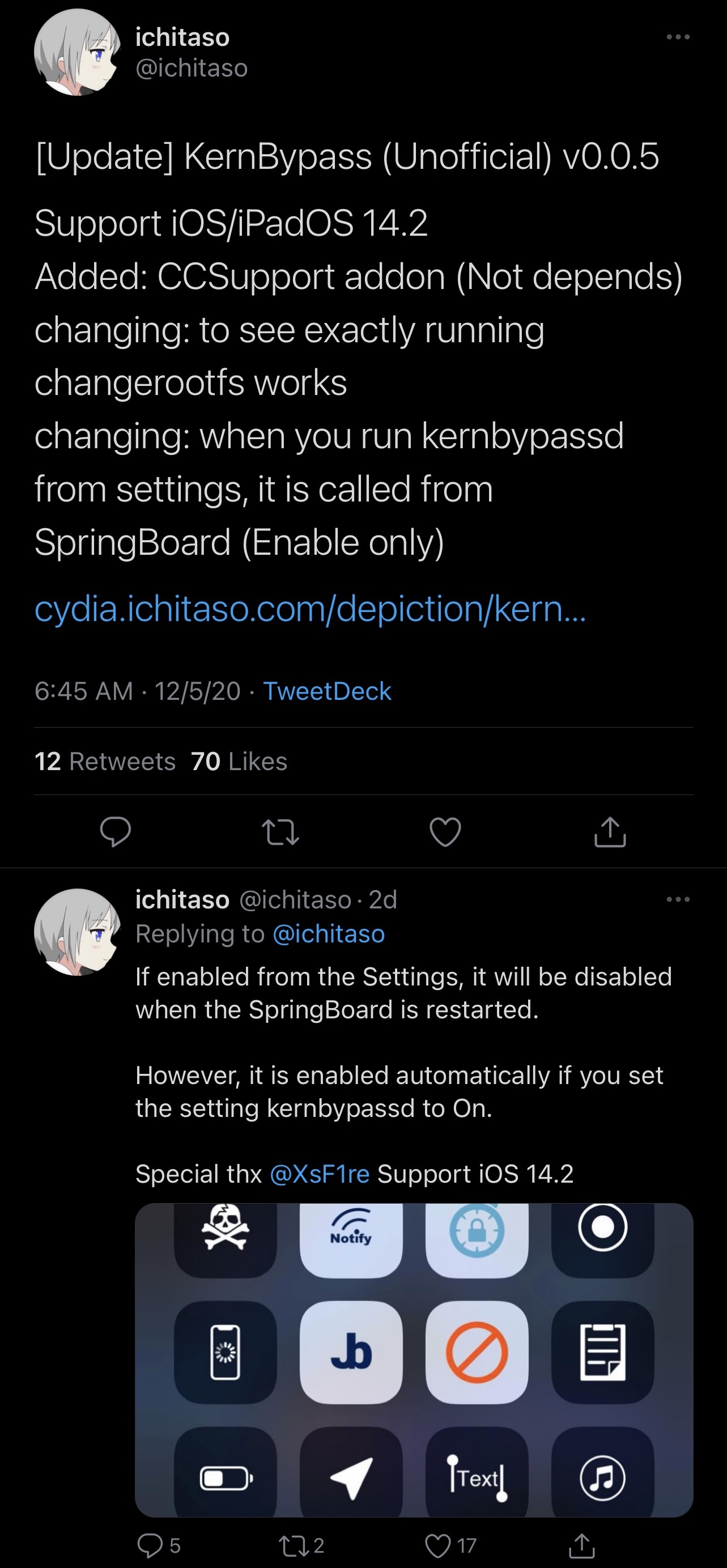
In an announcement Tweet shared just this past Saturday, Ichitaso said that KernBypass v0.0.5 would incorporate the following improvements:
- Official support for iOS and iPadOS 14.2 on compatible handsets
- Support for CCSupport, enabling quick toggle functionality from Control Center
- Support for automatic start
- And other minor changes
Perhaps the most important takeaways are that this package supports the latest jailbreakable firmware (on checkra1n or Odysseyra1n devices only at this time) and that it can be toggled manually via Control Center or automatically with the kernbypassed function.
Those already using XsF1re’s FlyJB X kernel-level jailbreak bypass without any issues, then you may need need to change to Ichitaso’s KernBypass. Whether or not you do will come down to just how badly you want the newly announced features above. Both developers have good track records, and it wouldn’t be surprising if XsF1re’s FlyJB X soon offered the same features as those offered by KernBypass. Only time will tell, however.
If you’re wondering what a kernel-level jailbreak bypass is or why you might need it, then it ultimately comes down to this: some apps look to see if you’re jailbroken before you use them, and if the check comes back positive, then the app may lock you out, or worse, ban you. Kernel-level jailbreak bypasses like this one work at the kernel level, and should therefore be untraceable, allowing you to use apps that would normally bar jailbreakers from using them.
Sounds warm and cozy right? Well, just remember that you use these things at your own risk. No one but you will be liable if you install a kernel-level jailbreak bypass and end up getting banned from your favorite app due to a fluke. If you accept these terms, then go ahead and give it a try.
Those interested in learning more about Ichitaso’s KernBypass v0.0.5 project can view the package depiction on Ichitaso’s repository via their favorite package manager. More details are available at the developer’s GitHub page.
Do you plan to install the new kernel-level jailbreak detection bypass by Ichitaso? Let us know down in the comments section below.