
When you’re an avid jailbreaker and you hear news about a new exploit that could potentially be used to jailbreak the latest version of iOS, then you tend to get excited about it. This response is only natural, especially given Apple’s rather conspicuous practice of rapidly releasing software updates to patch the very exploits hackers release in order to jailbreak iPhones and iPads alike.
With that in mind, jailbreakers might be particularly thrilled to learn that a new tfp0 exploit has been cooked up for Apple’s brand-new iOS & iPadOS 13.6 release, which was dropped to the public only yesterday afternoon. The news was first shared via Twitter user and security researcher @_Simo36 Thursday morning:
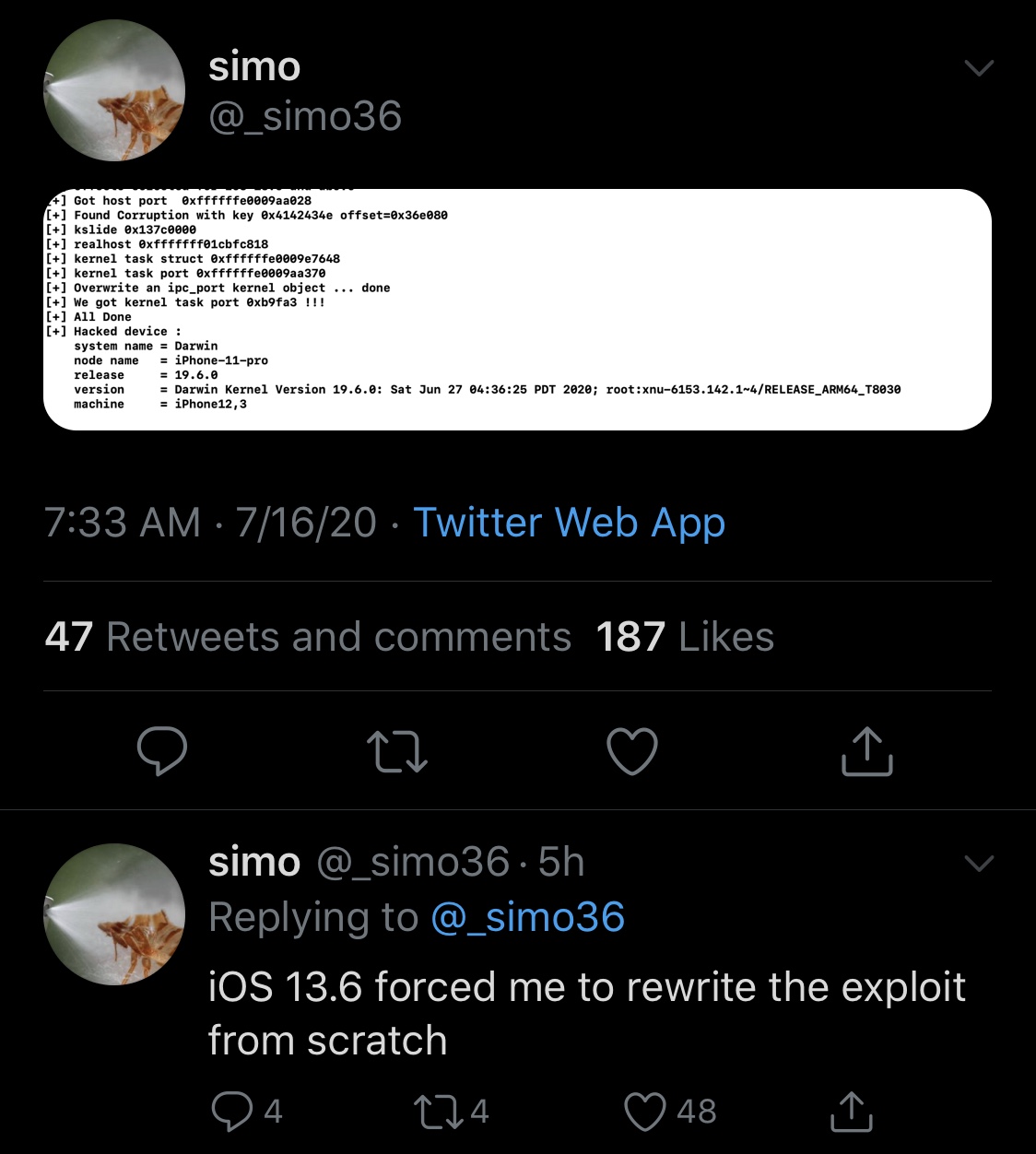
As for what a tfp0 exploit is, it’s essentially a kernel task port that permits arbitrary reads and writes to a handset’s kernel memory. Exploits of the tfp0 variety are software-based and are used by popular jailbreak tools like unc0ver, Chimera, Electra, and even the upcoming Odyssey tool. Unlike hardware-based bootrom exploits such as the one utilized by the checkra1n jailbreak, tfp0 exploits can be patched by Apple with software updates.
Given just how vital tfp0 exploits are to the creation of jailbreak tools, it’s particularly exciting to learn that even Apple’s latest iOS & iPadOS 13.6 update is vulnerable.
There haven’t been any announcements regarding whether the new tfp0 exploit would be released to the general public, but if it does get released, then it would be likely that even Apple’s latest firmware on the company’s latest handsets would be pwnable.
For what it’s worth, the checkra1n jailbreak can already jailbreak iOS 13.6 on compatible handsets.
What are your thoughts on the fact that a tfp0 exploit is already available for iOS & iPadOS 13.6 not even a full day after release? Let us know in the comments section below.