
Jailbreakers with access to an A7-A11 device pretty much have it made thanks to the hardware exploit-based checkra1n jailbreak that can’t be patched by Apple in a software update. Those handling newer devices, such as the A12 and A13 varieties, instead depend on infrequently released tfp0 exploits. These seem to surface sporadically with no rhyme or reason, and they can unfortunately be patched by Apple’s software updates.
On a more positive note, it does appear that a skilled security researcher going by the Twitter handle @ProteasWang has achieved tfp0 on an A13-equipped handset running iOS 13.4.1. This is currently the latest version of iOS available from Apple, and with that in mind, the news has particularly exciting implications for jailbreaks such as unc0ver and the to-be-released Chimera13 tool.
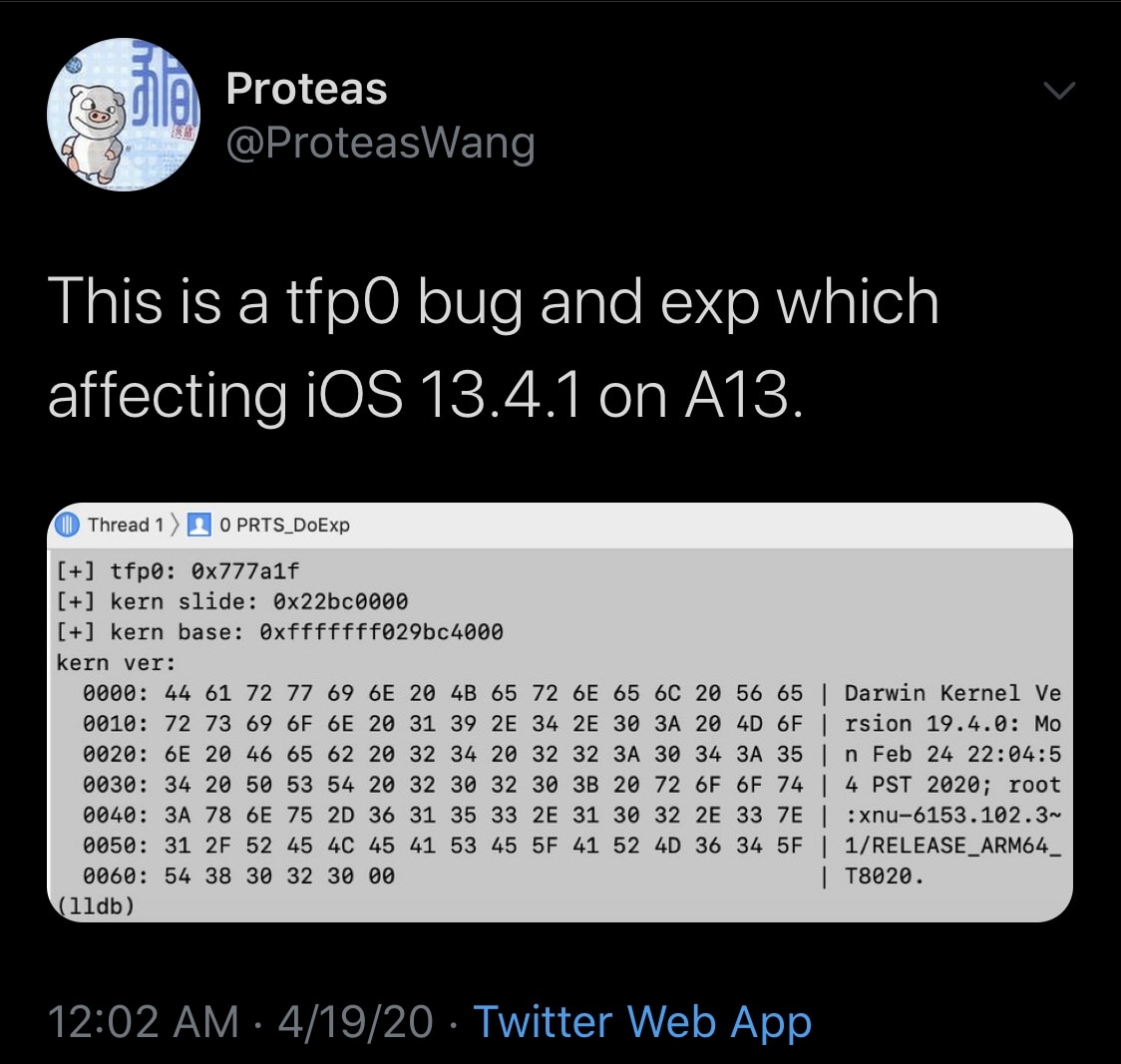
What does all this mean? Tfp0 is just a fancy way of saying that Wang managed a kernel task port, which this permits arbitrary reads and writes to the device’s kernel memory. Such a feat is essential to the entire jailbreak process, and this is precisely what lets jailbreakers overwrite Apple’s first-party software with third-party extensions.
In most cases, a tfp0 exploit that works on one particular device can be fine-tuned to work with older handsets, and this means that this A13-centric exploit should be backwards compatible with A12 and older handsets.
It isn’t yet clear if Wang will release this tfp0 exploit to the public, as there has been no official word at the time of this writing. If the exploit does get released, then jailbreak developers such as Pwn20wnd and CoolStar would then be capable of starting preliminary implementations into their jailbreak tools. Then again, that’s a big “if.”
It should be interesting to see if the exploit gets released. After all, there is currently no way of jailbreaking iOS 13.4.1 on any device besides those supported by checkra1n. Moreover, Apple appears to have additional updates on the back burner, and it remains to be seen if those updates will patch this newly announced tfp0 exploit. Only time will tell… we suppose.
Are you excited to learn that there’s a new tfp0 exploit in development? Share your thoughts in the comments section below.