We can almost always count on the jailbreak community to have something interesting going on during the week, and today is no different. Pwn20wnd released an updated version of the iOS 11.0-12.2-centric unc0ver jailbreak tool on Monday, officially bringing it up to version 3.3.8.
Pwn20wnd announced the update just this morning via Twitter, noting that it would implement an updated iteration of Jake James’ Sock Port exploit:
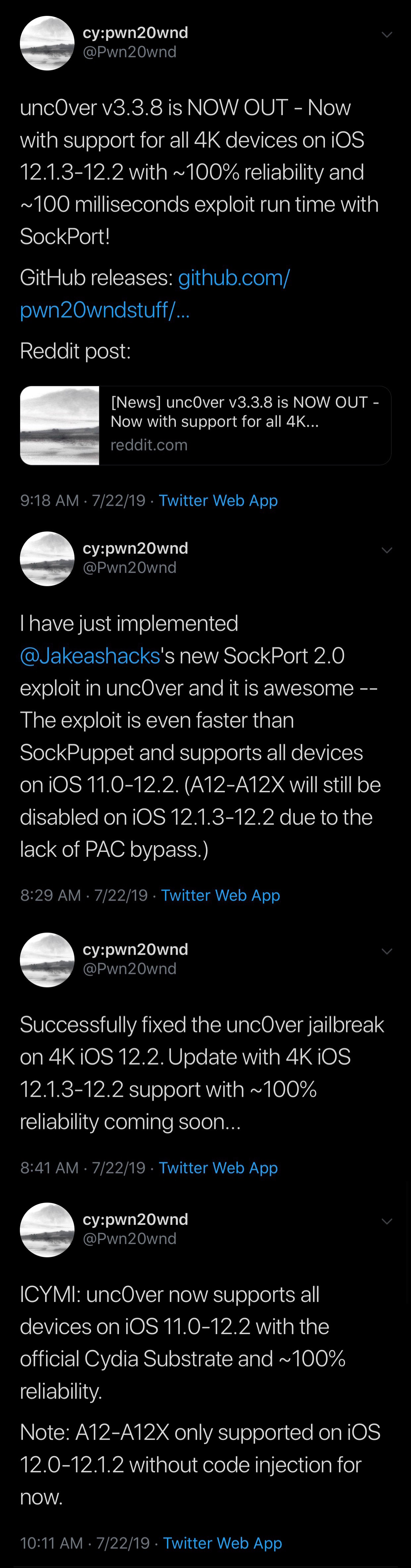
Citing Pwn20wnd’s GitHub page, the full change log for unc0ver v3.3.8 is as follows:
07/22/2019 – v3.3.8 was released for production with the following changes:
– Use the rewritten SockPort 2.0 exploit with ~100% reliability, ~100 milliseconds run time and support for all devices on iOS 11.0-12.2 (12.1.3-12.2 on A12-A12X excluded)
– Fix the jailbreak on iOS 12.2 iPhones and iPods
In case you were unaware, Jake James’ Sock Port exploit originally only supported A7-A9(X) devices running iOS 11.0-12.1.4, but the updated iteration now supports up to iOS 12.2, which offers a better scope of jailbreakability than before.
Pwn20wnd says that the updated Sock Port exploit brings near-100% jailbreak reliability, and that it offers near-100 millisecond run time, providing one of the fastest jailbreak experiences ever for iOS 12. Perhaps unsurprisingly, the exploit will not jailbreak A12(X) devices running iOS 12.1.3-12.2 due to the lac of a PAC bypass for those device and firmware combinations.
According to James himself, while the latest iteration of Sock Puppet supports more devices on more firmware versions, it’s also more reliable, with the only trade off being that it’s slightly slower than before.
If you’re currently using an older version of unc0ver, then it’d be in your best interest to download and deploy v3.3.8 such that you can take advantage of the latest exploit refinements, device support, and stability improvements.
As always, you can download the latest version of the unc0ver jailbreak from Pwn20wnd’s official GitHub page. You can also follow the steps listed in our in-depth tutorial if you’ve never jailbroken with unc0ver before.
Are you taking advantage of the updated Sock Port exploit in unc0ver v3.3.8? Let us know in the comments section below.