A new type of man-in-the-middle attack has been detected in the wild, targeting Apple’s Mac. Dubbed OSX/DOK, it relies on a new strain of macOS malware which leverages a bogus security certificate to bypass Apple’s Gatekeeper protection. Popular anti-virus programs are currently unable to detect OSX/DOK.
The Hacker News and researches at CheckPoint explain that the malware affects all versions of macOS by using a valid developer certificate signed by Apple. Here’s what OSX/DOK does, how it works, how to tell if you’re affected and what you can do to protect yourself and avoid these kinds of attacks in the future.
What is OSX/DOK?
OSX/DOK is a new type of malware distributed via an email phishing campaign.
It’s been designed to specifically target Mac owners. OSX/DOK affects all macOS versions and can avoid detection by most anti-virus programs. It’s signed with a valid developer certificate authenticated by Apple, meaning it avoids detection by macOS’s Gatekeeper security feature.
How does OSX/DOK infest your Mac?
The malware bundle is contained in a .ZIP archive named “Dokument.zip.”
Once executed, the malware first copies itself to your Mac’s /Users/Shared/ folder before executing itself from that location. It then proceeds to install a new root certificate which lets it intercept your traffic with a man-in-the-middle attack. To ensure the malware finishes installing its payload before a reboot, it adds itself as macOS Login Item named “AppStore”.
Next, the user is greeted with a persistent window designed to look like a valid macOS warning, as you’re seeing on the screenshot below. The window informs the user of a supposed security issue in their Mac which requires an update. The message prevents the user from doing anything on their computer until they accept the fake update prompt.
Clicking the Update All button puts up another prompt asking for your password.
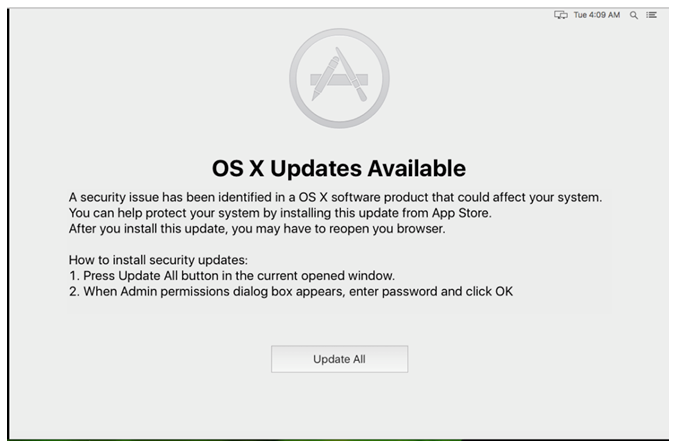
Once the password is supplied, the malware gains administrator privileges on your Mac.
Using those privileges, it installs command-line tools that allow connection to the dark web. It then changes your Network Settings to redirect all outgoing connections through a malicious proxy server which lets the attacker eavesdrop on your communications.
Some phishing messages used to spread the malware appear to mostly target users in Germany, but that doesn’t mean that only European users are at risk. For what it’s worth, the malware code supports messages in both German and English.
What damage does OSX/DOK do?
OSX/Dok redirects your traffic via a malicious proxy server, giving nefarious users access to all your communication, including that encrypted by SSL. Because it installs a compromised root certificate on the system, the attacker is able to impersonate any website to fool users into providing their passwords for banking apps and popular online services.
How to know if you’re affected?
If you’ve recently opened a ZIP file in an email message you weren’t expecting, and are now seeing suspicious-looking prompts asking for your Mac password, your system may have been infected with OS X/DOK. Because the malware redirects your network traffic to a rogue proxy server, you should venture into System Preferences → Network.
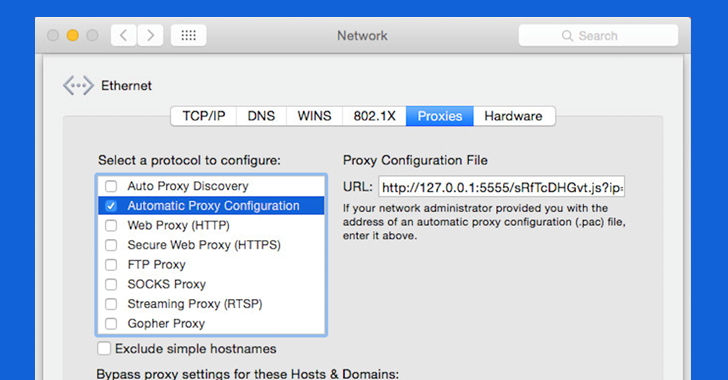
From there, select your active network connection in the lefthand column (like Wi-Fi, Ethernet and so forth), then click the Advanced button. Now click the Proxies tab.
If Automatic Proxy Configuration has been enabled in the lefthand column and the field underneath the heading Proxy Configuration File points to the URL that begins with “127.0.0.1:5555”, the malware is already routing all your traffic through a rogue proxy server.
Simply delete this entry to prevent traffic routing.
The malware installs two LaunchAgents that will start with system boot:
- /Users/YOUR USERNAME/Library/LaunchAgents/com.apple.Safari.proxy.plist
- /Users/YOUR USERNAME/Library/LaunchAgents/com.apple.Safari.pac.plist
If you find these files in the above locations, delete them immediately.
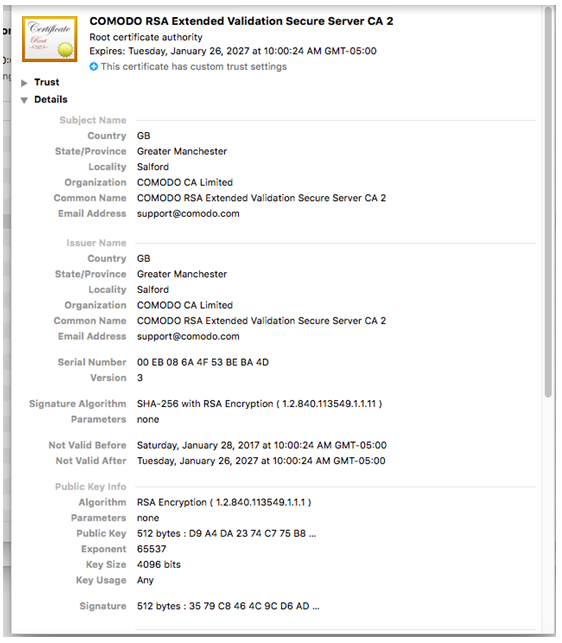
Lastly, check for the existence of the bogus securest certificate named “COMODO RSA Extended Validation Secure Server CA 2” in the System section of the Keychain Access app in your /Applications/Utilities/ folder.
If the certificate is installed on your Mac, delete it.
How to protect yourself?
OSX/DOK is the first major-scale malware to target Mac users via a coordinated email phishing campaign.
The first point of attack relies on the user opening a maliciously-crafted attachment in an email message. Don’t open suspicious attachments, especially if the attached file is named “Dokument.ZIP”. Beware of phishing messages bearing animated GIFs or those regarding supposed inconsistencies in your tax returns.
Always check the headers to confirm the validity of the sender.
If the malware file has found its way on your system, do not interact with and suspicious-looking prompts pretending to be valid macOS dialogs, especially if they ask for your root password for no apparent reason. Apple never puts up warning messages if your Mac requires a software update. All macOS software updates are distributed exclusively via Mac App Store.
If you use an anti-virus app, update its signature database manually.
At the time of this writing, no anti-virus vendor has updated their signature database with DOK OS X malware, but that will change soon. This malware issue will be fully resolved as soon as Apple revokes the bogus security certificate that its author has abused to bypass the Gatekeeper security feature.
Source: The Hacker News, CheckPoint