There’s a new trojan in town, one that attacks jailbroken iPhone, iPod touch and iPad devices.
As discovered by Lacoon, the malicious software dubbed Xsser mRAT uses social engineering to steal valuable data from jailbroken devices by fooling unsuspecting users to tap on an install link in phishing messages from unknown senders.
Created by Chinese hackers, it can extract a vast range of personal information including your iOS address book, SMS messages, call logs, GSM identities, your approximate geographical location (as determined by the cell tower ID), on-device pictures, as well as passwords and other authentication data in the iOS keychains used by your Apple ID, mail accounts and other services.
The spyware also sucks out additional data into the cloud, such as your iOS version, MAC address, phone number and device version, IMSI and IMEI. Once installed on a user’s device, the trojan runs immediately after a reboot and updates itself dynamically.
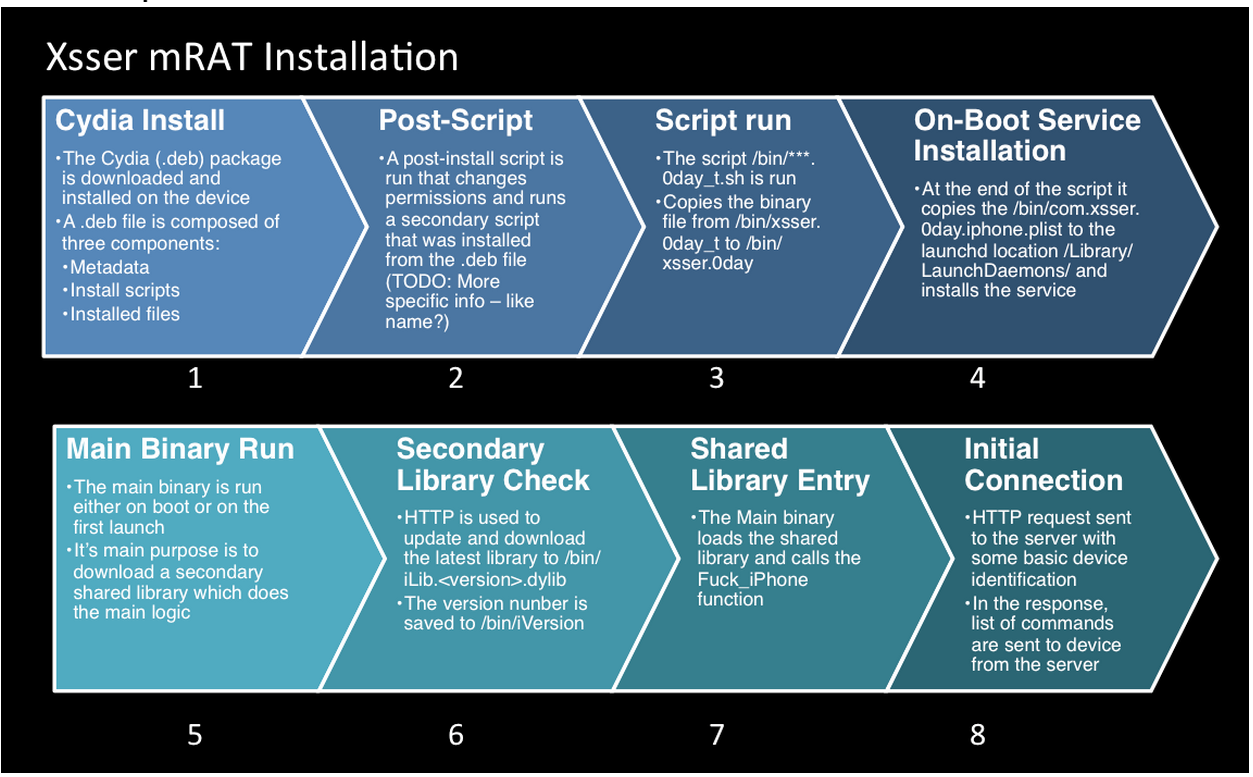
Noting that the exact attack vector is largely unknown, Lacoon has been able to determine that the malicious software leverages the popular Cydia store in conjunction with a special server that contains a Cydia repository for the mRAT debian package for both iOS and Android devices.
“With Cydia installed, the repository would be need to be added and then the package could be installed,” notes the article. The package then installs an iOS ‘launchd’ service to make sure the trojan starts immediately after rebooting your device.
The attackers have gone to great lengths to maintain their anonymity by using a Whois protection service on malicious servers. The servers themselves seem to be connected to a VPS service and can be accessed by RDP connections.
What can you do to protect yourself from Xsser mRAT.
Obviously, if you’re not jailbroken you’re in the clear. If you’re jailbroken, however, you should be careful about accepting links from unknown senders via WhatsApp, iMessage and other instant messaging platforms.
The Xserr mRAT trojan was successfully used Thursday against the Occupy Central protesters in Hong Kong, who received a WhatsApp link inviting them to install the trojan, which disguised itself as an app to help coordinate protesters.
And because Xsser mRAT is a cross-platform trojan targeting both iOS and Android devices, Lacoon believes it’s the first iOS trojan linked to the Chinese government cyber activity.
[Lacoon]