The alleged iCloud hacking, which has resulted in a massive leak of hundreds of revealing celebrity photos, has most likely been made possible because attackers reportedly used a piece of software that law enforcement officials rely on to siphon data from iOS device backups, Wired reported last night.
Rather than obtain a user’s iCloud username and password with brute-force attacks, the article points to web forum reports describing using specialized software called Elcomsoft Phone Password Breaker (EPPB) to impersonate the user’s device in order to obtain the full device backup which holds data like photos, videos, application data, contacts, text messages and more.
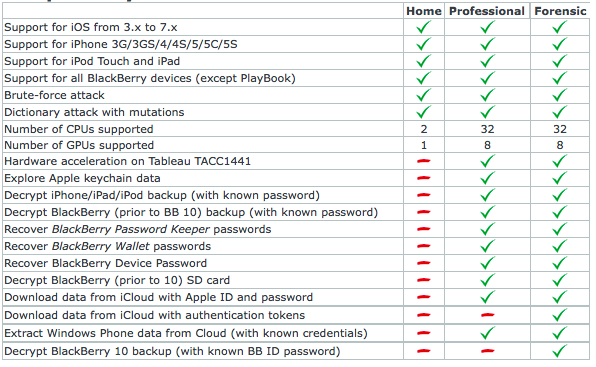
EPPB by Moscow-based Elcomsoft is typically used by law enforcement to gain access to a suspect’s iOS devices. Based on an analysis of the metadata from leaked photos of Kate Upton performed by forensics consult and security researcher Jonathan Zdziarski, the celebrity leaks might not have been possible without a tool like EPPB.
“You don’t get the same level of access by logging into someone’s [web] account as you can by emulating a phone that’s doing a restore from an iCloud backup,” says Zdziarski. “If we didn’t have this law enforcement tool, we might not have the leaks we had.”
Makers of the $399 tool reverse-engineered Apple’s protocol for communicating between iCloud and iOS devices, but no credentials are required to purchase this sophisticate software, which is freely available on bittorrent sites.
Worse, hackers on the web forum Anon-IB, one of the most popular anonymous image boards for posting stolen nude selfies, are even offering to pull nude photos on behalf of anyone who knows the target’s Apple ID and password.
Here’s a quick overview of EPPB.
In an effort to play down the PR crisis on its hand, Apple yesterday issued a media advisory attributing the leak to a “very targeted attack” and insisting that iCloud security has not been compromised.
This “very targeted attack” on user names, passwords and security questions has “become all too common” on the Internet, Apple said, adding that none of the cases they’ve investigated “has resulted from any breach in any of Apple’s systems including iCloud or Find my iPhone”.
Here’s Conan O’Brien’s take on the matter in an NSFW video below.
Long story short, Find My iPhone wouldn’t lock out a user’s Apple ID account after several unsuccessful attempts to guess the password, which provided a nice attack vector for nefarious users. Soon after the discovery was made public, Apple has patched this hole so now Find My iPhone locks you after five unsuccessful attempts to guess the password.
The seriousness of the celebrity breach is illustrated by the fact that the FBI is involved in the investigation as Apple continues to “work with law enforcement to help identify the criminals involved”.
The attack seems to have been targeted at female celebrities, most notably Jennifer Lawrence. For the sake of completeness, such an attack would have been rendered difficult, if not downright impossible, had the victims used a strong password and enabled two-factor authentication on their Apple ID.
If you have developed an interest in online security, I wholeheartedly recommend checking out Anna North’s excellent opinion piece over at The New York Times, titled ‘Why We Care About Privacy’.
Coincidentally or not, Apple yesterday updated its App Store guidelines for iOS development to ensure that third-party apps are not permitted to share user data acquired via HealthKit without user consent, use it for advertising or other data-mining purposes.
[Wired]