Last Thursday, an intruder attempted to secure personal information from Apple’s developer website. The company immediately took the dev center offline, and at the time of this writing it’s still down, in order to rebuild its systems in a way that this won’t happen again.
But just exactly how did it happen? Well according to Turkish security researcher Ibrahim Balic, who is claiming responsibility for the outage, he was able to infiltrate Apple’s servers thanks to an exploit he discovered in the recently released iAd Workbench software…
TechCrunch’s Chris Velazco spoke with Balic, who says that after discovering bugs for Facebook and other sites, he recently turned his attention to Apple. And he’s actually done quite well, sending 13 new bugs to the iPad-maker since he began his research on July 16.
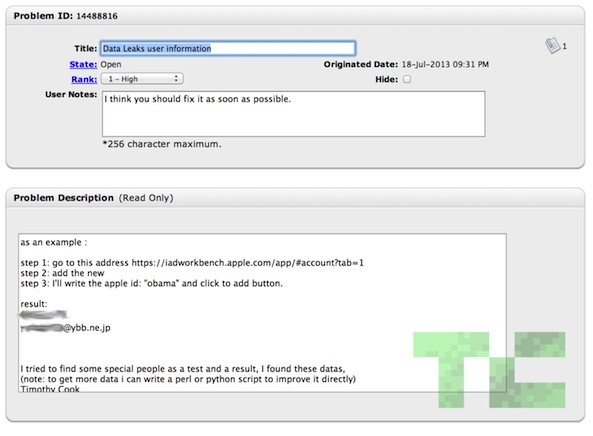
But there’s one exploit in particular that seems to be getting the lion’s share of attention, and that’s bug #14488816. Balic highlighted the find in his video (which has since gone private) and claims he reported it to Apple on July 18—hours before the dev center went down.
“That little security issue is centered around Apple’s iAd Workbench, a recently launched tool that lets users craft and target iAd campaigns to better build hype around their iOS apps. Balic discovered that if you manipulated a request sent to the server that runs Workbench, it would allow you to try to add a new user to the account. From there you could try throwing in first names, last names — whatever really — and the server would then respond with a full name and email address. Once Balic understood the full scope of the problem, he (and this is where his rationale loses me a bit) wrote a Python script to scrape all the data he could find and showed some of it on YouTube.”
As for the dev center itself, Balic submitted a bug report (#14461474) to Apple on July 16 that dealt with the dev center’s vulnerability to a stored XSS attack. He said that it was technically possible to access user data by exploiting this issue as well, but he never attempted it.
Ibrahim remains adamant that his intentions were not malicious, and it’s worth noting that Apple has confirmed that no credit card data, or any other sensitive information, was compromised. It’s still unclear, though, how much longer the developer center will be down.