Following an absolutely bonkers 4th of July weekend for Taurine users thanks to a new trick for keeping the Taurine jailbreak app signed indefinitely, it seems like things only appeared to get more interesting thanks to some additional research by Twitter user Nick Chan (@riscv64).
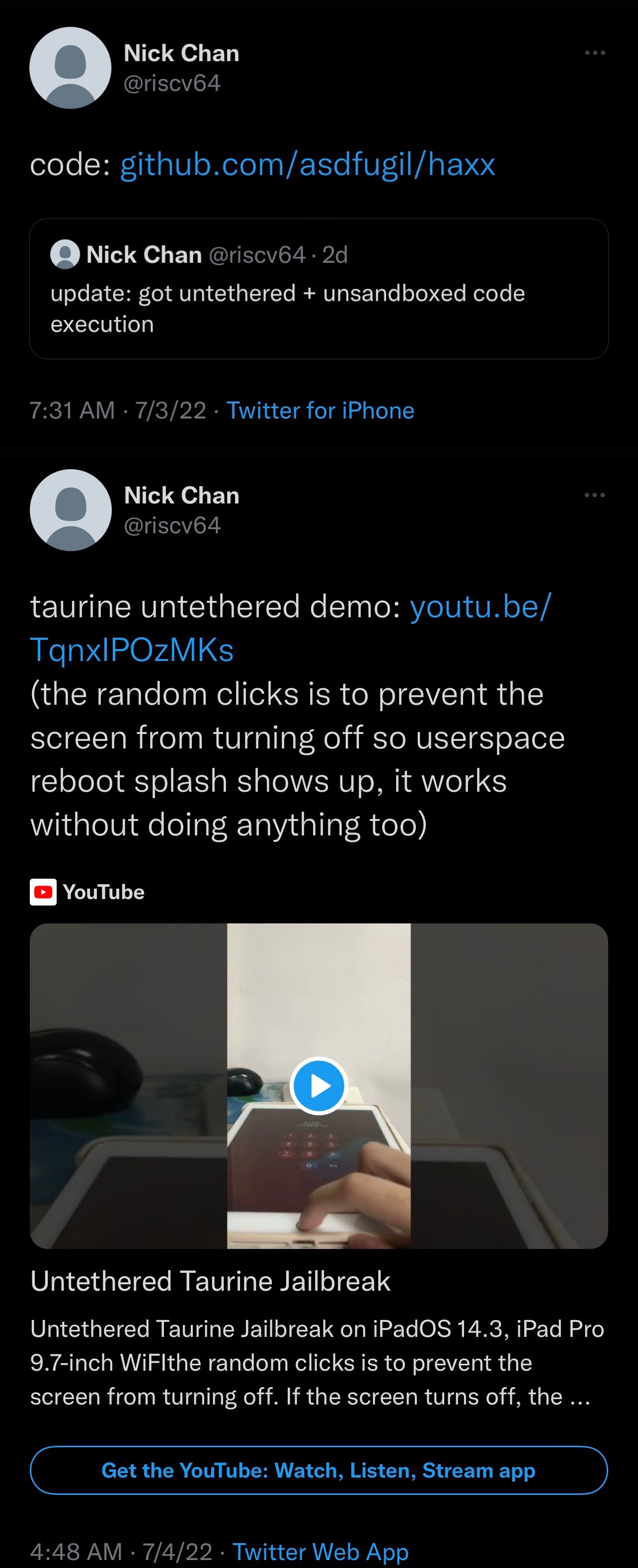
From what we can gather, Chan successfully achieved a full-blown untether for the iOS & iPadOS 14-based Taurine jailbreak with unsandboxed code execution as root. While the Taurine jailbreak only supports iOS & iPadOS versions 14.0-14.3 currently, it’s worth noting that Chan’s untether with unsandboxed code execution as root, dubbed haxx, supports all versions of iOS & iPadOS 14.0-14.8.1.
Citing the official GitHub write-up and PoC, the untether is based on the recently released CoreTrustDemo PoC by Zhuowei Zhang, which gave rise to the new taurine-permanent package that is being used by the Odyssey Team to allow users to keep their Taurine jailbreak app signed indefinitely.
The GitHub page also notes that installing the untether requires that the user have a Mac and that they have an existing iOS or iPadOS 14 jailbreak. This means that the hack could also potentially be used in tandem with other jailbreaks for iOS & iPadOS 14, including checkra1n and unc0ver, not just Taurine, which received most of the spotlight this past weekend. This is important considering the supported firmware versions listed by various jailbreaks.
In a Tweet chain Tweeted late last night, Chan shared a YouTube video demonstrating the untether working on an iPad running the Odyssey Team’s Taurine jailbreak. After a seemingly long reboot process, Chan simply opens the Sileo app and begin using it without having to re-jailbreak the device with the Taurine app – a telltale feature of a truly untethered jailbreak that we haven’t seen available for the general public since the iOS 9 days; true persistence:
Responding to the impressive feat was none other than iOS hacker and developer Jake James, who appears to not only explain why the reboot took as long as it did, but also offer some friendly advice about how Chan could potentially speed the process up a bit:
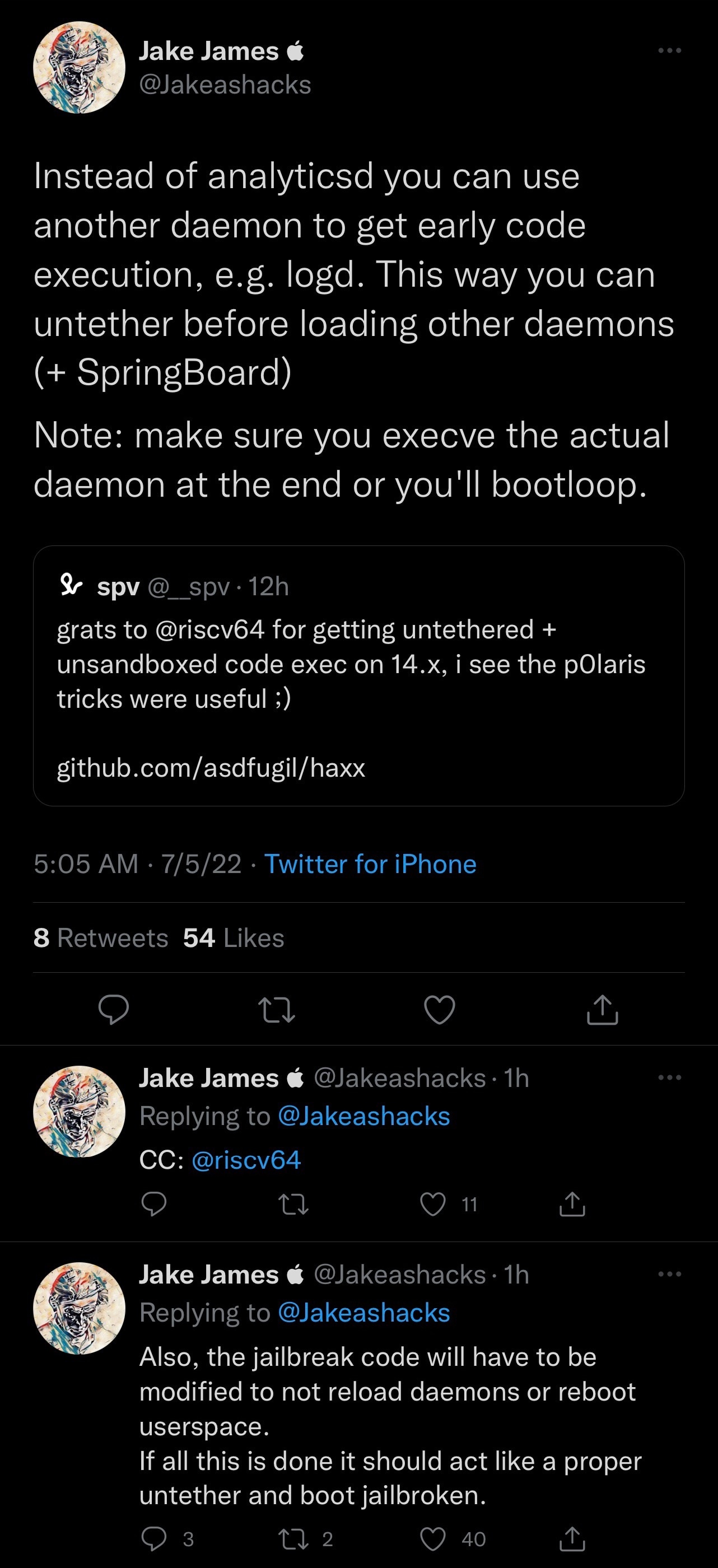
According to James, Chan could switch from one daemon to another to achieve earlier code execution. In doing so, one wouldn’t need to wait so long for all the device’s daemons to start up before the untether would take place. It remains to be seen if this will be adjusted in the future.
Because the untether and unsandboxed code execution is open source on Chan’s GitHub page, it will be interesting to see whether jailbreak developers choose to refine the code and implement it into existing iOS & iPadOS 14-based jailbreaks or not. After all, most jailbreakers salivate over the thought of a truly untethered jailbreak because of the joys that come with not being dependent on a computer to stay jailbroken.
Are you excited to see where this goes? Be sure to let us know in the comments section down below.