Apple hasn’t held back from being vocal about the performance and security of its proprietary M1 chip – the tried-and-true powerhouse found inside of several different Mac computer models and even the highest-end 2021 iPad Pro. But as it would seem, not even the venerable M1 chip is hack proof…
Hacker and ZecOps security researcher @08Tc3wBB, known for contributions to the jailbreak community in the form of exploits that have been used in tools such as unc0ver by Pwn20wnd, appears to have made a momentous breakthrough with respect to the M1 chip.
More specifically, a series of Tweets shared Tuesday afternoon allude to the idea of a kernel-level exploit for Apple’s M1 chip that affects M1-equipped Mac computers running macOS Big Sur versions 11.0 to 11.3.1:
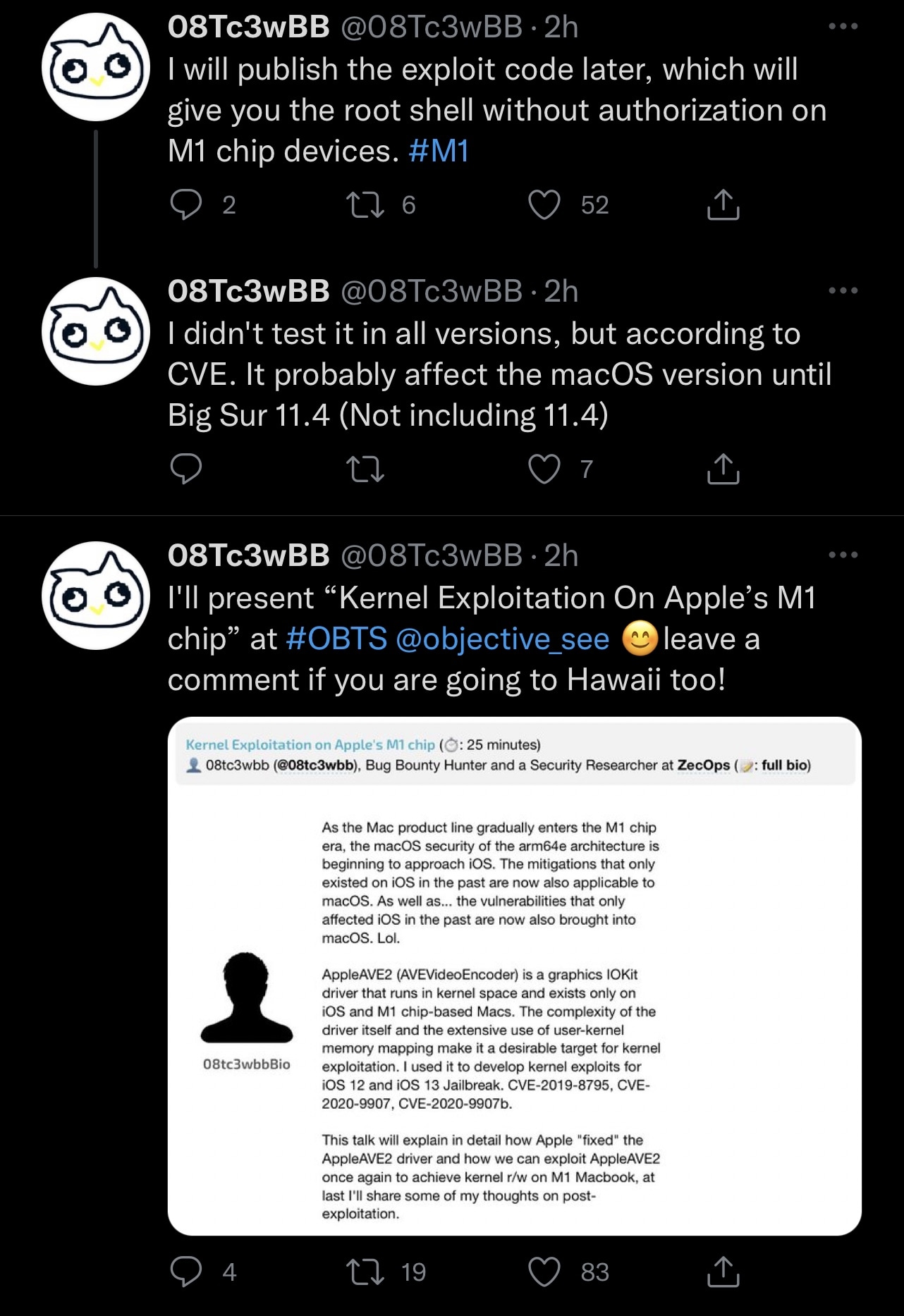
Citing the Tweets, it seems that @08Tc3wBB plans to present the aforementioned M1 exploit and relevant findings at a macOS-themed security conference called Objective by the Sea (OBTS) v4.0 in Hawaii this September.
The renowned bug bounty hunter and security researcher went on to explain that this exploit would grant the user with root shell access without authentication on impacted devices. While it’s suggested that the exploit would work on M1-equipped Macs running up to macOS 11.3.1, @08Tc3wBB admits that the exploit wasn’t tested on all versions of the operating system between 11.0-11.3.1, despite being confirmed to work on some.
Regardless, this is a huge breakthrough, as Apple appears to be making the hard shift toward proprietary processing power. This has long been the case with Apple’s mobile devices, but more recently, Apple-branded computers such as the iMac, MacBook Air, and MacBook Pro also come with the option to run an M1 chip rather than the more traditional Intel x86 processors.
The description for the upcoming presentation by @08Tc3wBB at Ojective by the Sea is as follows:
As the Mac product line gradually enters the M1 chip era, the macOS security of the arm64e architecture is beginning to approach iOS. The mitigations that only existed on iOS in the past are now also applicable to macOS. As well as… the vulnerabilities that only affected iOS in the past are now also brought into macOS. Lol.
AppleAVE2 (AVEVideoEncoder) is a graphics IOKit driver that runs in kernel space and exists only on iOS and M1 chip-based Macs. The complexity of the driver itself and the extensive use of user-kernel memory mapping make it a desirable target for kernel exploitation. I used it to develop kernel exploits for iOS 12 and iOS 13 Jailbreak. CVE-2019-8795, CVE-2020-9907, CVE-2020-9907b.
This talk will explain in detail how Apple “fixed” the AppleAVE2 driver and how we can exploit AppleAVE2 once again to achieve kernel r/w on M1 Macbook, at last I’ll share some of my thoughts on post-exploitation.
@08Tc3wBB noted plans to publish the exploit code online after completing the presentation above, which could offer an interesting look into how it works and what it might be useful for.
The elephant in the room is of course the question of whether this exploit could result in a jailbreak for M1-equipped Macs or not, and that’s a question that hasn’t been answered at the time of this writing. We’re sure the question will come up during the presentation, however.
Given the increasingly likely possibility that Apple will attempt to limit software downloads to that of the App Store and trusted developers, the imaginative idea of a jailbreak for Mac computers doesn’t seem too far out of reach. For what it’s worth, the Sileo Team already plans to release Procursus and Sileo for macOS in the future.
Furthermore, as Apple pushes the M1 architecture into the iPadOS (and perhaps soon iOS) ecosystems, the exploit could have relevance on mobile platforms as well.
It will indeed be interesting to witness @08Tc3wBB presenting at OBTS and to see what becomes of this marvelous work. Only time will tell, however…