Hot off the heels of Apple’s newly released iOS & iPadOS 14.7.1 software update Monday afternoon, the company published a page entitled “About the security content of iOS 14.7.1 and iPadOS 14.7.1.” The notes describing what this update patches are somewhat shocking.
More specifically, it references a zero-day kernel level exploit dubbed CVE-2021-30807, which Apple says, “may have been actively exploited.” The company credits an anonymous researcher for finding and reporting the security hole and goes on to mention that it had the potential to let an app run arbitrary code with kernel privileges.
Shortly after iOS & iPadOS 14.7.1 was made available to the masses, security researcher @b1n4r1b01 took to Twitter to share what looks to be a proof of concept (PoC) of CVE-2021-30807 at work:
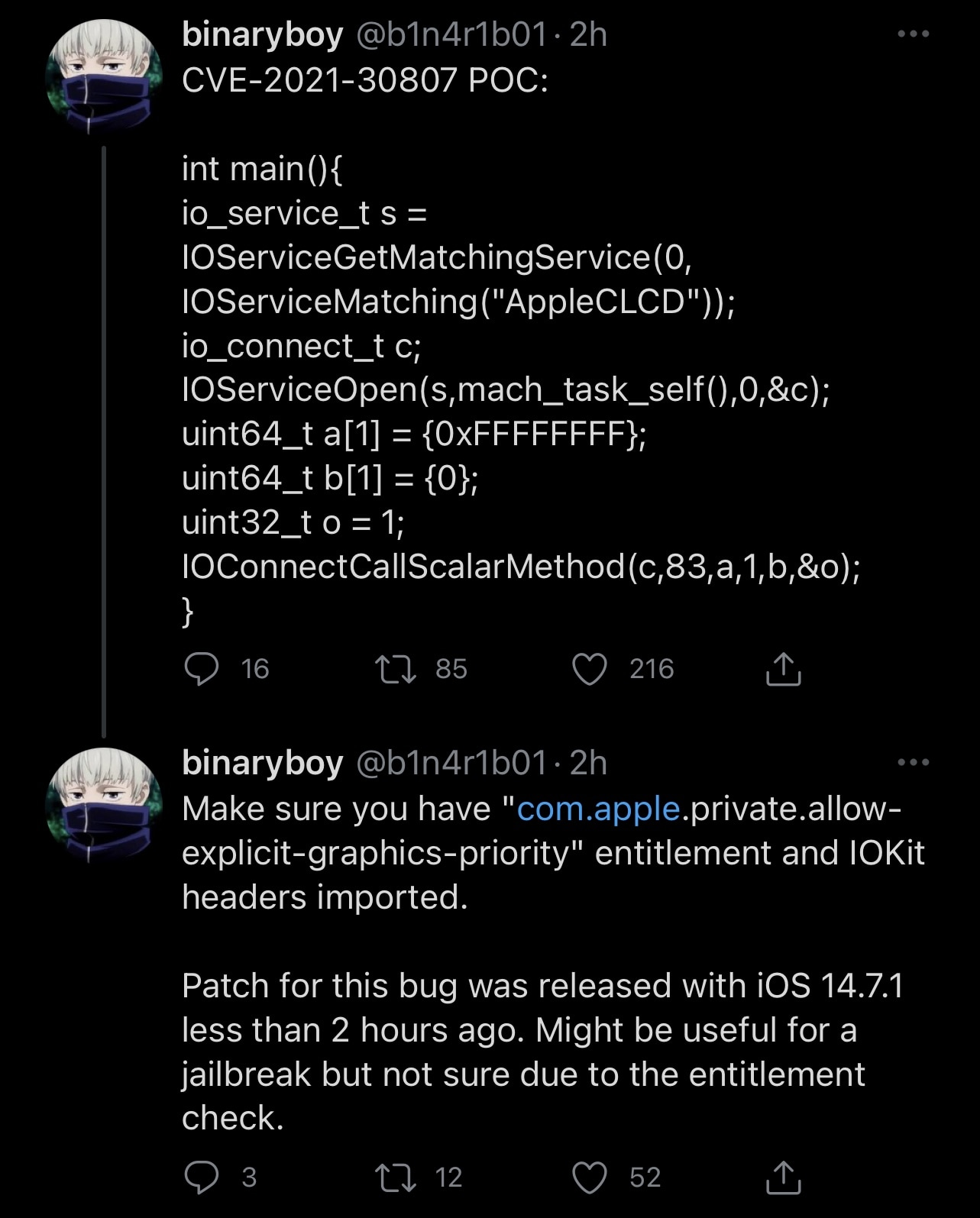
In a follow-up Tweet, @b1n4r1b01 mentioned a few more details pertaining to the PoC, such as to “make sure you have com.apple.private.allow-explicit-graphics-priority entitlement and IOKit headers imported.” Additionally, the Tweet said that the aforementioned PoC “might be useful for a jailbreak,” however with the asterisk that the entitlement check may hinder that.
Since this exploit was only just patched in iOS & iPadOS 14.7.1, that would mean that it actively impacts all devices running both iOS & iPadOS 14.7, which Apple only just released to the general public last week – a fairly recent firmware with modern new features, bug fixes, and security patches.
The elephant in the room is whether this exploit can or can’t be used for developing a jailbreak supporting up to and including iOS & iPadOS 14.7, or simply updating existing jailbreak tools such as Taurine or unc0ver. While we don’t have a clear-cut yes or no answer as of right now, we’re sure that more details will surface in the coming days or weeks as jailbreak team members begin research.
Given the lack of clairvoyance regarding whether this will materialize into anything useful, the jailbreak community shouldn’t get its hopes up. On the other hand, it’s still a good reason to save your .shsh2 blobs for iOS & iPadOS 14.7 since it is still being signed at the time of this writing.
Also see:
- How to save your .shsh2 blobs online with TSS Saver
- How to save your .shsh2 blobs on A12 and newer devices
Saving blobs while they’re being signed helps ensure that you can downgrade to unsigned firmware in the future – cementing your jailbreakability if something becomes of today’s news.
Are you excited to see what becomes of CVE-2021-30807? We certainly are. Be sure to let us know in the comments section down below.