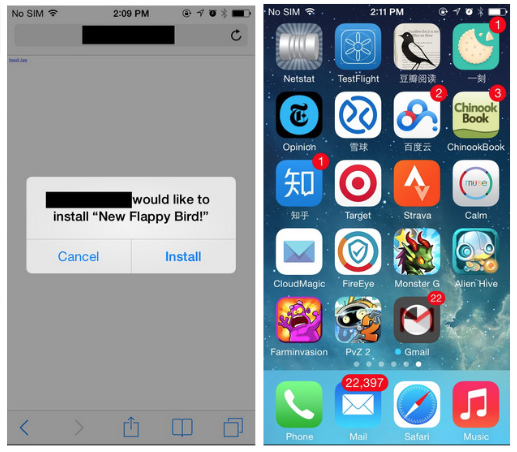
The United States government issued a warning for iPhone and iPad users today regarding the recently-discovered ‘Masque Attack’ vulnerability, reports Reuters. The security flaw, which began circulating the web earlier this week, allows malicious third-party apps to be installed to a device using enterprise provision profiles.
Today’s bulletin was issued by the National Cybersecurity and Communications Integration Center, and it warns users of how Masque Attack can spread and what it’s capable of doing. The malware installs itself through a phishing link disguised as a new app or game, and then it can masquerade as a well-known app like Gmail.
Once installed, the app can mimic nearly any iOS app enough to steal login credentials and credit card information. It can also access private data via local data caches, perform background monitoring of the host device, and worst of all, it can gain root access privileges to its host device, meaning there’s very little it can’t do.
The NCCIC says users can protect themselves by avoiding apps outside of the App Store. They should pay particular care to not tap ‘Install’ in popup boxes on third-party websites, and to not open any links sent via iMessage from an unknown contact. Also, users should always select “Don’t Trust” when iOS displays the “Untrusted App Developer” alert.
The team that discovered Masque Attack, FireEye, says it has notified Apple about the vulnerability, but it has yet to hear back from them and the company hasn’t made a public statement regarding the issue. The exploit affects a wide range of devices, including iOS 7.1.1, 7.1.2, 8.0 and 8.1, and it has not been patched in the latest 8.1.1 beta.
[Reuters]