In case you missed our Sunday coverage of the newly exposed NSA tactics, the snooping agency – thanks to its secret 10-year initiative code-named Bullrun which runs at $250 million a year – has been able to successfully crack much of the Internet’s widely-used encryption technologies to compromise everyone’s online communications, banking transactions and other sensitive data.
And now, internal NSA slides from a 2010 report titled ‘Exploring Current Trends, Targets and Techniques’ and leaked by the NSA whistleblower Edward Snowden shamefully depict iPhone customers as ‘zombies’. As if that weren’t enough, in a reference to the George Orwell book ‘1984’ Steve Jobs himself is being portrayed as Big Brother…
The German paper Der Spiegel published this set of slides Monday.
Although other smartphone platforms collect users’ anonymized location history for the purposes of improving location accuracy and traffic data, Apple’s presence, brand power and clout (and non-scandals like Locationgate) have led one particular NSA slide to refer to Apple owners as “zombies” brainwashed by Big Brother.
By the way, NSA documents also refer to Internet users as “adversaries”.
Another slide references Apple’s 1984 Macintosh commercial – widely regarded as one of the most memorable and successful American television commercials of all time. Apple’s ad, seen below, depicts the then omnipresent IBM as Big Brother with the underdog Apple and its Macintosh destined to save the world from the Orwellian future.
Playing that card, the two NSA slides use Steve Jobs graphics to liken the late Apple co-founder to Big Brother.
The NSA documents also reveal that the agency is able to access a wide variety of iPhone geolocation features and other data.
“The implication of the presentation is that iPhone users are somehow complicit in their own surveillance by buying iPhones in the first place,” Der Spiegel observed.
These slides are just shameful and in really bad taste, if you ask me.
Of all people, NSA dares painting Apple as Big Brother?
If anyone is Big Brother in this world, it’s organizations like NSA that have compromised online user’s privacy security over and over again, up to the point where anything and everything you do online is being eavesdropped, collected and analyzed by NSA’s humongous data centers.
The worst part: had it not been for brave individuals like Edward Snowden, we would have never known anything about the scope of NSA’s snooping and privacy intrusion.
As mentioned in the introductory paragraph, owners of iPhone, BlackBerry and Android devices are definitely at risk of their “most sensitive data” being fully exploitable because the NSA is able to crack protective measures of these systems, previously believed to be highly secure.
A follow-up story Sunday by the German news weekly Der Spiegel has revealed that the agency is able to leverage so-called backdoor access to infiltrate your computer remotely and decrypt the iPhone backup files created during each iTunes sync, injecting small scripts that enable additional access to at least 38 iPhone features.
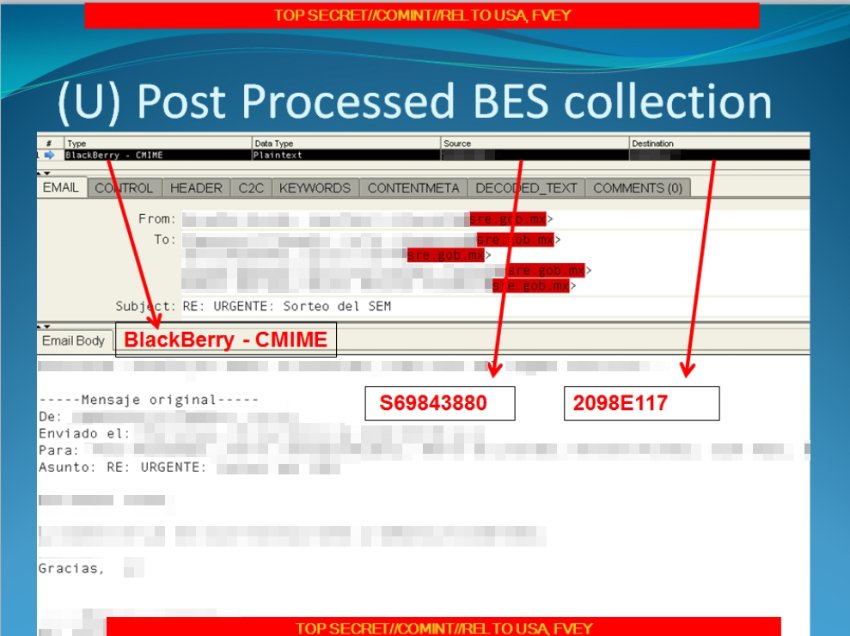
Finally, one particular slide from a presentation appropriately titled “Your target is using a BlackBerry? Now what?” shows an email from a Mexican government agency which was sent using BlackBerry encryption technology, intercepted by the NSA nonetheless.
NSA whistleblower Edward Snowden noted in a Q&A session over at The Guardian that “encryption works: properly implemented strong crypto systems are one of the few things that you can rely on,” but also cautioned that “Unfortunately, endpoint security is so terrifically weak that NSA can frequently find ways around it”.
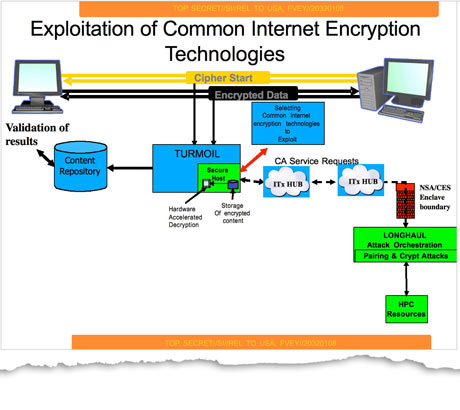
Indeed, as one cryptology expert tells the paper, “The NSA has huge capabilities – and if it wants in to your computer, it’s in,” The exact nature of NSA’s methods is closely guarded, as one particular NSA slide explicitly warns analysts, “do not ask about or speculate on sources or methods”.
“There will be no ‘need to know’,” another internal memo warns.
These methods include not only cracking widely used encryption technologies to make “vast amounts” of previously collected data newly “exploitable,” but also working covertly with standard bodies to influence international encryption standards and using powerful supercomputers to break encryption with brute force methods.
On a definitely related note (as noted by a commenter), spell ‘illuminati’ backwards and put ‘.com’ at the end and watch the NSA website pop up.
Wait, what?
Probably some joker’s redirect.
Top of post: NSA’s mega data center in Utah hosts supercomputers that crack online encryption, analyze Internet traffic and invade our privacy.