The U.S. National Security Agency (NSA) has pretty much compromised every online user’s security through a previously unknown ten-year program against encryption technologies that made “vast amounts” of collected data “exploitable.”
After these shocking revelations came to light Thursday, a new report Sunday in German news weekly Der Spiegel has given the privacy scare a whole new meaning.
See, owners of iPhone, BlackBerry and Android devices are at risk of their “most sensitive data” being fully exploitable because the NSA is able to crack protective measures of these systems, previously believed to be highly secure…
Pet top secret documents leaked by NSA whistleblower Edward Snowden, Der Spiegel writes that the agency is able to retrieve your on-device contact lists, SMS traffic, notes and location information history.
It doesn’t seem to be widespread hacking as the documents mention “individually tailored” cases of smartphone tapping, often “without the knowledge of smart phone companies.”
That’s hardly reassuring:
In the internal documents, experts boast about successful access to iPhone data in instances where the NSA is able to infiltrate the computer a person uses to sync their iPhone. Mini-programs, so-called “scripts,” then enable additional access to at least 38 iPhone features.
Put simply, the NSA spies leverage so-called backdoor access to infiltrate your computer remotely and decrypt the iPhone backup files created during each iTunes sync.
The NSA has set up working groups that deal with each operating system. and tasked them with gaining secret access to the data held on the popular smartphone operating systems.
The agency has even gained access to BlackBerry’s highly secure email system, marking a “huge setback for the company which has always claimed that its mail system is uncrackable”.
Apparently, there was a period in 2009 when the NSA was temporarily unable to access BlackBerry devices. After the Canadian company acquired another firm the same year, it changed the way in compresses its data.
But in March 2010, the department responsible at Britain’s GCHQ intelligence agency declared in a top secret document it had regained access to BlackBerry data and celebrated with the word, “champagne!”
A 2009 NSA document explicitly acknowledges that the agency can “see and read SMS traffic.”
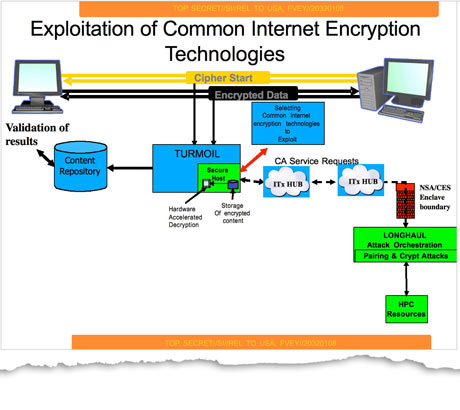
If you haven’t been following this major story, the British newspaper The Guardian along with its U.S. counterpart The New York Times and ProPublica, an independent non-profit newsroom that produces “investigative journalism in the public interest,” on Thursday exposed how NSA’s $250 million a year program against widely used encryption technologies made a breakthrough in 2010, making “vast amounts” of data collected through Internet cable taps newly “exploitable”.
Reporting stems from top secret files from both the NSA and The Government Communications Headquarters (GCHQ), a British version of the NSA, provided by NSA whistleblower Edward Snowden.
Not only did the NSA and GCHQ covertly influence international encryption standards, they also tap powerful supercomputers to break encryption with brute force methods.
The snooping agencies also collaborate with tech titans and the Internet’s four service providers that funnel encrypted traffic which the NSA can decipher and exploit, explicitly named as Hotmail, Google, Yahoo and Facebook.
NSA’s efforts have “broadly compromised the guarantees that internet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments,” The Guardian opined.
Check this out: the NSA has covertly changed commercial encryption software and devices “to make them exploitable” and is able to “obtain cryptographic details of commercial cryptographic information security systems through industry relationships”.
A 2010 GCHQ paper trail acknowledges that “vast amounts of encrypted internet data which have up till now been discarded are now exploitable”.
An internal agency memo says among British analysts shown a presentation on the NSA’s progress, “those not already briefed were gobsmacked!”
The all-encompassing program costs ten times more than the PRISM initiative and “actively engages US and foreign IT industries to covertly influence and/or overtly leverage their commercial products’ designs,” the classified documents read.
Another top secret NSA doc brags about gaining access to “data flowing through a hub for a major communications provider” and to a “major internet peer-to-peer voice and text communications system”.
The scariest bit: the NSA has compromised crucial and rarely-updated hardware such as network routers and switches, and even encryption chips and processors used in consumer devices. Yes, the agencies can get into your computer if need be, though such an accomplishment is “significantly more costly and risky for them”, another Guardian article states.
On the NSA, PRISM, and what it means for your 1Password data: http://t.co/azSbGkqgHp
— 1Password (@1Password) September 6, 2013
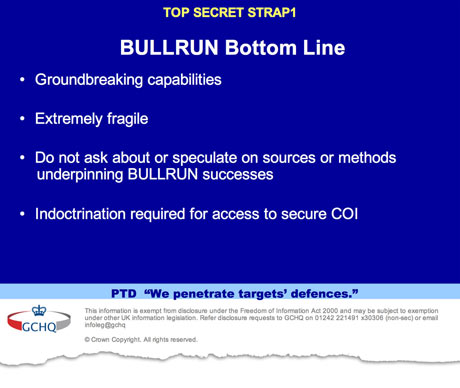
“The NSA has huge capabilities – and if it wants in to your computer, it’s in,” the crux of the story reads. The exact nature of NSA’s methods is of course closely guarded. As one slide warns agency analysts, “do not ask about or speculate on sources or methods”.
Those cleared to access the program were warned: “There will be no ‘need to know’.”
NSA’s secret mega data center in Utah: that’s where supercomputers analyze vast amounts of online traffic data obtained through snooping programs.
On Friday, Microsoft and Yahoo expressed concerns over NSA’s encryption bypassing methods. Microsoft said it had “significant concerns” about the reports and Yahoo said it feared “substantial potential for abuse”.
NSA documented its decryption initiative as the “price of admission for the US to maintain unrestricted access to and use of cyberspace”.
The iPhone 5S will provide NSA with the last piece of the puzzle: your fingerprint.
— Christian Zibreg (@dujkan) September 6, 2013
Responding to publication of these stories, the NSA in a Friday statement through the mouth of the office of the director of national intelligence (ODNI) laconically dismissed the findings. This is “not news”, the officials said and cautioned the revelations provided a “road map to our adversaries”.
The ODNI statement reads:
It should hardly be surprising that our intelligence agencies seek ways to counteract our adversaries’ use of encryption. Throughout history, nations have used encryption to protect their secrets, and today, terrorists, cybercriminals, human traffickers and others also use code to hide their activities.
Our intelligence community would not be doing its job if we did not try to counter that.
Needles to say, privacy advocates are baffled.
I suggest going through the entire coverage over at The Guardian – you’ll be gobsmacked.
It’s guaranteed to send chills down your spine and shatter any notion that strong encryption secures your online data and communications from the government’s prying eyes.
I’m terribly sorry, but it seems Big Brother is winning.