The Misaka package manager app has picked up yet another update on Friday, this time bringing it up to version 8.0.9 beta.
App developers can make special sideloadable apps that take advantage of the MacDirtyCow bug on iOS & iPadOS 15.0-15.7 and 16.0-16.1.2. Apps that exploit this bug can make cosmetic and functional changes to the operating system if it’s within the bounds of memory that a sandboxed app can access.
Follow along as we provide ongoing coverage on the latest MacDirtyCow developments.

The Misaka package manager app has picked up yet another update on Friday, this time bringing it up to version 8.0.9 beta.

The Misaka team is out with another update Thursday morning for the MacDirtyCow and kernel file descriptor (kfd) exploit-based package manager app, this time bringing the project up to version 8.0.8.

In addition to uploading a new tvOS-compatible version of the Misaka package manager app on Wednesday, it seems that project lead developer @straight_tamago is also releasing a new build for iPhones and iPads in the form of version 8.0.7 beta.

We’ve got some pretty big news for you if you’re a Misaka package manager app user or if you aspire to use it for Apple TV customization in any capacity.

The Misaka package manager app, which hosts a bevy of add-ons made to support both jailbroken and non-jailbroken iPhones and iPads vulnerable to the MacDirtyCow and kernel file descriptor (kfd) exploits, received an important update early Monday morning to version 8.0.0.

The Misaka package manager app received another update on Friday, this time bringing it up to version 3.3.7.

The Misaka package manager app for the MacDirtyCow and kfd exploits received a handful of updates within the past 24 hours with a ton of improvements for end users. The latest version at the time of this writing is now v3.3.6.
I still remember more than a decade ago when I first began jailbreaking iPhones that I would always install a particular theme on my device called Glasklart. I always appreciated the transparent icons on my Home Screen, along with the simplistic glyphs at the center of them.
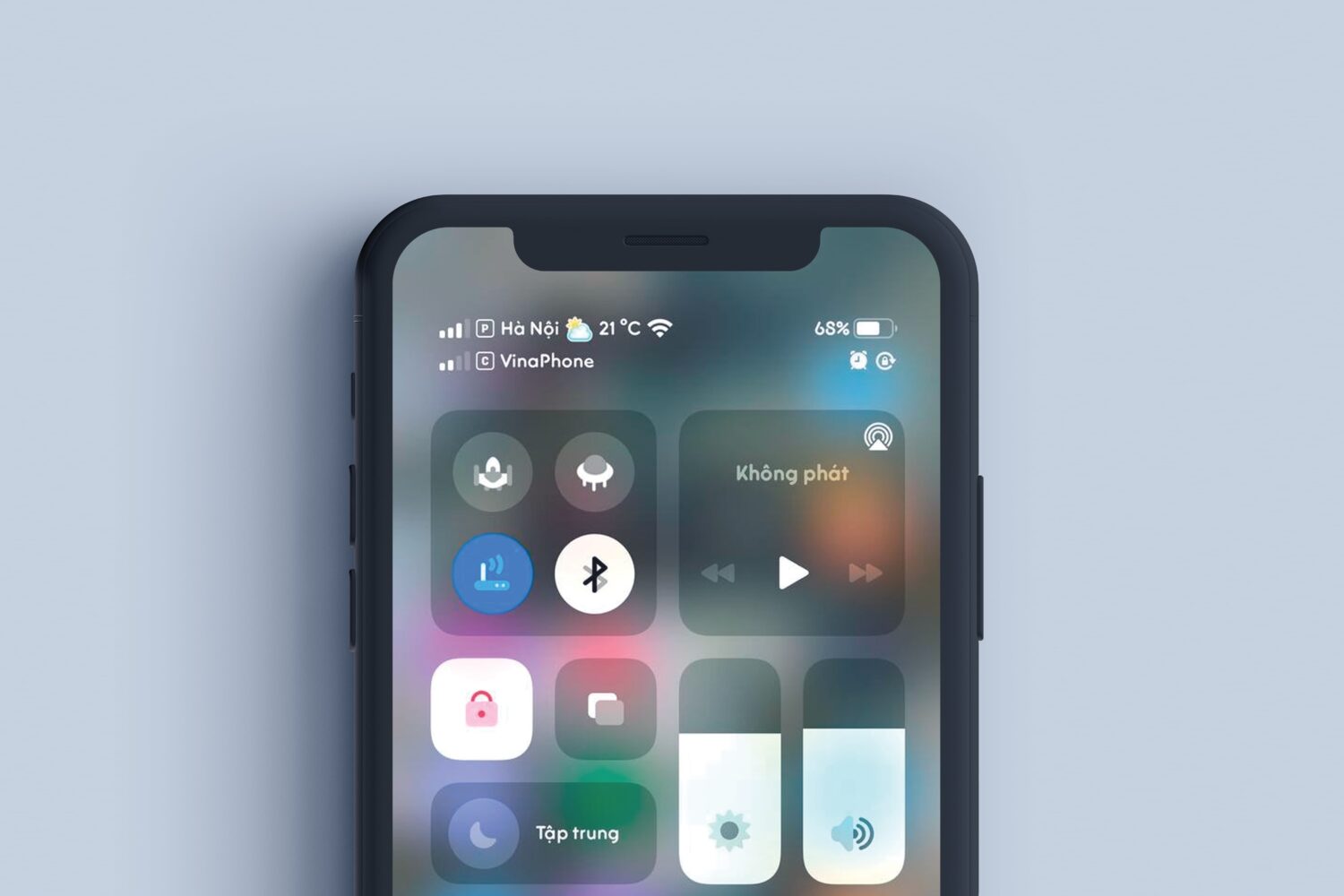
If you’re interested in harnessing the power of the MacDirtyCow exploit for iOS & iPadOS 15.0-16.1.2 or the kfd exploit for iOS & iPadOS 16.0-16.6 beta 1 to add a touch of extra information to your handset’s Status Bar, then we have a feeling that you’ll appreciate a new add-on called Real Weather by iOS developers YangJiii and Robin.

The Misaka package manager app picked up a minor incremental update to version 3.3.3 over the weekend, incorporating new features and bug fixes that will improve its overall user experience.

The Misaka package manager app, renowned for giving iPhone and iPad users the ability to install hacks and add-ons without a jailbreak by way of the MacDirtyCow (iOS & iPadOS 15.0-16.1.2) and kfd (iOS & iPadOS 16.0-16.6 beta 1) exploits, has received another important update.

The Misaka package manager app received another update on Wednesday, this time up to version 3.3.1 with new features and bug fixes that might be of interest to a substantial amount of prospective users.