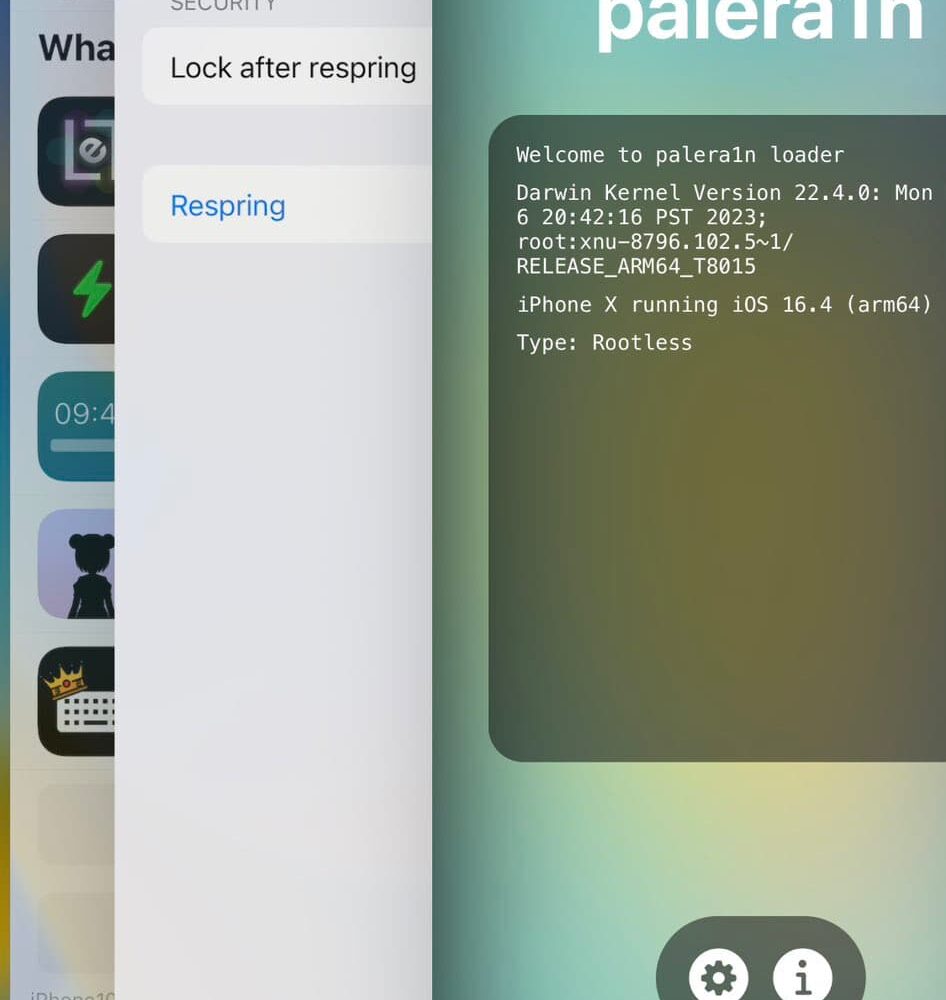
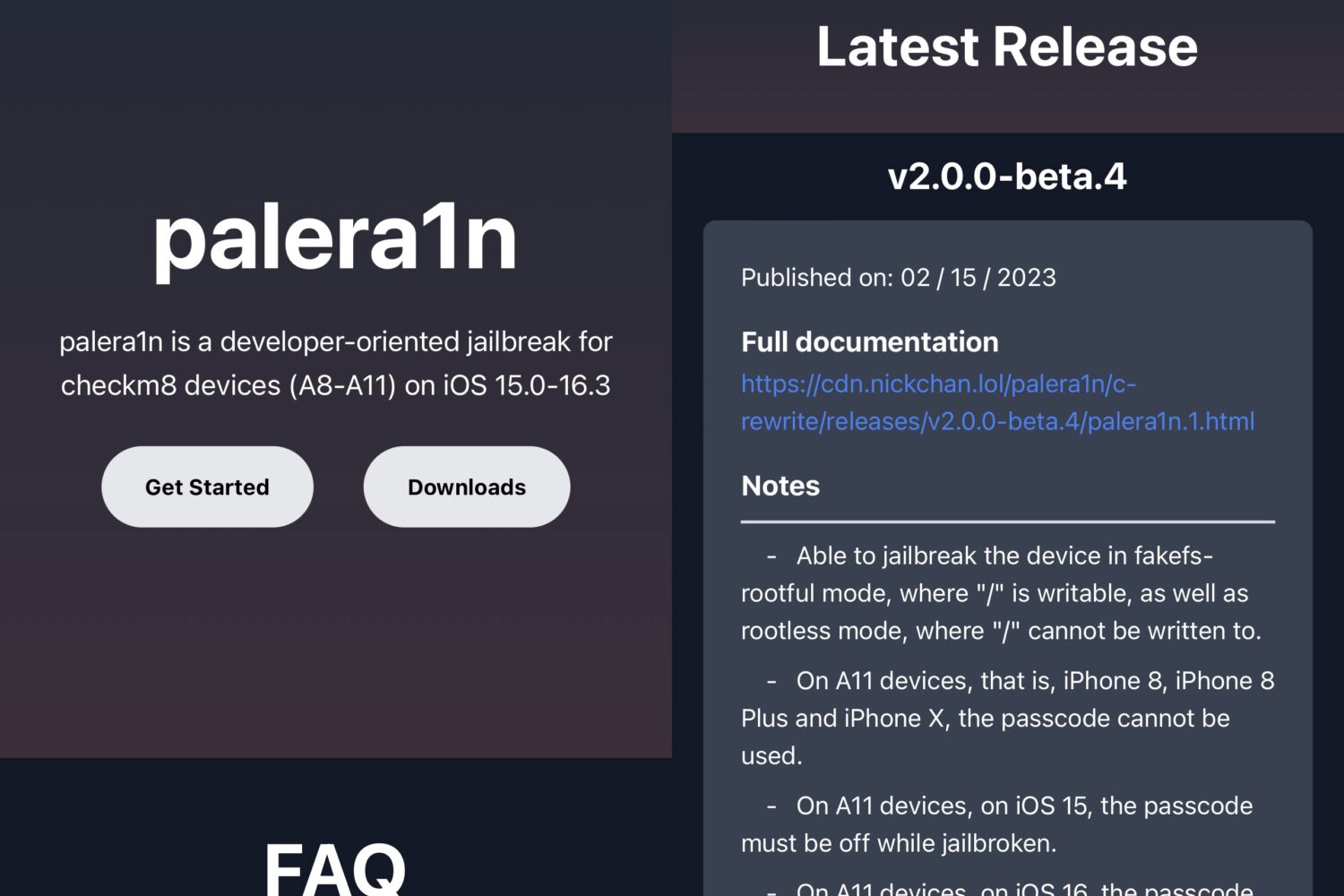
In April, there were conflicting reports concerning whether the upcoming iOS 17 software update would drop support for the aging iPhone X, 8, and 8 Plus or not. Following the WWDC 2023 keynote, Apple confirmed the company’s decision to ditch those devices in a press release.