Turn on the sync feature in the updated Google Authenticator app for iOS and Android to avoid a lockout crisis if you lose the device or buy a new one.
Google Authenticator finally syncs your security codes between devices
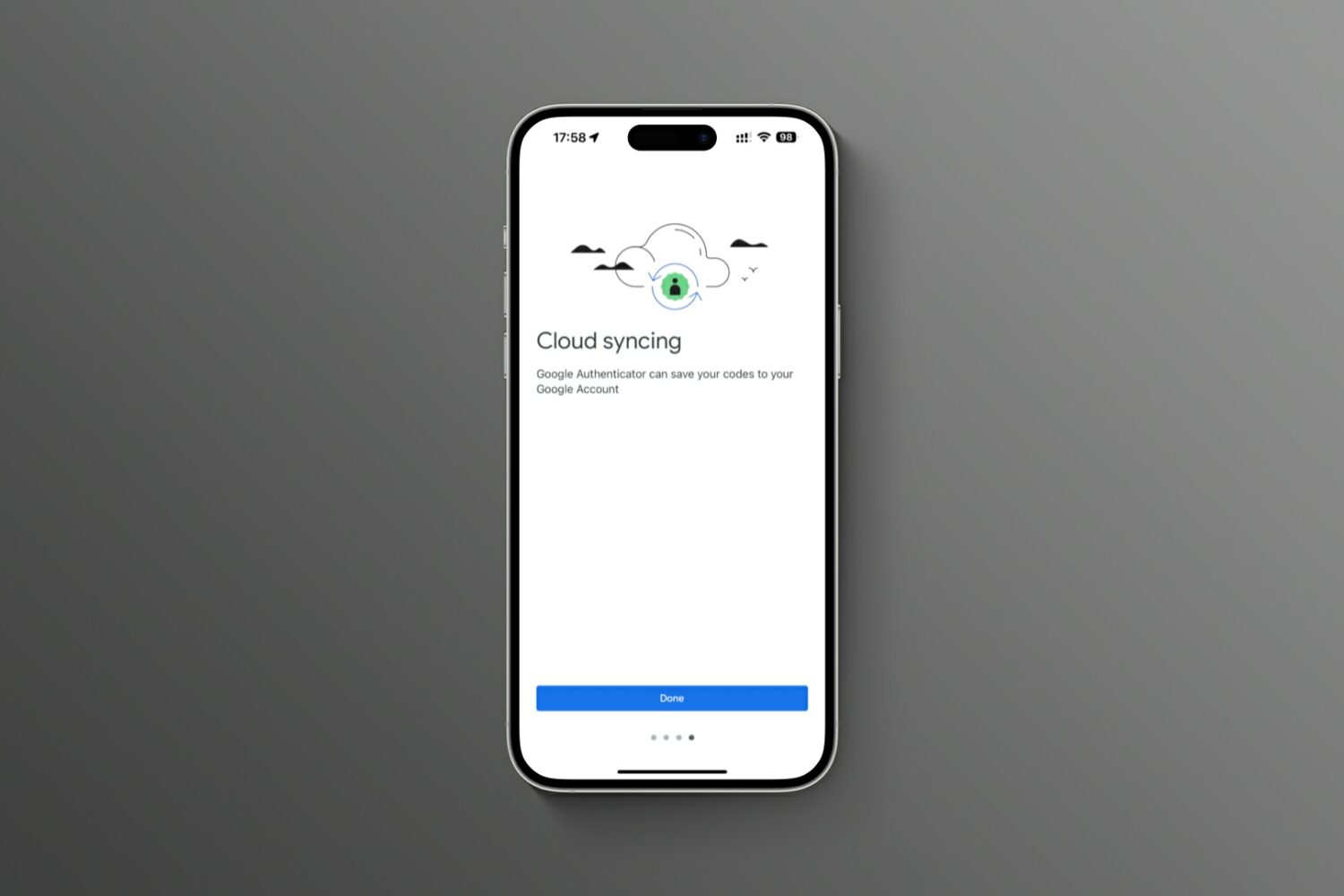

Turn on the sync feature in the updated Google Authenticator app for iOS and Android to avoid a lockout crisis if you lose the device or buy a new one.
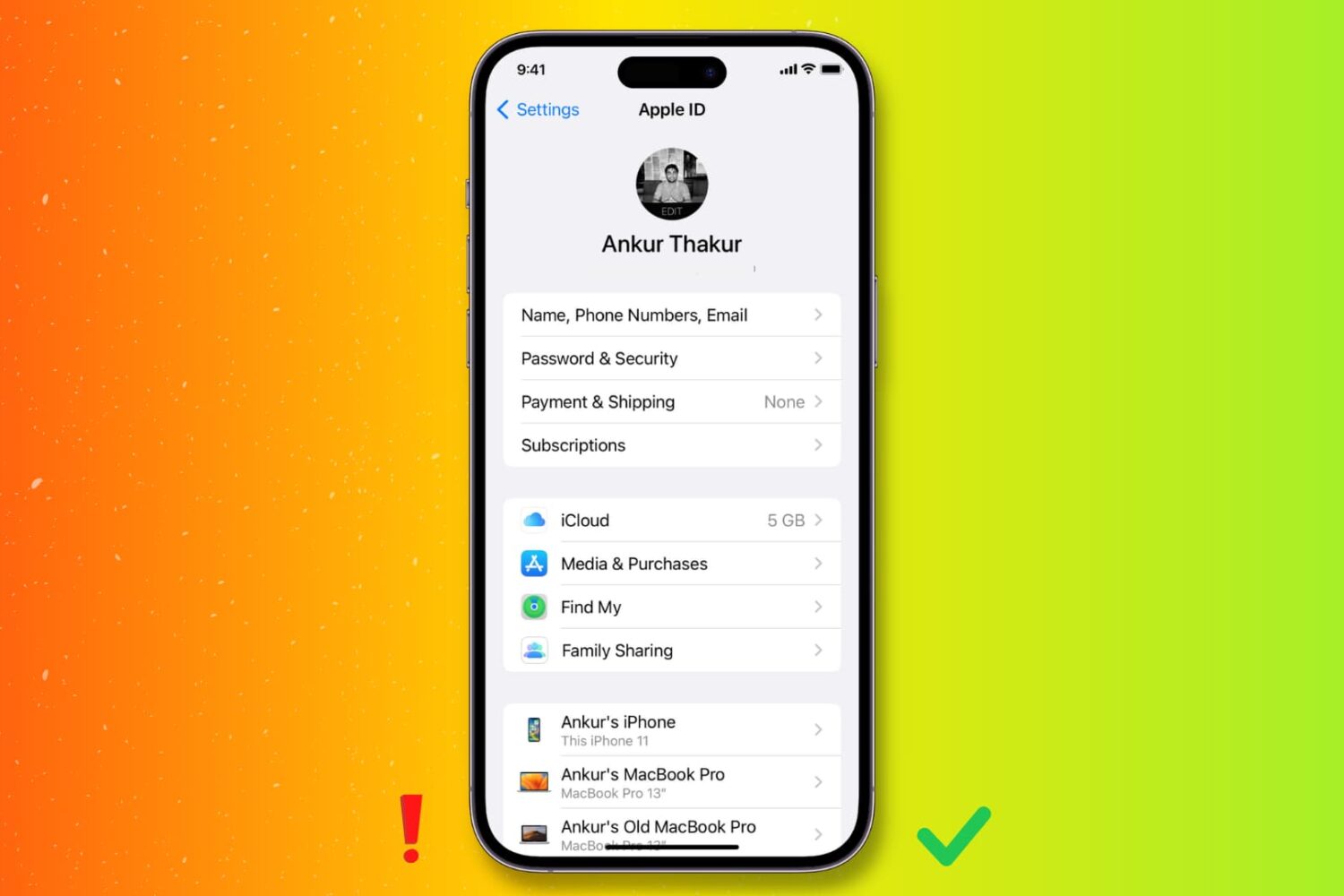
Your Apple ID or iCloud ID (same thing) contain valuable data such as your contacts, messages, photos, calendar events, files, third-party app data, payment methods, Apple ID balance, device backups, shipping & billing addresses, contact information, and more.
Therefore, it's critical to keep your Apple account secure, and in this guide, we will share 13 essential tips to achieve a high level of security.
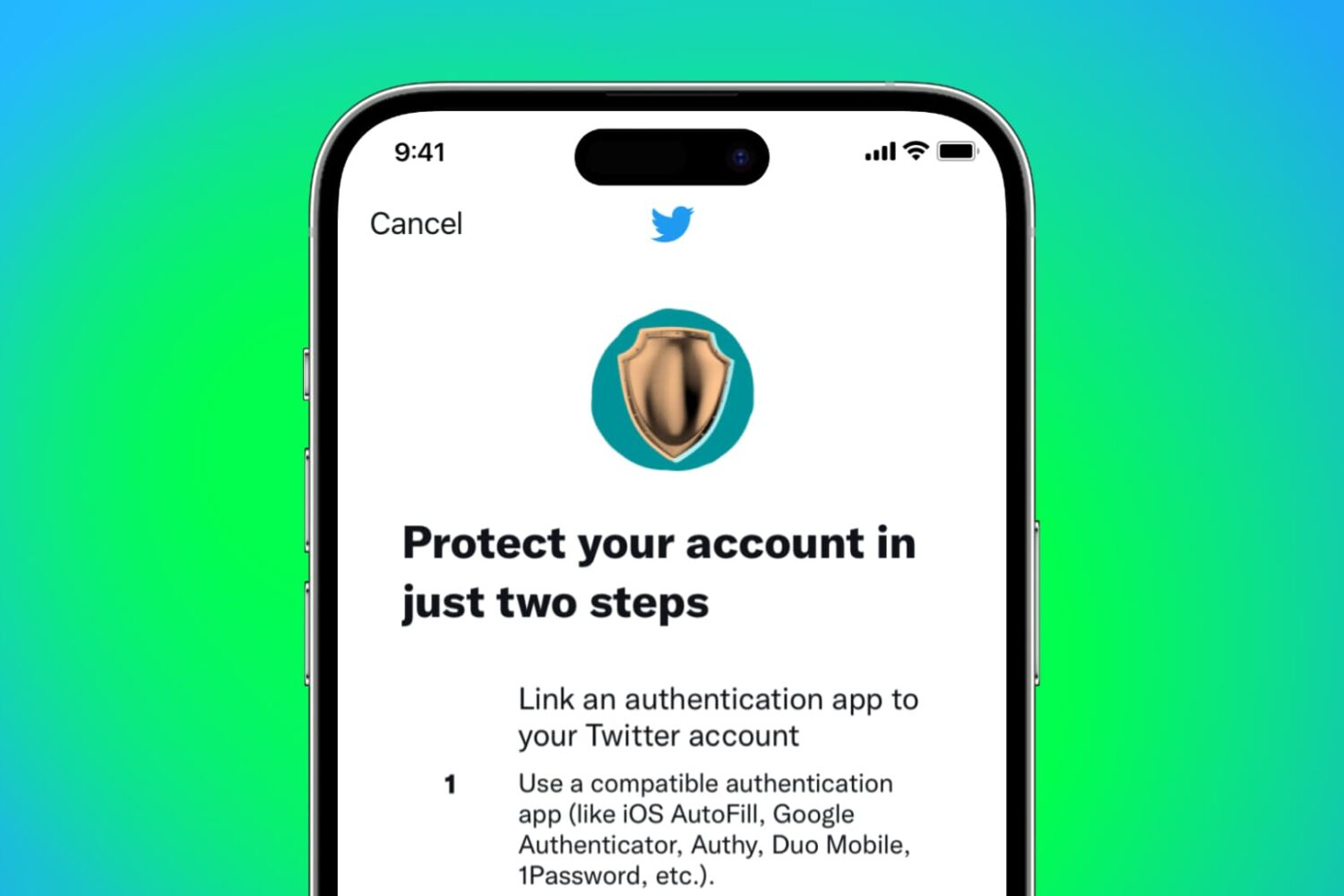
It is highly recommended you enable two-factor authentication (2FA) to secure your Twitter account and prevent anyone from getting access to it. This extra level of protection will ensure any intruder can't log in to your Twitter account even if they happen to know your password!
2FA requires you to enter your correct password (which is something you know) and then verify using a secondary means of proving your identity with something you have, like a changing code from the authenticator app.
Follow along as we show you how to set up Twitter two-factor authentication without using your phone number.
Adobe left the personal information of almost 7.5 million customers of its Creative Cloud service exposed, according to a new report on The Next Web.
Security firm Comparitech says Adobe left an Elastisearch server accessible without any password or authentication required. Adobe corrected the problem as soon as it was alerted on October 19th. Exposed information included email addresses, Creative Cloud subscription information and other details, though financial information and passwords were not exposed.
Comparitech's concern is that the information which was exposed may make those Adobe customers more liable to phishing attacks in the future.
Adobe acknowledged the issue in a blog post:
The environment contained Creative Cloud customer information, including e-mail addresses, but did not include any passwords or financial information. This issue was not connected to, nor did it affect, the operation of any Adobe core products or services.
Do incidents like this make you wary to share your details with companies like Adobe? Sound off in the comments.
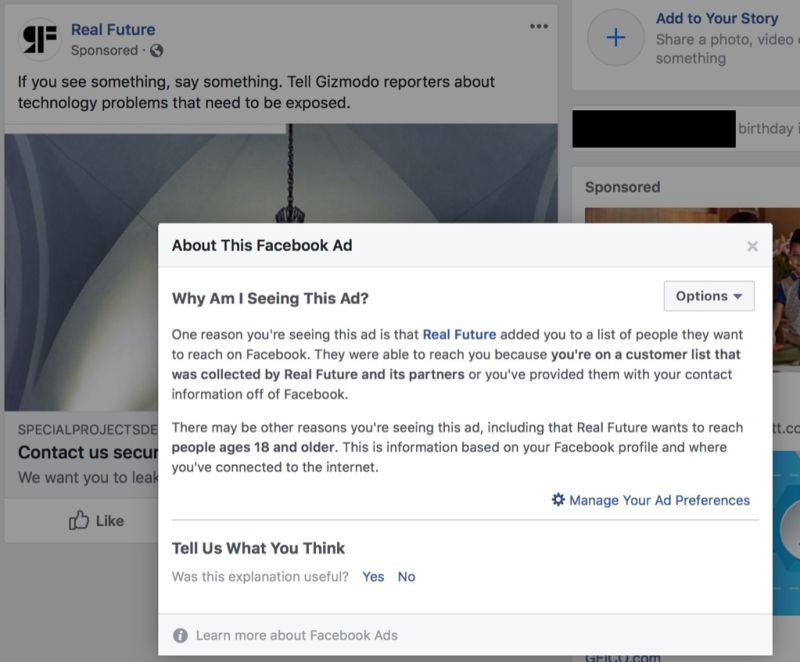
Following a Gizmodo report this week alleging Facebook is giving advertisers access to your shadow contact information, the firm's confirmed that it's been using the phone number registered with their two-factor authentication (2FA) system in order to target you with ads.

In today's day and age, there are chances that your various passwords can be compromised. This can happen even if you have taken just about every precaution possible.
One of the most prevalent and popular precautions has been the introduction of two-factor authentication (2FA). For the unaware, 2FA requires a second input from the user whenever signing into your account.
Thankfully, Apple has joined the movement in recent years in an effort to keep Apple ID's protected. However, there are sometimes where you forget your password, don't have your device handy, and are locked out.
We are going to take a look at what you can do in the event that you are locked out and can’t sign in or reset your Apple ID password.
Two-Factor Authentication strengthens the security of your Apple ID by preventing anyone from accessing or using it, even if they know your password. With Two-Factor Authentication, one of your trusted devices generates a one-time code when you make a purchase or sign in to your Apple ID, iCloud, iCloud.com, iMessage, FaceTime or Game Center account on a new device. Two-Factor Authentication is also required for Auto Unlock so you can unlock your Mac by wearing an Apple Watch.
In this tutorial we'll show you how to protect your Apple ID with Two-Factor Authentication or, if you're still using the older and less secure Two-Step Verification, upgrade to Two-Factor Authentication.

A trusted device is an iPhone, iPad, or Mac, where you have previously signed in using your Apple ID. Trusted devices are used to verify your identity when signing in and keep your Apple ID secure with two-factor authentication.
In this tutorial, we will go over trusted devices for Apple ID two-factor authentication, their requirements, and some other pieces of valuable information that you should know.