By now you’ve probably heard about the MacDirtyCow bug for iOS & iPadOS 16.0-16.1.2. Shortly after Google Project Zero security researcher Ian Beer reported CVE-2022-46689 to Apple late last year, security researcher Zhowei Zhang created a rough draft of a bug that developers now actively exploit to make operating system modifications that ordinarily wouldn’t be possible without jailbreaking.
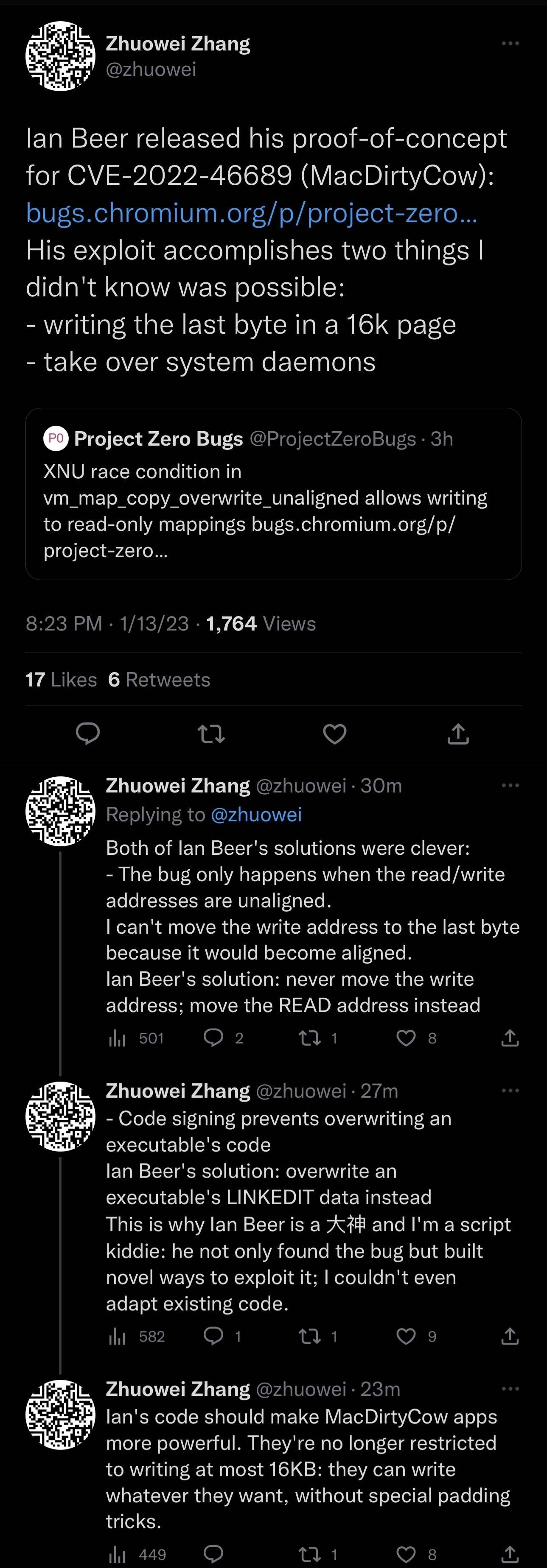
But as Zhang points out late Friday evening, Beer has officially published a detailed write-up with a proof of concept (PoC) about his bug for the world to see, and the write-up reveals how the bug appears more capable than originally thought…
According to Zhang, Beer’s PoC accomplishes at least two major feats that even Zhang’s PoC does not. For example, Beer can write to the last byte in a 16k page and take over system daemons, among other things.
In closing comments, Zhang added that Beer’s PoC would likely make MacDirtyCow-based apps and their modifications more powerful. Since they’re no longer restricted by the 16KB limit, those apps would be able to write essentially whatever they want without any kind of padding tricks that are currently being used.
One thing that obviously doesn’t change is that MacDirtyCow-based add-ons still revert after a device reboot. This has to do with the fact that modifications happen in the device’s memory, which is volatile and loses its contents upon being powered off. Even Beer’s implementation doesn’t circumvent this fact.
While MacDirtyCow add-ons are a far cry from a full-fledged or even rootless jailbreak experience, it’s worth noting that they’ve offered at least some refuge for users who enjoy customization as the mainstream continues to wait for a jailbreak. Jailbreak developers have repeatedly reiterated just how challenging it is to break into iOS & iPadOS after Apple’s latest security mitigations, which is the reason for the long wait.
This isn’t Beer’s first appearance in the iPhone hacking realm, and it probably won’t be his last. He is a talented individual who has proven his capabilities time and time again. Many of this exploits have went on to make jailbreaks for previous firmware versions, however mere tfp0 exploits aren’t enough to create a jailbreak these days as Apple has added so many additional roadblocks for jailbreak developers to overcome.
Those interested in seeing what Ian Beer had to say about the MacDirtyCow bug and viewing the PoC can head over to his blog post.
Are you excited to see what becomes of MacDirtyCow-based add-ons and their capabilities following Ian Beer’s full and comprehensive write-up? Discuss in the comments section down below.