Those searching for the next interesting way to customize their iPhone may enjoy the new TrollLock Reborn add-on based on the MacDirtyCow hack by iOS developers @haxi0sm and @dedbeddedbed.
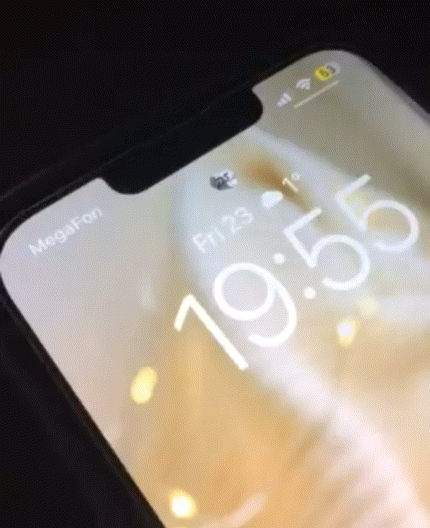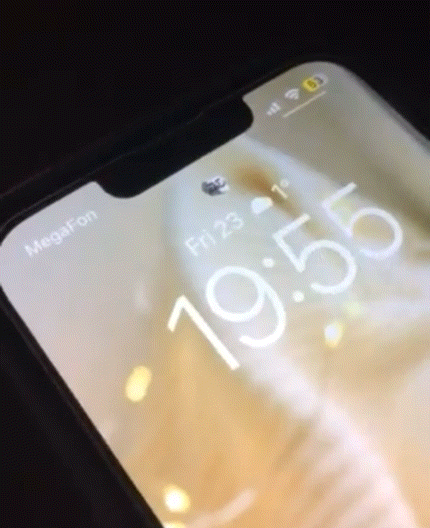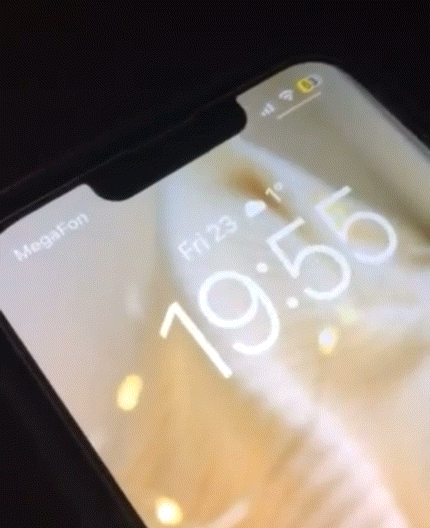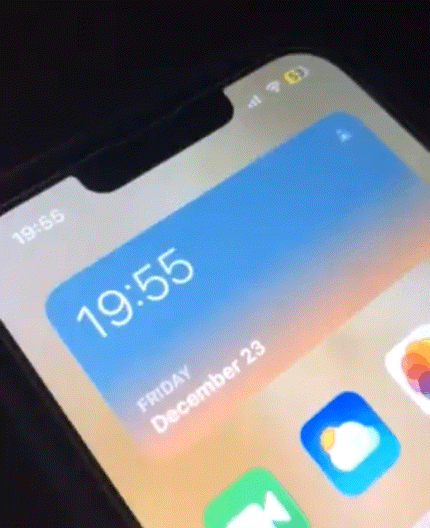
This simple add-on replaces the Lock Screen’s Face ID padlock glyph on notched handsets with an animated troll face that begins to show its smile as your Face ID system recognizes your face.
An example of the animation appears in the GIF embedded above, and it’s quite smooth.
Despite the name “TrollLock” Reborn, it’s important to note that this add-on is not intended for TrollStore. Instead, it can be sideloaded with a utility such as AltStore or Sideloadly (even on devices running iOS 16.1.2 or below). Troll merely related to the troll face in the animation.
For those wondering, TrollLock appears to take advantage of CVE-2022-46689, also known as MacDirtyCow. According to a comment by TrollStore developer opa334 on /r/jailbreak, MacDirtyCow is a live hack that can be exploited to write to all files that a sandboxed app can read. It’s worth noting however that these changes aren’t permanent; they typically reset after a reboot because information will be written to cached data in the device’s memory.
With that in mind, users will likely need to re-configure TrollLock Reborn in between reboots to reinitialize the customization into their device’s memory. Still, a minor inconvenience given that this is possible without a jailbreak and on iOS & iPadOS 16 devices up to and including iOS & iPadOS 16.1.2. MacDirtyCow is unfortunately patched in iOS & iPadOS 16.2, so TrollLock won’t work on devices running the newer firmware.
If you’re interested in giving TrollLock a try, then you can head over to the project’s official GitHub page.
Do you plan to give your notched handset a troll face-inspired Face ID unlocking animation with TrollLock? Let us know in the comments section down below!