The FBI has vehemently opposed Advanced Data Protection, a new feature in iOS 16.2 that encrypts your iPhone backups in iCloud with end-to-end encryption.
- What’s happening? The FBI isn’t thrilled about the new encrypted iCloud backup option in iOS 16.2, saying it needs “lawful access by design.”
- Why care? As the battle for privacy and encryption continues, Advanced Data Protection in iOS 16.2 is a potential setback for law enforcement because it means Apple no longer holds the encryption keys to access iPhone backups in iCloud.
- What to do? Stay tuned, iOS 16.2 is releasing next week!
Encrypted iCloud backups ruffle the FBI’s feathers
The new Advanced Data Protection feature brings end-to-end encryption to nine more iCloud services like iCloud Backup, Notes and Photos, raising the number of iCloud features that are protected by end-to-end encryption from 14 to 23.
As a result, law enforcement can no longer leverage search warrants to obtain peoples’ photos, messages and other items that are backed up to iCloud when Settings → [your_name] → iCloud → iCloud Backup is toggled on.
The FBI wants “lawful access by design.”

Predictably, the FBI is vehemently opposing Advanced Data Protection because the organization believes it throws a wrench in its intelligence efforts while at the same time giving bad actors an upper hand.
In a statement to The Washington Post, the FBI not only called the move “deeply concerning” but demanded “lawful access by design” (read: backdoor).
This hinders our ability to protect the American people from criminal acts ranging from cyber-attacks and violence against children to drug trafficking, organized crime and terrorism. In this age of cybersecurity and demands for ‘security by design,’ the FBI and law enforcement partners need ‘lawful access by design.'”
The FBI’s stance on encryption is concerning

We still remember a standoff between Apple and the FBI several years ago, when government spooks tried scare tactics by arguing that someone is going to get abducted or something worse and the FBI won’t be able to do anything about it because bad Apple won’t build a backdoor into iOS.
But as it turns out, that was just a posture for public display because the FBI had legal grounds to obtain backups via search warrants. Because the encryption keys were stored on Apple’s servers, Apple had no choice but comply with such requests.
Without means to decrypt someone’s backup, however, the FBI has lost the ability to compel Apple to hand over unencrypted backups to it. What bugs us the most is the fact that the FBI continues to view enhanced privacy as concerning.
Privacy groups applaud Apple’s move
The Electronic Frontier Foundation called the feature a “victory for user privacy.”
We applaud Apple for listening to experts, child advocates and users who want to protect their most sensitive data. Encryption is one of the most important tools we have for maintaining privacy and security online. That’s why we included the demand that Apple let users encrypt iCloud backups in the Fix It Already campaign that we launched in 2019.
Advanced Data Protection is off by default
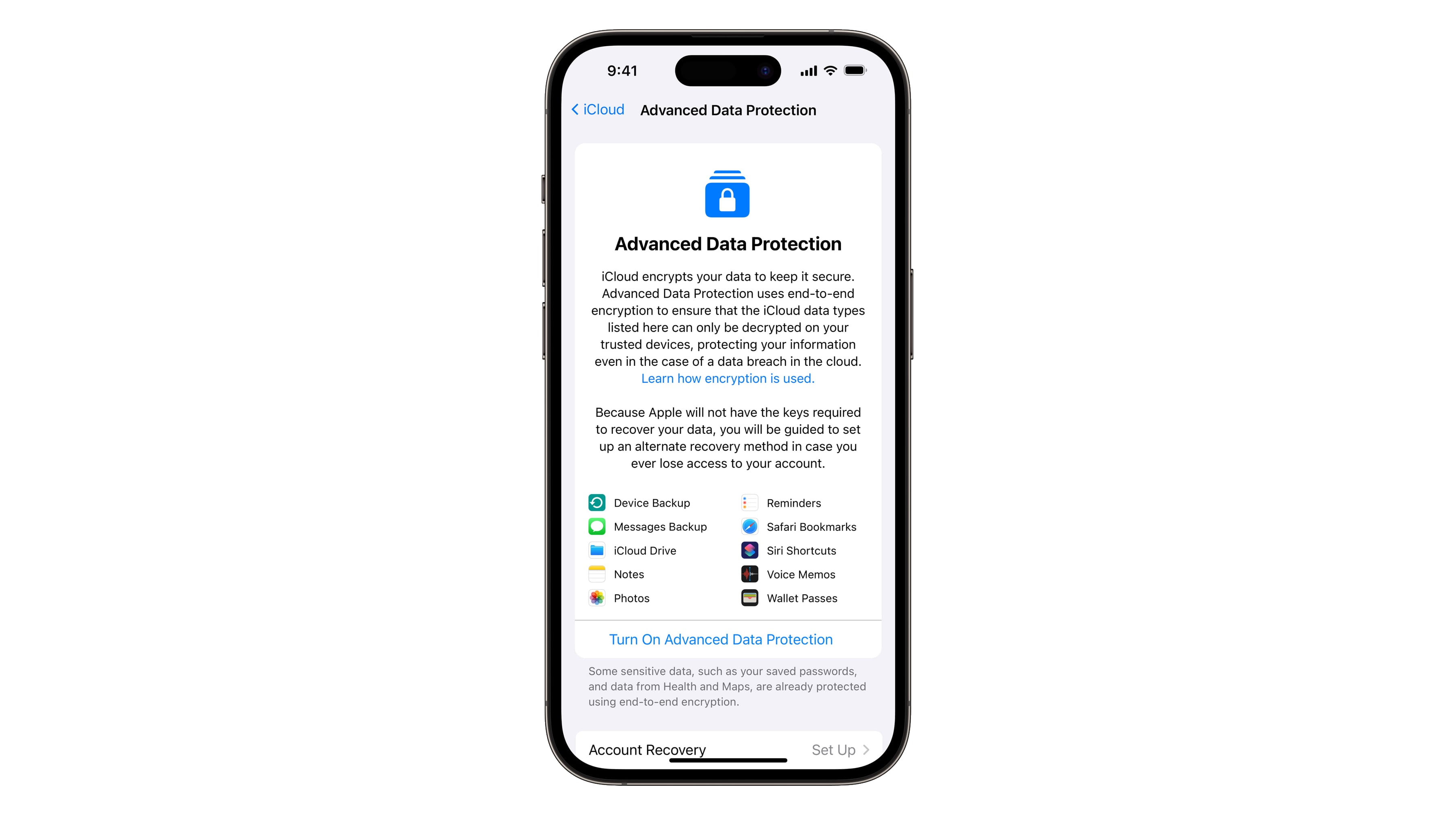
One potential issue is that Advanced Data Protection is off by default, requiring you to manually opt-in. Many people won’t bother to turn this feature on, especially novice users who aren’t geeks. That fact wasn’t lost on the Surveillance Technology Oversight Project, which says defaulting to off will “leave most users vulnerable.”
For years, Apple has touted its privacy record while leaving its users vulnerable, particularly to police surveillance. Much of the data users store on iCloud is just a court order away from becoming a policing tool. With these changes, Apple will keep up with the privacy best practices that other companies have followed for years. But it’s disappointing that users have to opt-in to many of these new protections, leaving the vast majority at risk.
How end-to-end encryption protects iCloud backups
End-to-end encryption protects data on the device, in transit and on servers to make it unreadable to anyone but you. No one—and that goes for law enforcement—can read encrypted data without keys that are stored on your device and never leave it.
Before this change, Apple used to store encryption keys on servers. That’s why the company had been able to comply with search warrants and decrypt a person’s photos, messages and other data stored as part of their iCloud device backup.
How to encrypt iPhone backups in iCloud

Upon updating your iPhone to iOS 16.2, you can turn this feature off manually in Settings → [your_name] → iCloud → Advanced Data Protection. As part of the setup process for the feature, you’ll need to define at least one recovery contact or create a recovery key. Read: How to set up emergency contacts on iPhone
Again, with Advanced Data Protection turned on Apple no longer has the means to decrypt your backups. But you’ll need to store your recovery key in a safe place and be sure to have at least one recovery contact added. Otherwise, losing the recovery key/contact will stop you from accessing your backups and other iCloud data.
The whole reason why Apple used to gold these encryption keys was to help you with recovery should you ever lose access to your iCloud account.
When will Advanced Data Protection launch?
Advanced Data Protection will be available across the iPhone, iPad and Mac devices with iOS 16.2, iPadOS 16.2 and macOS 13.1 updates dropping on December 13 or 14.
The only iCloud categories that Advanced Data Protection doesn’t protect with end-to-end encryption are Mail, Contacts and Calendar due to the need for these services to interoperate with the global email, contacts and calendar systems.
Read Apple’s support document if you’re interested to read about end-to-end encryption on iCloud in detail. For a deep technical dive into Advanced Data Protection, check out the Apple Platform Security Guide on the web.