Security researcher @_simo36 turned quite a few heads with a Tweet shared on Friday that appears to contain a proof of concept (PoC) for an exploit chain called WeightBufs that achieves kernel memory read and write capabilities on some versions of iOS & iPadOS 15 and macOS 12.
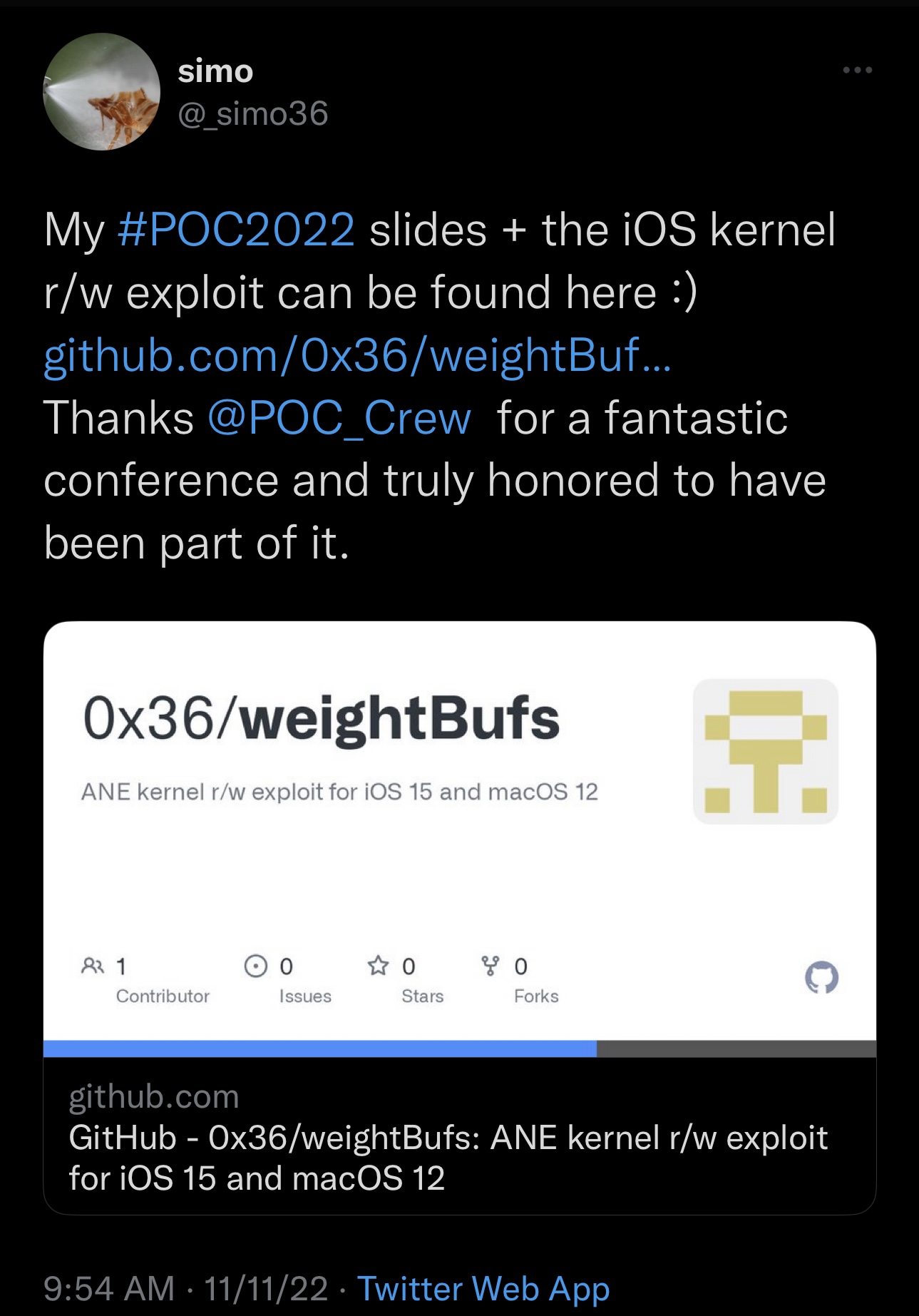
In the Tweet, @_simo36 points to a GutHub page that contains not only all the information about the exploit, but also the slides for the presentation they gave at POC2022.
As it would appear, the exploit itself supports all versions of iOS & iPadOS 15 on Neural Engine-equipped devices (A11 and newer) just shy of iOS & iPadOS 16; but iOS & iPadOS 15.6 patch the sandbox escape, which breaks the exploit chain used to achieve the WeightBufs hack. With that in mind, the full exploit chain is only currently viable on iOS & iPadOS 15.0-15.5 and macOS 12.0-12.4.
The problem above underscores one of the core issues impacting jailbreaking today, which is how techniques have become more important than the kernel exploits themselves. No single kernel exploit will make a jailbreak on modern iOS or iPadOS firmware since Apple continues to ratchet up iPhone and iPad security. Because of this, jailbreak developers need additional resources such as bypasses and sandbox escapes just to achieve one. The logic behind navigating all these mechanisms is what constitutes a technique.
At least four different vulnerabilities that have already been reported to Apple are used in @_simo36’s exploit chain, including the following:
- CVE-2022-32845: aned signature check bypass for model.hwx.
- CVE-2022-32948: DeCxt::FileIndexToWeight() OOB Read due to lack of array index validation.
- CVE-2022-42805: ZinComputeProgramUpdateMutables() potential arbitrary read due to integer overflow issue
- CVE-2022-32899: DeCxt::RasterizeScaleBiasData() Buffer underflow due to integer overflow issue.
Currently, @_simo36 says they’ve tested their exploit chain successfully on the following device and firmware combinations:
- iPhone 12 Pro (iPhone 13,3) running iOS 15.5
- iPad Pro (iPad 8,10) running iPadOS 15.5
- iPhone 11 Pro (iPhone 12,3) running iOS 15.4.1
- MacBook Air (10,1 with M1 chip) running macOS 12.4
So the searing question we know you’re all asking is, “can this be used for a jailbreak?” And the simple answer to that question would be no because it’s only one piece of a greater puzzle and a lot more work would be required to build a jailbreak and get it up and running on end user devices.
Still, the proof of concept is a great example of masterful hacking, and we can only hope that it helps to complete the puzzle faster as several jailbreak teams work in the background to develop jailbreaks for iOS & iPadOS 15.
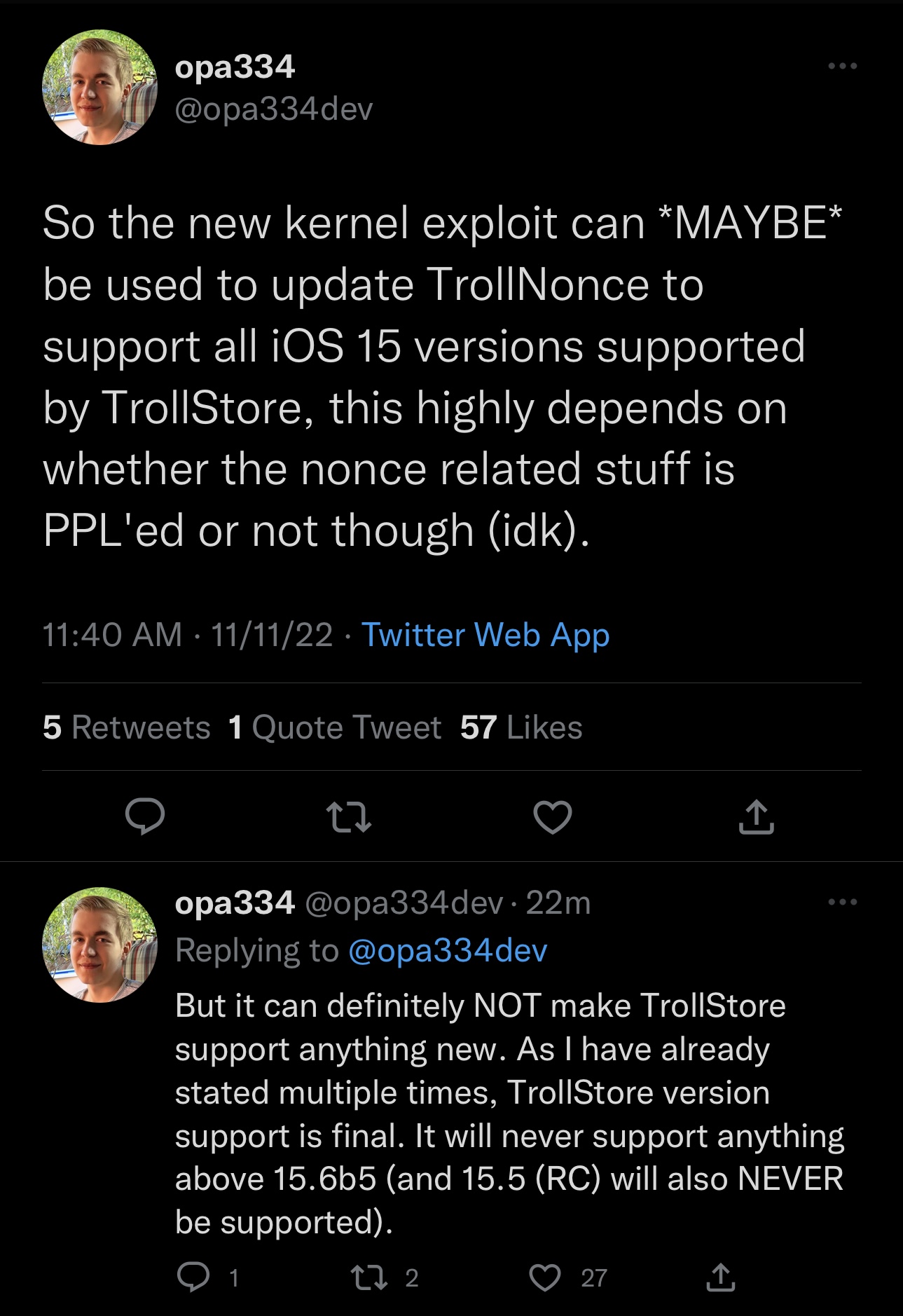
In fact, some developers are already looking into ways that it could be incorporated into their projects, such as TrollStore developer @opa334, who might be able to use it to enhance TrollNonce. But it’s worth noting that TrollStore won’t ever support anything newer than the firmware it already supports:
Are you excited to see what becomes of the new exploit chain? Let us know in the comments section down below.