Apple on Monday released the iOS & iPadOS 15.2 software update for compatible iPhones and iPads. Based on the security content notes for this release, it’s evident that Apple ‘s security team spent some extra time patching a relatively high number of security vulnerabilities.
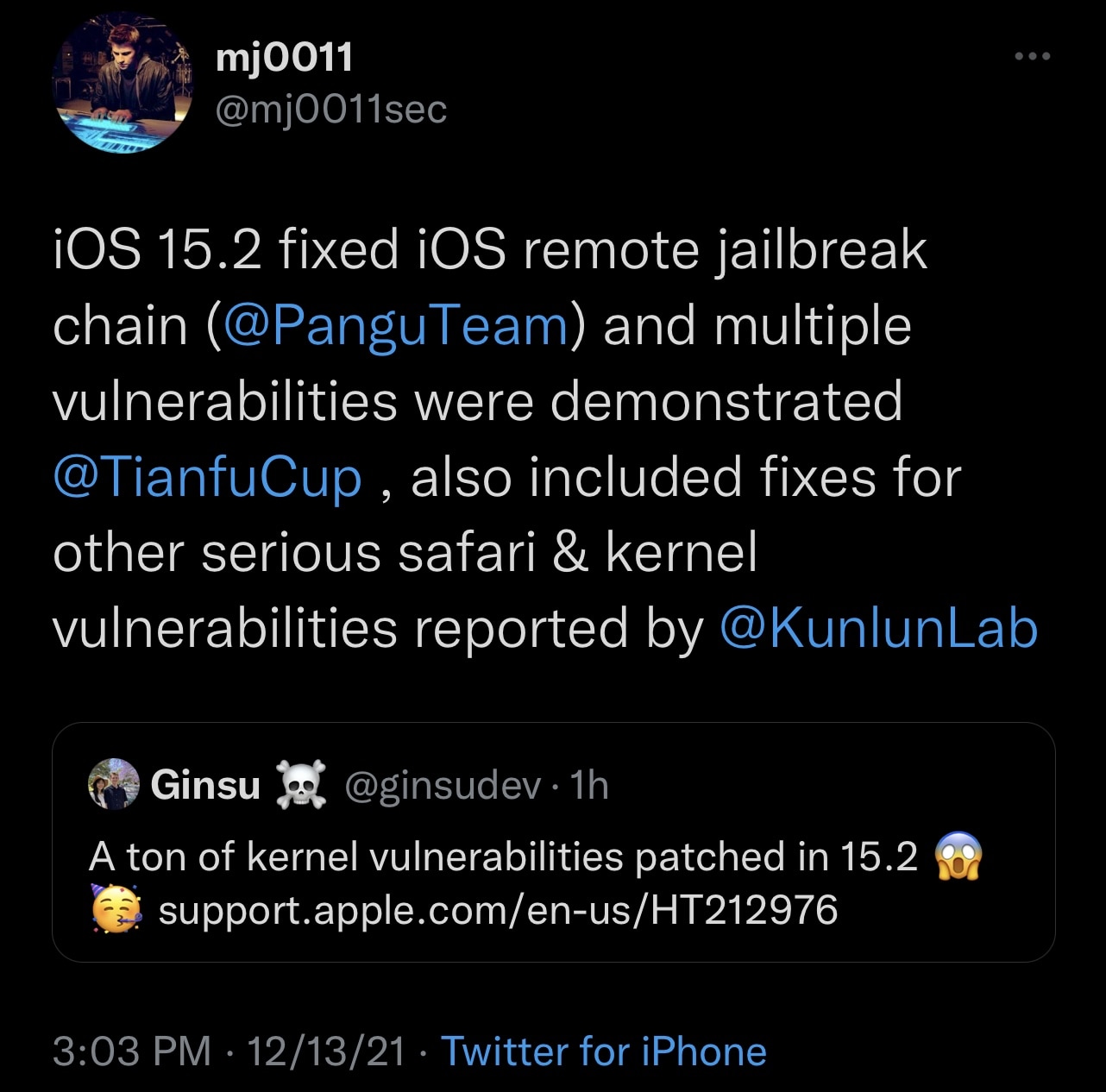
In fact, according to a Tweet shared just this afternoon by Kunlun Lab CEO @mj0011sec, it appears that iOS and iPadOS 15.2 fix a chain of exploits that were originally harnessed by the Pangu Team at TianfuCup 2021.
If your memory needs jogging, then we can help with that. The Pangu Team used those exploits to demonstrate a working remote jailbreak for the iPhone 13 Pro running iOS 15 on the first day of the hacking event. The feat was not only impressive given the timeline of Apple’s new product launch, but it also fetched the Pangu Team a juicy $330,000 cash prize.
The security notes for iOS and iPadOS 15.2 cite the Pangu Team, or individual members of the Pangu Team, at least six different times in the following CVEs. The description for each CVE below describes circumstances in which an attacker could achieve arbitrary code execution on Apple’s mobile platform(s):
- IOMobileFrameBuffer: CVE-2021-30983
- IOMobileFrameBuffer: CVE-2021-30985
- IOMobileFrameBuffer: CVE-2021-30991
- Kernel: CVE-2021-30927
- Kernel: CVE-2021-30980
- WebKit: CVE-2021-30952
Many jailbreakers remember the Pangu Team because they released a jailbreak to the general public back when iOS 9 reigned supreme. Since then, the team’s core values shifted from releasing jailbreaks to that of private research and responsible disclosure. In essence, that’s why they don’t seem to release jailbreaks to the general public anymore.
While it would be considered unfortunate to avid jailbreakers that Apple has patched some potentially useful exploits for iOS and iPadOS 15 in the new 15.2 release, it’s good news for non-jailbreakers who’ve updated their device(s) because this means their handsets are now more secure from potential malicious attacks than they were before today.
There is still no public jailbreak available for iOS or iPadOS 15 at the time of this writing, nor is there any ETA for one. Obviously, those ambitious about jailbreaking iOS 15 should steer clear of today’s update and stay on the lowest possible firmware to increase their odds of jailbreak eligibility when a jailbreak does surface.
What are your thoughts on all the security patches integrated into the new iOS & iPadOS 15.2 software update? Be sure to let us know in the comments section down below.