
It was only a few days ago that a kernel-level jailbreak detection bypass had been released to the general public. Dubbed FlyJB by @XsF1re, the project was quickly taken down after the developer lost confidence in his work. But much of his efforts remained open source, permitting future projects to draw inspiration from it.
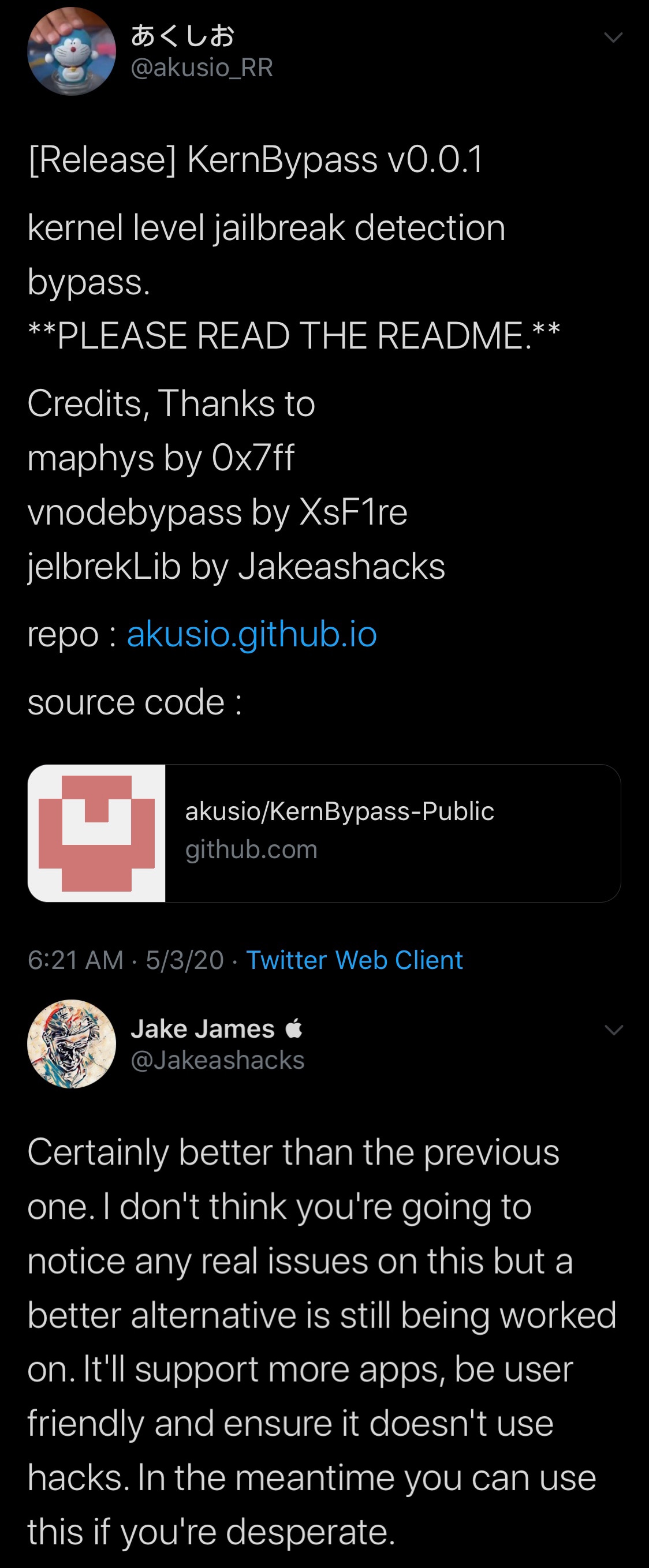
Now, a second kernel-level jailbreak detection bypass called KernBypass by has been released, this time by Twitter user @akusio_RR. The project credits @XsF1re for vnodebypass, hacker Jake James for jelbrekLib, and @0x7ff for maphys. But what does all this mean?
Shortly after the KernBypass project was announced this morning on Twitter, hacker Jake James got to work in studying the open source release to discern its differences from FlyJB. Interestingly, James Tweeted that this one is “better than the previous one,” albeit not as good as an alternative that James appears to be working on for a future release:
So, what is a jailbreak detection bypass? It’s essentially a means of tricking App Store apps into thinking you aren’t jailbroken. These can come in the form of jailbreak tweaks, but it can be easy for an app update to break it. A kernel-level jailbreak detection bypass like KernBypass, on the other hand, works at a higher chain of software command in the kernel level and, in theory, shouldn’t be detectable by an app even after it receives updates.
Kernel level jailbreak detection bypasses are highly sought after by the jailbreak community because many apps are starting to adopt jailbreak detection that either bars the user from using said app or bans the user’s account for breaking its terms of service with third-party hacks. Obviously, each of these are inconvenient.
Whether the app is a game you enjoy playing or a banking app that you absolutely must use, jailbreak detection often rides a careful self-righteous line that defines Lady Justice. On one side, users should have the freedom to do what they want with their devices, and on the other, app developers must remain mindful about user security, especially when performing sensitive banking activities on a hacked device.
Ultimately, this choice should come down to the user and the risks they decide to take on, and this is why jailbreak detection bypasses are such a big deal. Moreover, one that can evade detection by operating at the kernel level is an even bigger deal.
While hacks like these are used entirely at your own risk with no endorsement implied by iDownloadBlog, those who feel comfortable putting their trust in a third-party hack to evade account bans and jailbreak restrictions in apps can follow these instructions via /r/jailbreak to install KernBypass:
This is kernel level tweak. No warranty is provided, use it at your own risk.
How to use:
1) Download and install deb.
2) In terminal, run su and type your password (alpine if you haven’t change it).
3) Run changerootfs & (don’t forget “&”).
4) Run disown %1
5) Done. the changerootfs is now a daemon.
6) After changerootfs launch, open Preferences > KernBypass > select enable application.
– For unc0ver users please delete the app you are trying to bypass and install it again after completing the steps above.
– If you get the Segmentation fault error, please create the “/var/MobileSoftwareUpdate/mnt1” folder
Note: if at any time you want to uninstall the kernel-level jailbreak bypass, you can merely uninstall it via your preferred package manager. You will then need to reboot, not respring, your device for the changes to take effect.
According to James, users are advised to use his kernel-level jailbreak bypass when it gets released, but he also notes that users could install KernBypass in the interim since his bypass isn’t yet ready for the public.
For those interested in learning more about it, KernBypass is fully open source on the developer’s GitHub page.
It will be interesting to see how these kernel-level jailbreak bypasses shake up the realm of jailbreak detection. After all, this seems to be an increasingly annoying issue for jailbreakers, especially those that enjoy playing popular titles like Call of Duty mobile, Fortnite, Pokémon GO, and PUBG among others. Even commonly-used apps that aren’t games seem to be adopting jailbreak detection more frequently than in the past.
Do you have any plans to try these kernel-level jailbreak detection bypasses? Discuss your stance in the comments section below.