The iOS 12.1 update, which released yesterday, has fixed an underreported yet dangerous Lock screen vulnerability which permitted anyone in possession of your iPhone or iPad to view your photos and—worse—use the Share function to send them to anyone.
According to Apple’s support document detailing iOS 12.1’s security content, the bug allowed a local attacker to get to your photos from the Lock screen.
“A Lock screen issue allowed access to the share function on a locked device,” reads the document. “This issue was addressed by restricting options offered on a locked device.”
TUTORIAL: How to protect missed calls on your Lock screen
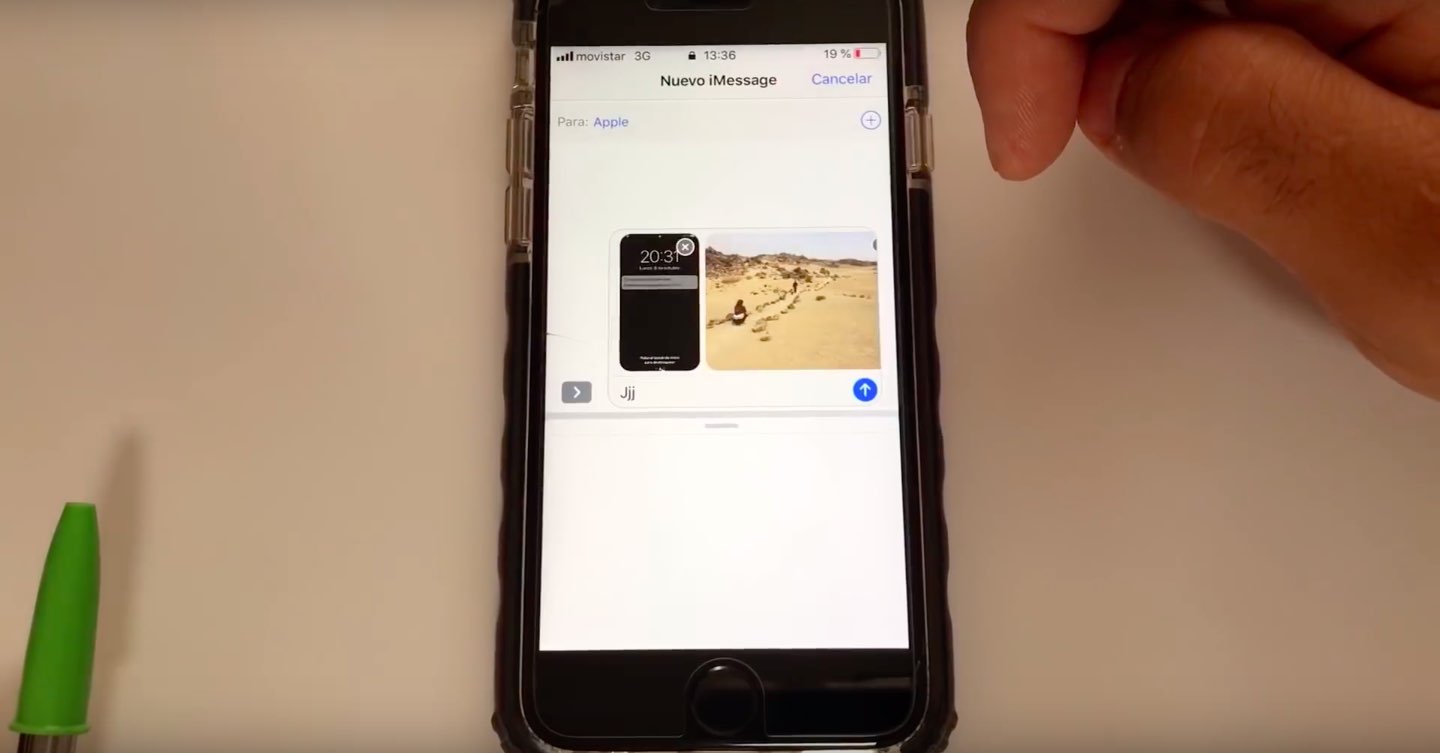
Enthusiast iOS hacker Jose Rodriguez, who in the past exposed a pair of other Lock screen vulnerabilities, was first to document this problematic Lock screen behavior. Basically, the vulnerability uses Reply With Message on a locked device to access your Photos library.
Check out Jose’s proof-of-concept video posted on YouTube earlier this month.
As the video demonstrates vividly, an attacker first needs to learn about your phone number by asking Siri. Taking it from there, they’d need to place a call to a target device, then hit the Message option on the Lock screen before choose the option labeled Custom.
AppleInsider has the full rundown of the remaining steps:
After entering a few random letters in the text box, he once again invokes Siri to activate VoiceOver. Returning to Messages, Rodriguez taps on the camera icon and, while invoking Siri with iPhone’s side button, double taps the screen to trigger what appears to be a system-level conflict. While this particular step must be performed with a certain level of precision, an attacker can repeat the process multiple times until the desired effect is achieved.
A black screen is displayed when the bug condition is met. As Rodriguez demonstrates, however, VoiceOver’s text selection tool is able to access ‘hidden’ UI options through typical navigation gestures. Swiping left on the blank screen takes Rodriguez to ‘Photo Library’ which, when selected by double tapping, returns him to the Messages app.
The app drawer below the text input box is blank, but leaves the app card collapse button active. Tapping on said element—a small handlebar—and swiping right grants VoiceOver unseen access to a target device’s photos, details of which are read aloud by the system.
Swiping through the photo library, which is seemingly obscured by the Messages UI, and double tapping on a given photo inserts the image into the Messages text box. Multiple photos can be inserted, viewed and sent to an attacker’s device in this manner.
Despite more than a dozen steps required to replicate the issue, an informed rogue user could easily offload your photos onto another device provided they’re in possession of both their own personal phone and your iPhone at the time of attack.
Current iPhone models, including the latest iPhone XS and iPhone XR models, are susceptible to this vulnerability as well. The issue is present in both the iOS 12.0 and iOS 12.1 updates.
Reply With Message, required for this bypass to work, is on by default in iOS 12.
To restrict Reply With Message and other features such as Siri and Notification or Control Center, visit the Face ID, Touch ID or Passcode settings on your iPhone or iPad.
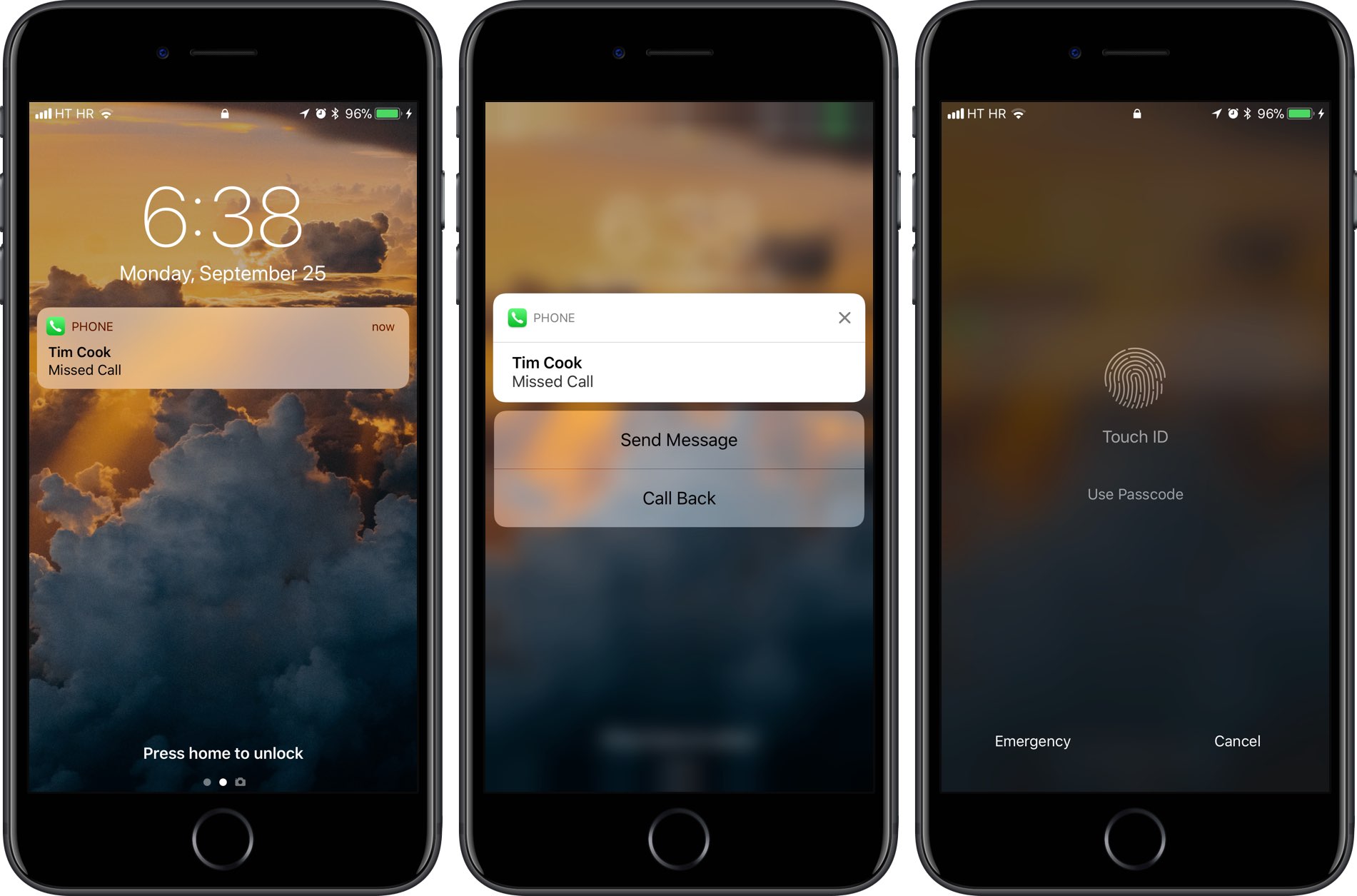
You’re wholeheartedly recommended to also disable Siri on the Lock screen.
An unattended device that allows Siri on the Lock screen is prone to these kinds of attacks. Preventing Siri on the Lock screen also prevents tricks where someone could ask your Siri “Who I am?” (or request she make a call to your own phone number).
To protect yourself, go to Settings → Siri & Search and turn off Allow Siri When Locked.
There’s another iPhone lock screen bypass out and once again it needs Siri available – so locking up your lock screen is once again a smart move… pic.twitter.com/eVOzB6DjEJ
— Naked Security (@NakedSecurity) October 16, 2018
Using Siri to activate VoiceOver to perform certain tasks on a locked device is what makes these kinds of attacks that expose your personal information possible in the first place.
Did you know about this particular Lock screen vulnerability?
Let us know by leaving a comment below.