
It’s a number that’s bound to raise some eyebrows: 220,000 iCloud accounts breached in what is being called a backdoor attack made possible by a malicious jailbreak tweak.
This leak, which was brought to our attention by /r/jailbreak, was reported by a Chinese online vulnerability reporting platform called WooYun. It’s an information security platform where security researchers report vulnerabilities and vendors give feedback. WooYun is a legit site, and it has reported thousands of security related issues in this month alone.
On a post on its website, WooYun details the nature of this particular attack, stating that 220,000 accounts have been compromised as a result of a malicious jailbreak tweak or plug-in. It also states that WooYun has notified vendors—presumably Apple—and are awaiting processing.
It’s sure to make any jailbroken iPhone user take note, but before you get too alarmed, understand that this hack has nothing to do with Apple’s security, and that there appears to be special circumstances in the case of this breach.
As we’ve seen in the not so distant past, the breach of iCloud credentials can have negative results, because if two factor authentication is not enabled for an account, then a person in possession of leaked credentials can access personal data, including emails and photos with relative ease.
This, indeed sounds horrible, as nearly a quarter of a million accounts were said to be compromised, and we know that not all of those accounts took the sound advice of enabling 2FA.
Who’s affected?
When you start to break down the facts, it appears that this breach has had an extremely limited reach, if any, on those who jailbreak their own devices. That rules out most of those who reside outside of China and surrounding areas.
The report states that these accounts were compromised as a result of a malicious jailbreak release. By just doing some mental math, it seems highly unlikely that any jailbreak tweak would receive the amount of penetration required to affect a quarter of a million users, let alone a malicious tweak posted on some shady third-party repo. So the likelihood that this attack is the result of any of the tweaks that we use in the community is very slim.
With such a large number of compromised devices, it would seem that such an attack is the result of a more organized and methodical method of entry—a preinstalled backdoor, if you will.
A fellow redditor, ZippyDan, user suggested this conjecture:
In Asian countries, it is very common for people to buy phones, new or used, from technology markets. At those markets are lots of competing stalls selling phones, and jailbreaking your phone and selling it to you preinstalled with lots of jailbroken / pirated apps is part of their service.
That is part of why jailbreaking / Pangu is so popular in Asia / China. There are entire markets of Chinese-only programs and apps that we are not really exposed to here on this English- / Western-dominated subreddit.
We aren’t really used to that kind of service in the west. Mostly you just buy your phone and get it brand new and virgin from the box and you’re on your own. Part of this is because technical know-how is much more costly in the US / West, and part is because cell-phone shops are much more scattered and there is much less competition to provide these kinds of services. In an Asian technology market, you might have 30 – 100 different shops all competing for your business in an area the size of a Walmart.
Anyway, my point is that if one of these “shady” apps is something that was somewhat common for these 3rd-party sellers to install, then this stat wouldn’t be that surprising. It doesn’t take 220,000 people with personal tech know-how to jailbreak and download a tweak: it just takes 220,000 people buying from a few hundred / thousand technology boutique shops that preload the software.
To me, this makes a lot more sense than having some jailbreak tweak hosted on some shady third party repo that just happened to get popular enough to convince a quarter of a million savvy jailbreakers to put themselves at risk.
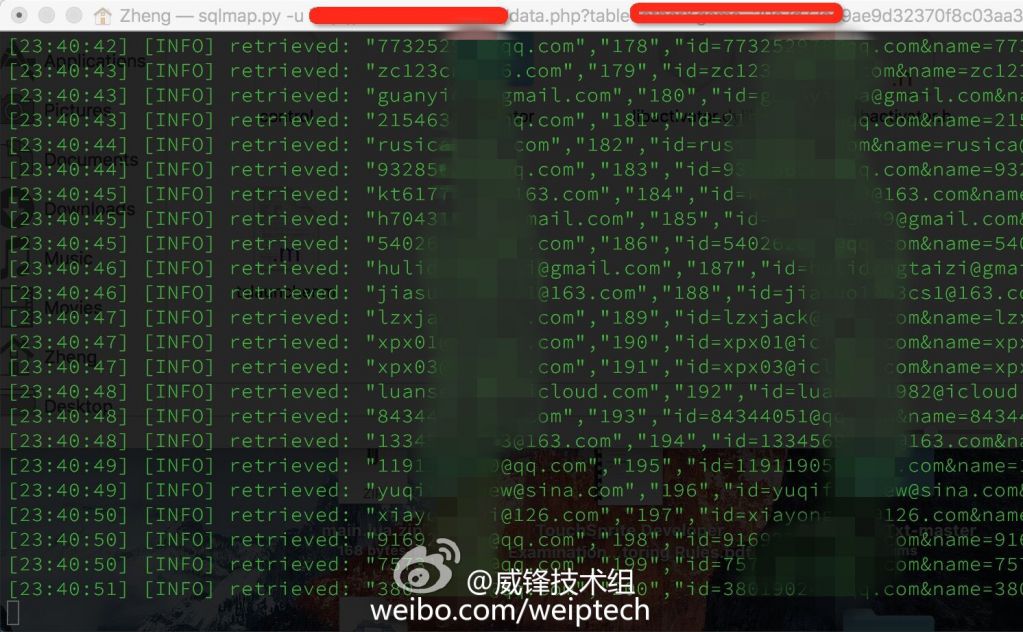
A screenshots showing some of the leaked credentials, which contain Chinese names
Yes, there are shady tweaks that make it through the cracks, to be sure. Yes, there are malicious third-party repos that host cracked software and likely host malicious files as well. Yes, jailbreakers do inherently open themselves up to more risk than those who don’t jailbreak.
That’s all true, but it’s also highly unlikely that any of that was the case in this attack, if the breach is indeed the result of a malicious backdoor, as noted by WooYun.
Protect thyself
That’s not to say that jailbreakers in general can’t take something away from this. We all can strive to do better when it comes to security. Here are some of the things that we should all be doing to help protect ourselves and others:
- Enable 2 Factor Authentication
- Don’t add shady third party repos to Cydia
- Don’t pirate tweaks or apps
- Don’t install tweaks outside of Cydia
These may sound like basic things, but by following the above protocol, a jailbreaker can mitigate much of the risk associated with jailbreaking.
What do you think about this report? Does it move your needle in any particular direction as far as your opinion of jailbreaking goes? Sound off down below with your thoughts on the matter.
Update: I have it on good authority that this has affected certain Chinese users only, and is the result of a jailbreak tweak downloaded by the user, not preinstalled as conjectured above. More details to come soon.