Taking advantage of a primitive Windows technique relying on automatically-running macros embedded in Microsoft Word documents, a new type of Mac malware attack has been discovered recently. As first noted in a research compiled by Objective-See, the technique used may be crude but once an unsuspecting user opens an infected Word document and chooses to run the macros, the malware installs itself silently on the target Mac and immediately attempts to download a hazardous payload.
Malware
Malwarebytes reports first case of Mac malware for 2017, points out antiquated tactics
Security software development firm Malwarebytes has just exposed what could be the first known case of Mac malware for the year of 2017.
It appears to be a highly antiquated piece of malware. In other words, it’s not super advanced and it’s using methods to infect machines that are so well-known that only a small number of unsuspecting users would even fall victim to it.
Apple just shot down an app that could detect iPhone malware
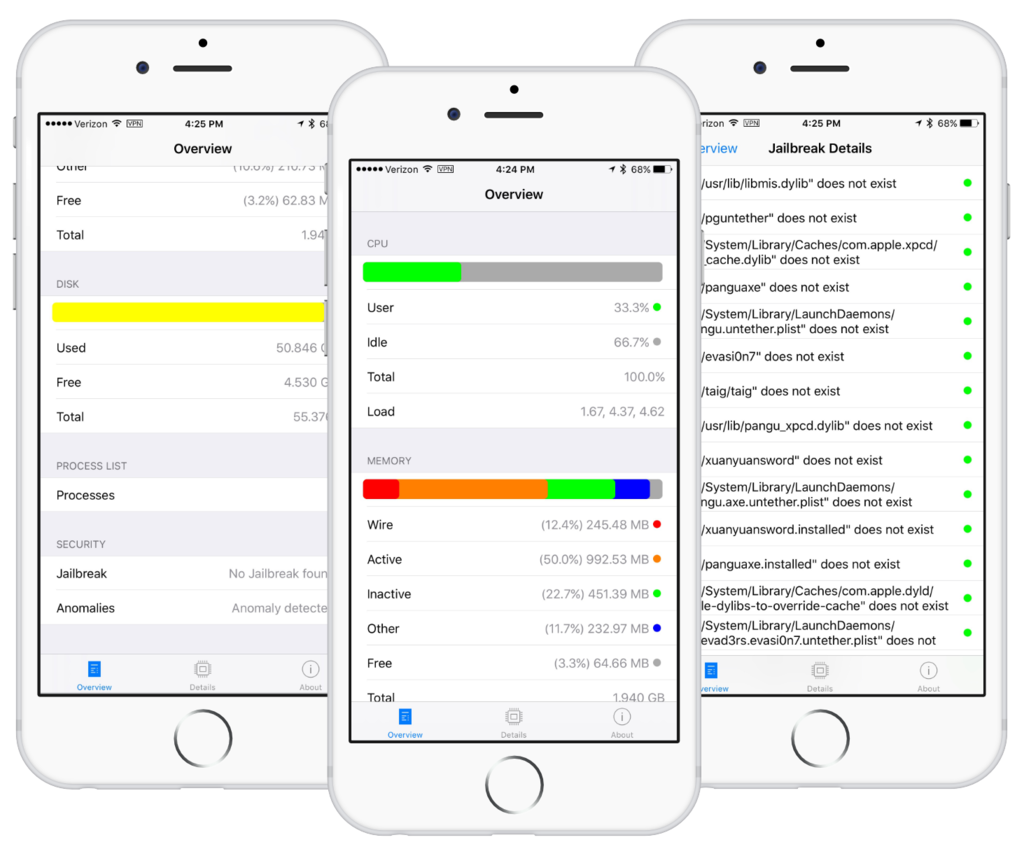
Stefan Esser’s iPhone app, called System and Security Info, can no longer be downloaded from the App Store, as first noted by The Next Web. Esser’s software let iPhone users know if their device had malware that could be used to spy on them, and could detect a jailbreak, too.
The app was removed from the App Store earlier this morning. Esser was basically told that detecting weaknesses in a user’s device could lead to “potentially inaccurate and misleading diagnostic functionality for iOS devices.”
A quick overview of the new System and Security Info app

Security has always been a top priority for Apple and its ecosystem, especially as of late. Tim Cook has made it clear that maintaining encryption and tight security protocols are here to stay. Users that are equally as concerned about protecting their personal information have had few options in actually monitoring their security however. A new app called System and Security Info from security firm SektionEins aims to help with that.
What you need to know about the AceDeceiver trojan that’s affecting some iOS devices

Stock, non-jailbroken iOS devices appear to be vulnerable to a new security threat; a trojan known as AceDeceiver, which can be installed on an iOS device without the user's knowledge and without the help of an enterprise certificate. Once installed, it will spread malware and unwanted software to the user's device.
AceDeceiver only seems to be affecting those located in China at this point in time, but because that could change on the fly, you need to know how to protect yourself so similar threats don't affect users across the globe in the future.
Phishing emails: what they are and how to report them

Emails are a popular way to keep in touch with people, be it friends, family, or co-workers, but often companies that you deal business with will send you the occasional promotional email if you signed up for subscriptions.
Sometimes, you get an email that you think is legit, and it turns out it's just a fake email pretending to be something it's not and it tries to get you to click on stuff or give up your personal information. These emails are malicious and they're known as phishing emails.
In this piece, we'll go over some of the things you can look for to tell if the emails you're getting are legitimate, or if they're a con artist trying to scam you of your personal information.
What you need to know about the KeRanger ransomware found in the Transmission app
Users of the popular open-source Transmission BitTorrent client for OS X were in for quite a surprise this weekend when it was discovered that certain installers for version 2.90 of the application were found to bundle unwanted ransomware with the installation, which is a type of malware that restricts file access across the system to cause trouble for the user.
Dubbed KeRanger by security research firm Palo Alto Networks, the malicious software will try to encrypt the user's system files in such a way as to tamper with the user's access to their Mac and then force the user to pay money to get their access back.
The makers of the Transmission app are now pushing immediate mandatory app updates to remove the ransomware and fix the problem for those that may have been affected, and it's recommended for all users, but how do you know if you're affected?
Using Gatekeeper to help secure your Mac

macOS comes with a security feature known as Gatekeeper, which can help prevent unwanted apps from launching on your Mac without your permission. It can also prevent potentially malicious apps from launching because it can be used to limit the kinds of apps that are allowed to open on your Mac.
In lieu of the recent Sparkle updater framework vulnerability having been uncovered in a variety of popular macOS apps, now is a great time to set up your Gatekeeper settings to prevent potential issues with malware on your Mac in the future.
In this tutorial, we'll be showing you how Gatekeeper works and how you can configure it to keep your Mac just as secure as you want it to be.
About OS X System Integrity Protection aka ‘Rootless’ and how to disable it
All Macs with OS X El Capitan installed on them have a new layer of security known as System Integrity Protection, which has been given the nickname 'Rootless' because it closes off a lot of system files to user access to prevent malicious programs and code from causing harmful changes to the core of OS X.
For some, the added security feels like a must for protection of your personal information, but for more advanced users who poke their noses into system files quite often, the feature can get in the way and prevent user modifications to the operating system. In this tutorial, we'll give you an overview of System Integrity Protection and show you a way to disable it.
What to know about ‘YiSpecter,’ new malware targeting all iOS devices

Just as all the hoopla surrounding the XcodeGhost attack appears to have died down, security researchers over at Palo Alto Networks have identified a new type of harmful malware.
Dubbed YiSpecter, it can install itself on both jailbroken and non-jailbroken iOS devices and is the first iOS malware that exploit Apple's private APIs to implement malicious functionalities.
Here's everything you need to know about this new type of attack, what Apple is saying about the malware and what you can do in order to protect your devices from becoming infected with YiSpecter.
Apple lists top 25 apps infected by XcodeGhost
Apple today refreshed its official XcodeGhost FAQ webpage, listing the top 25 iPhone and iPad apps on the App Store that contain the widely reported though mostly harmless XcodeGhost malware.
In addition to WeChat, one of the top messaging apps in the world, Rovio's Angry Birds 2 and China Unicom’s Customer Service app, most of the listed apps are distributed on the Chinese App Store only.
“If users have one of these apps, they should update the affected app which will fix the issue on the user’s device,” writes the company. “If the app is available on App Store, it has been updated, if it isn’t available it should be updated very soon.”
Apple has pulled many of the infected apps and said it's working closely with developers to get impacted apps back on the App Store.
Apple to offer local Xcode downloads in China, posts official XcodeGhost malware FAQ
The XcodeGhost malware couldn't have arrived at worst time for Apple as the company prepares to launch its iPhone 6s and iPhone 6s Plus tomorrow. The company has already removed the App Store apps infected by the malware, which has been found to inject its payload into apps compiled with compromised copies of Xcode that were distributed on non-Apple servers in China.
Wednesday, the Cupertino firm has confirmed plans to mitigate the threat by hosting local Xcode downloads within China. In addition, Apple has posted an XcodeGhost FAQ webpage on its Chinese website detailing the XcodeGhost malware and how customers might be affected by it.