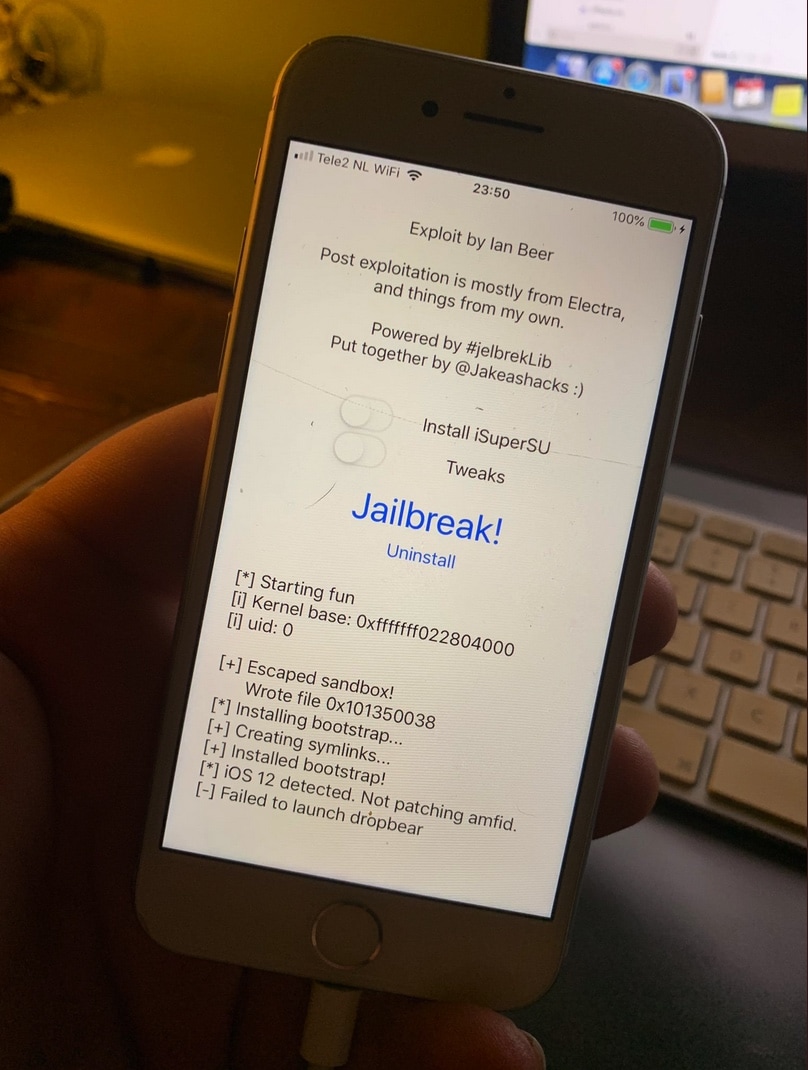
There’ve been so many kernel exploit releases for the iOS platform as of late that our heads are still spinning, but that’s pleasant news if you’re a jailbreak aficionado, because it gives our respected jailbreak tool developers more resources to work with.
The latest kernel exploit reportedly comes by way of hacker PsychoTea, and it has been named machswap. The exploit appears to be viable on all A7-A9 devices running iOS 11.0-12.1.2, which could make it a worthwhile candidate for modern jailbreak tools such as Electra or unc0ver.